HackTheBox Validation Writeup
Validation
Nmap Enumeration
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
# Nmap 7.95 scan initiated Mon May 26 18:09:14 2025 as: /usr/lib/nmap/nmap -sC -sV -vv -oN nmap 10.10.11.116
Nmap scan report for 10.10.11.116
Host is up, received echo-reply ttl 63 (0.068s latency).
Scanned at 2025-05-26 18:09:14 CDT for 15s
Not shown: 992 closed tcp ports (reset)
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 63 OpenSSH 8.2p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 d8:f5:ef:d2:d3:f9:8d:ad:c6:cf:24:85:94:26:ef:7a (RSA)
| 256 46:3d:6b:cb:a8:19:eb:6a:d0:68:86:94:86:73:e1:72 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBJ9LolyD5tnJ06EqjRR6bFX/7oOoTeFPw2TKsP1KCHJcsPSVfZIafOYEsWkaq67dsCvOdIZ8VQiNAKfnGiaBLOo=
| 256 70:32:d7:e3:77:c1:4a:cf:47:2a:de:e5:08:7a:f8:7a (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIJOP8cvEQVqCwuWYT06t/DEGxy6sNajp7CzuvfJzrCRZ
80/tcp open http syn-ack ttl 62 Apache httpd 2.4.48 ((Debian))
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.4.48 (Debian)
5000/tcp filtered upnp no-response
5001/tcp filtered commplex-link no-response
5002/tcp filtered rfe no-response
5003/tcp filtered filemaker no-response
5004/tcp filtered avt-profile-1 no-response
8080/tcp open http syn-ack ttl 63 nginx
|_http-title: 502 Bad Gateway
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Read data files from: /usr/share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Mon May 26 18:09:29 2025 -- 1 IP address (1 host up) scanned in 15.72 seconds
HTTP Port 80 Enumeration
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
┌──(wzwr㉿kali)-[~/Documents/htb/validation]
└─$ curl 10.10.11.116 -v
* Trying 10.10.11.116:80...
* Connected to 10.10.11.116 (10.10.11.116) port 80
> GET / HTTP/1.1
> Host: 10.10.11.116
> User-Agent: curl/8.8.0
> Accept: */*
>
* Request completely sent off
< HTTP/1.1 200 OK
< Date: Mon, 26 May 2025 14:53:00 GMT
< Server: Apache/2.4.48 (Debian)
< X-Powered-By: PHP/7.4.23
< Vary: Accept-Encoding
< Transfer-Encoding: chunked
< Content-Type: text/html; charset=UTF-8
<
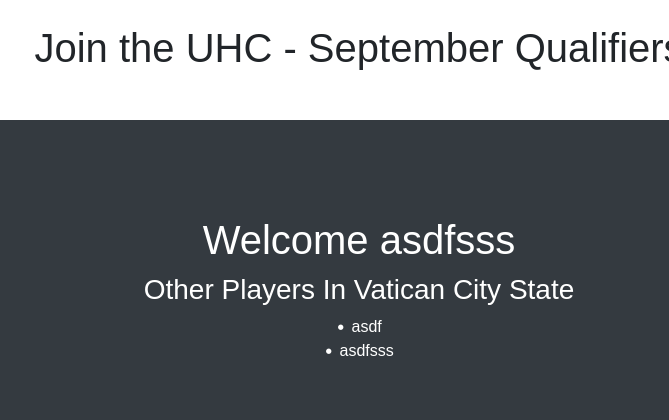
We can likely register with usernames. I’m thinking maybe SQL Injection or XSS could be useful here.
XSS
It looks like XSS is possible… but what else can we get from it?
Gobuster
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
┌──(wzwr㉿kali)-[~/Documents/htb/validation]
└─$ gobuster dir -u http://10.10.11.116/ -w /usr/share/wordlists/dirb/big.txt -x .php
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.11.116/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirb/big.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: php
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/.htaccess.php (Status: 403) [Size: 277]
/.htaccess (Status: 403) [Size: 277]
/.htpasswd (Status: 403) [Size: 277]
/.htpasswd.php (Status: 403) [Size: 277]
/account.php (Status: 200) [Size: 16]
/config.php (Status: 200) [Size: 0]
/css (Status: 301) [Size: 310] [--> http://10.10.11.116/css/]
/index.php (Status: 200) [Size: 16088]
/js (Status: 301) [Size: 309] [--> http://10.10.11.116/js/]
/server-status (Status: 403) [Size: 277]
Progress: 40938 / 40940 (100.00%)
===============================================================
Finished
===============================================================
Didn’t find anything interesting. I’m guessing there might be a SQL Injection vulnerability.
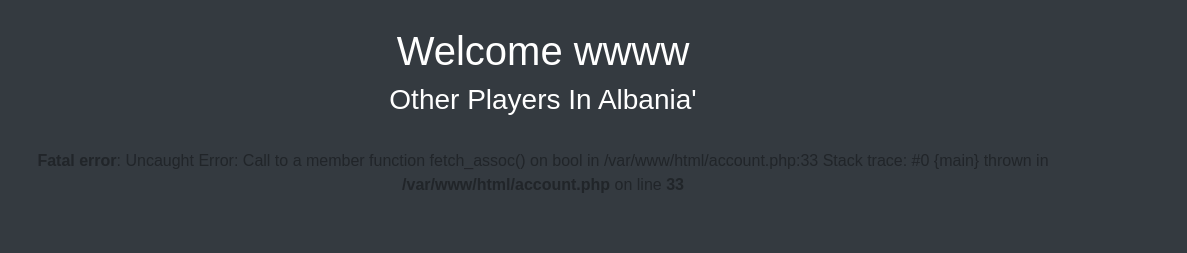
SQL Injection
I found a SQL Injection vulnerability in the country field, which returned some error messages.
This post is licensed under CC BY 4.0 by the author.